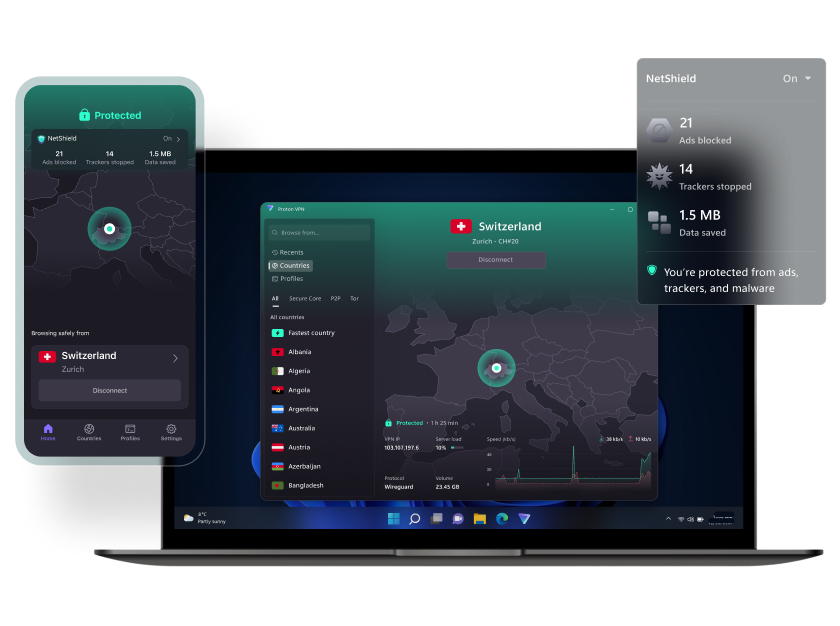
VPN security features
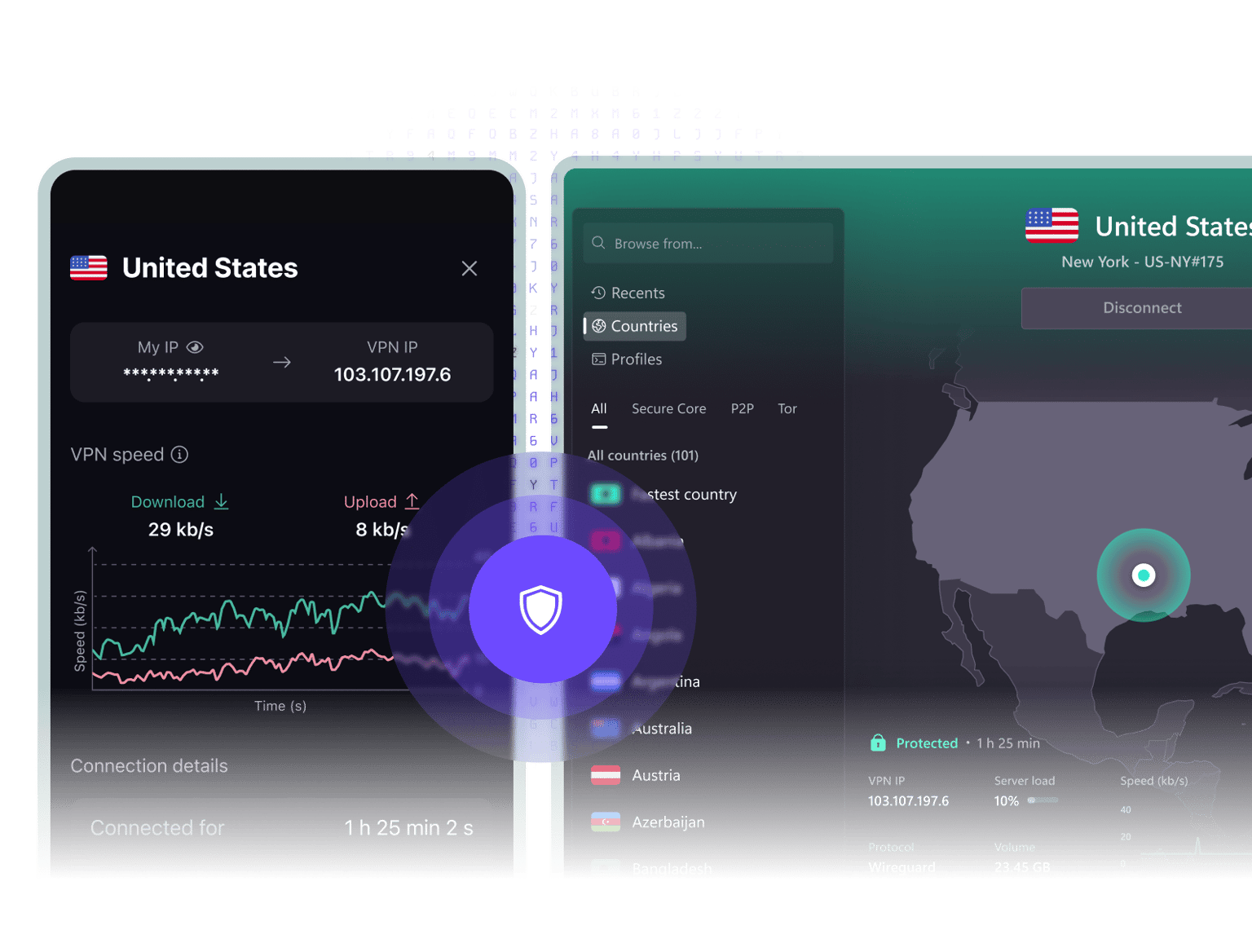
Browse the web with peace of mind. Proton VPN is a fast and reliable VPN service that protects your online privacy by hiding your real IP address.
Browse privately and securely
Avoid being tracked across the internet
Stop your browsing data from being sold to advertisers
With Proton VPN, you can also bypass censorship and access websites that might be blocked in your country.
Mask your IP
Proton VPN hides your real IP address, preventing the easiest and most accurate way for websites to track you online.

Swiss privacy
Switzerland has some of the strongest privacy laws in the world, is outside the EU, and isn't a member of any mass surveillance alliances.

No-logs policy
Proton VPN keeps no logs that can compromise your privacy and under Swiss law we can’t be obligated to start logging.

NetShield Ad-blocker
Block ads, trackers, and malicious scripts with NetShield Ad-blocker, our DNS filtering feature that prevents connections to unwanted domains.

DNS leak protection
Ensures your browsing history is never leaked to your internet service provider. Website address lookups are always done by Proton.

Tor over VPN
Connect to the Tor anonymity network and visit .onion sites from the convenience of your regular browser.

Alternative routing
Helps defeat censorship by routing your connection through third-party networks such as AWS when access to our servers is blocked.

Stealth
Defeat many forms of advanced censorship with Stealth, our custom obfuscation VPN protocol based on WireGuard tunneled over TLS.

Smart Protocol
Intelligently probes networks to discover the best VPN protocol configuration needed for optimal performance or to bypass censorship.
Open-source
Our apps are all open source, so anyone can check our code. We also commission regular independent audits so you can know they are secure.

Unblocking Content
Bypass government censorship and other content restrictions. Simply connect to one of our VPN servers located in a country that doesn’t censor the internet.

Unlimited Bandwidth
We place no restrictions on how much data you can use when connected to our service. Even if you’re on our Free plan.

Encryption
Our VPN protocols use proven open source encryption standards such as AES-256 and ChaCha20 at their strongest settings.

Strong Protocols
We use only the strongest and most cryptographically secure VPN protocols, such as WireGuard and OpenVPN.

Forward Secrecy
Forward secrecy generates a new encryption key for each session, keeping your browsing history secure even if a key is compromised in the future.
Two-factor authentication
Secure your Proton Account. Defeat hackers by proving your identity with two-factor authentication.

Secure Core
Prevent MITM and timing attacks with our high-security double VPN implementation where the first server is located only in a privacy-friendly country.

Kill switch & Always-on VPN
A kill switch in all our apps ensures your IP address is never exposed if the VPN connection is interrupted. Always-on VPN instantly reconnects you.

Independently audited
Our open source apps are regularly audited by security professionals. We openly publish the full results because we believe in transparency.

Full disk encryption
All our servers are bare-metal-only and use full disk encryption. So even if they are compromised, attackers can’t access your data.

VPN Accelerator
Improves speed performance by up to 400% when connecting to a VPN server over a long distance.

High-speed
Our network of high-speed VPN servers offers connections up to 10 Gbps.

Port Forwarding
Improve P2P performance and access local resources through your VPN connection with port forwarding.

Split Tunneling
Use split tunneling on Windows and Android to route some apps or IP addresses through the VPN tunnel while excluding others.
WireGuard®
A cutting-edge VPN protocol that is both fast and secure. Uses state-of-the art cryptographic primitives such as ChaCha20, and Diffie-Hellman elliptic curves.

Up to 10 devices
Use Proton VPN on up to 10 devices or browsers (via our browser extension) at the same time.

Easy to use
Simply open our app on any of your devices and tap the Quick Connect button to connect to the best server for your location.

Customer support / Live chat
If you have any questions, contact our friendly and professional support team. With a paid plan, Live chat support is available most hours.

Supported platforms
Proton VPN has open source apps for all major platforms — Windows, macOS, Linux, Android, Android TV, iOS and iPadOS, Chromebook, Chrome, and Firefox.

Streaming
Watch your favorite shows, movies, and sports events buffering-free when traveling away from home. Proton VPN supports many popular streaming services around the world.

Browser Extensions
Our browser extensions for Chrome and Firefox provide a convenient way to use Proton VPN and require no special permissions to install.

Servers & locations
Proton VPN runs over 15000 servers in 120 countries so you can always connect to the fastest or most useful location for your needs.

Mask your IP
Proton VPN hides your real IP address, preventing the easiest and most accurate way for websites to track you online.

Swiss privacy
Switzerland has some of the strongest privacy laws in the world, is outside the EU, and isn't a member of any mass surveillance alliances.

No-logs policy
Proton VPN keeps no logs that can compromise your privacy and under Swiss law we can’t be obligated to start logging.

NetShield Ad-blocker
Block ads, trackers, and malicious scripts with NetShield Ad-blocker, our DNS filtering feature that prevents connections to unwanted domains.

DNS leak protection
Ensures your browsing history is never leaked to your internet service provider. Website address lookups are always done by Proton.

Tor over VPN
Connect to the Tor anonymity network and visit .onion sites from the convenience of your regular browser.

Alternative routing
Helps defeat censorship by routing your connection through third-party networks such as AWS when access to our servers is blocked.

Stealth
Defeat many forms of advanced censorship with Stealth, our custom obfuscation VPN protocol based on WireGuard tunneled over TLS.

Smart Protocol
Intelligently probes networks to discover the best VPN protocol configuration needed for optimal performance or to bypass censorship.

Open-source
Our apps are all open source, so anyone can check our code. We also commission regular independent audits so you can know they are secure.

Unblocking Content
Bypass government censorship and other content restrictions. Simply connect to one of our VPN servers located in a country that doesn’t censor the internet.

Unlimited Bandwidth
We place no restrictions on how much data you can use when connected to our service. Even if you’re on our Free plan.

Encryption
Our VPN protocols use proven open source encryption standards such as AES-256 and ChaCha20 at their strongest settings.

Strong Protocols
We use only the strongest and most cryptographically secure VPN protocols, such as WireGuard and OpenVPN.

Forward Secrecy
Forward secrecy generates a new encryption key for each session, keeping your browsing history secure even if a key is compromised in the future.

Two-factor authentication
Secure your Proton Account. Defeat hackers by proving your identity with two-factor authentication.

Secure Core
Prevent MITM and timing attacks with our high-security double VPN implementation where the first server is located only in a privacy-friendly country.

Kill switch & Always-on VPN
A kill switch in all our apps ensures your IP address is never exposed if the VPN connection is interrupted. Always-on VPN instantly reconnects you.

Independently audited
Our open source apps are regularly audited by security professionals. We openly publish the full results because we believe in transparency.

Full disk encryption
All our servers are bare-metal-only and use full disk encryption. So even if they are compromised, attackers can’t access your data.

VPN Accelerator
Improves speed performance by up to 400% when connecting to a VPN server over a long distance.

High-speed
Our network of high-speed VPN servers offers connections up to 10 Gbps.

Port Forwarding
Improve P2P performance and access local resources through your VPN connection with port forwarding.

Split Tunneling
Use split tunneling on Windows and Android to route some apps or IP addresses through the VPN tunnel while excluding others.

WireGuard®
A cutting-edge VPN protocol that is both fast and secure. Uses state-of-the art cryptographic primitives such as ChaCha20, and Diffie-Hellman elliptic curves.

Up to 10 devices
Use Proton VPN on up to 10 devices or browsers (via our browser extension) at the same time.

Easy to use
Simply open our app on any of your devices and tap the Quick Connect button to connect to the best server for your location.

Customer support / Live chat
If you have any questions, contact our friendly and professional support team. With a paid plan, Live chat support is available most hours.

Supported platforms
Proton VPN has open source apps for all major platforms — Windows, macOS, Linux, Android, Android TV, iOS and iPadOS, Chromebook, Chrome, and Firefox.

Streaming
Watch your favorite shows, movies, and sports events buffering-free when traveling away from home. Proton VPN supports many popular streaming services around the world.

Browser Extensions
Our browser extensions for Chrome and Firefox provide a convenient way to use Proton VPN and require no special permissions to install.

Servers & locations
Proton VPN runs over 15000 servers in 120 countries so you can always connect to the fastest or most useful location for your needs.

Protect your internet
Strict no-logs policy
All apps are open source and audited
High-speed servers (up to 10 Gbps)
Based in Switzerland
30-day money-back guarantee
Strong encryption
We use only the strongest encryption to protect your internet connection. This means we encrypt all your network traffic with AES-256, exchange keys with 4096-bit RSA, and use HMAC with SHA384 for message authentication.

Forward secrecy
We have carefully selected our encryption cipher suites to include only ones with perfect forward secrecy.
This means that your encrypted traffic cannot be captured and decrypted later if the encryption key from a subsequent session gets compromised.
We generate a new encryption key each time you connect to the VPN, so a key is never used for more than one session.
Strong protocols
We use only the strongest encryption to protect your internet connection.
This means we encrypt all your network traffic with AES-256, exchange keys with 4096-bit RSA, and use HMAC with SHA384 for message authentication.
Full disk encryption
Although they store virtually no personally identifiable data, we protect all Proton VPN servers with full disk encryption.
This helps protect them against resource-intensive man-in-the-middle attacks that governments can perform.
Full disk encryption protects server certificates and all other configurations and software stored on our exit servers so that attackers cannot access any data, even if one was somehow compromised.
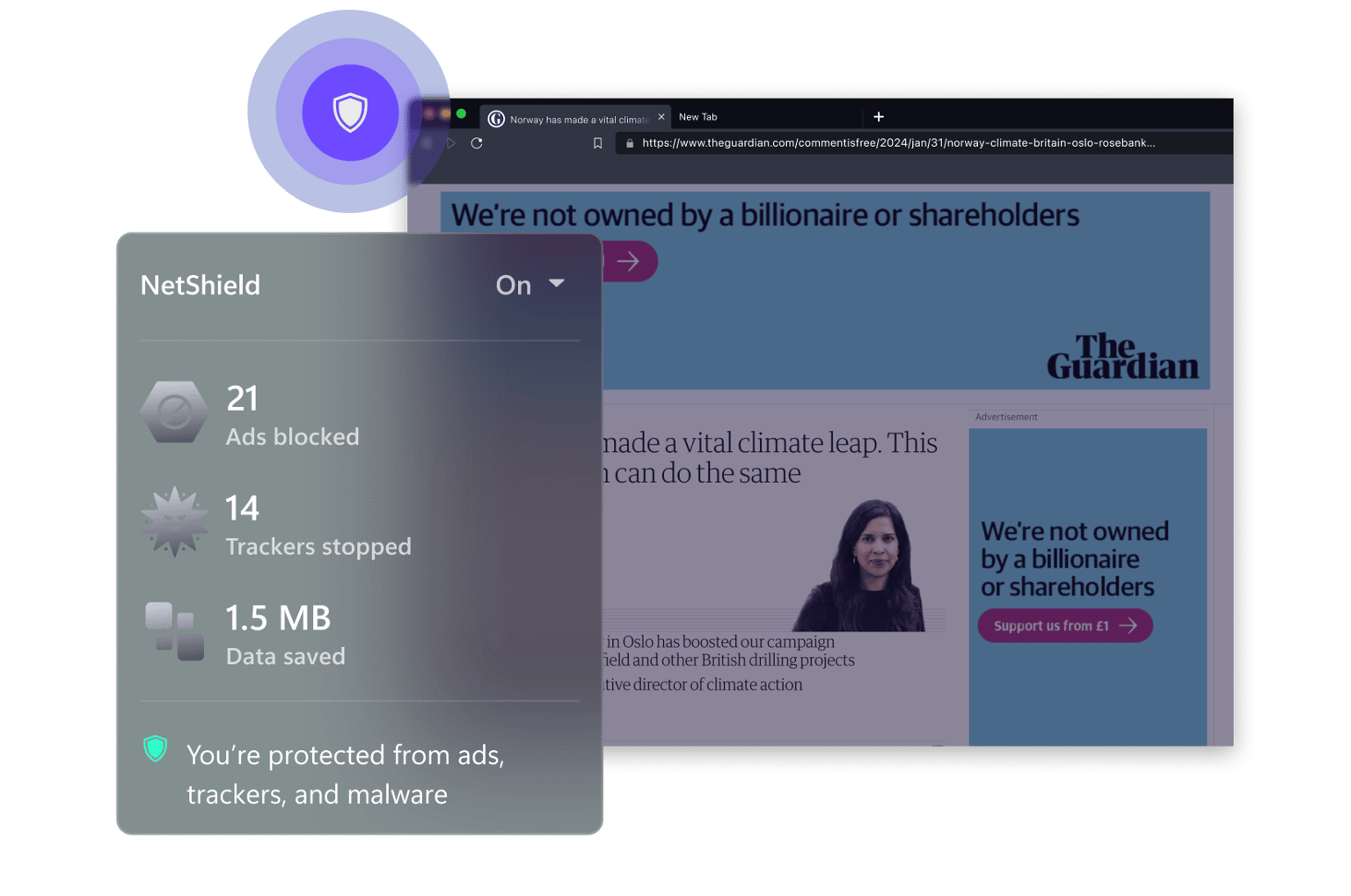
NetShield (Ad-blocker)
NetShield is a DNS filtering feature that protects you from malware, blocks ads, and prevents website trackers from following you as you surf the web.
As NetShield prevents your device from loading unnecessary content from the websites you visit, it also reduces the amount of data you need to load and increases your browsing speed.
VPN Accelerator
VPN Accelerator is a set of technologies unique to Proton VPN that can increase your VPN connection speeds by up to 400%.
VPN Accelerator dramatically increases performance by overcoming CPU limitations that affect how VPN protocols are processed, using advanced networking techniques to reduce latency, and redesigning VPN protocols themselves to reduce inefficiencies in their code.
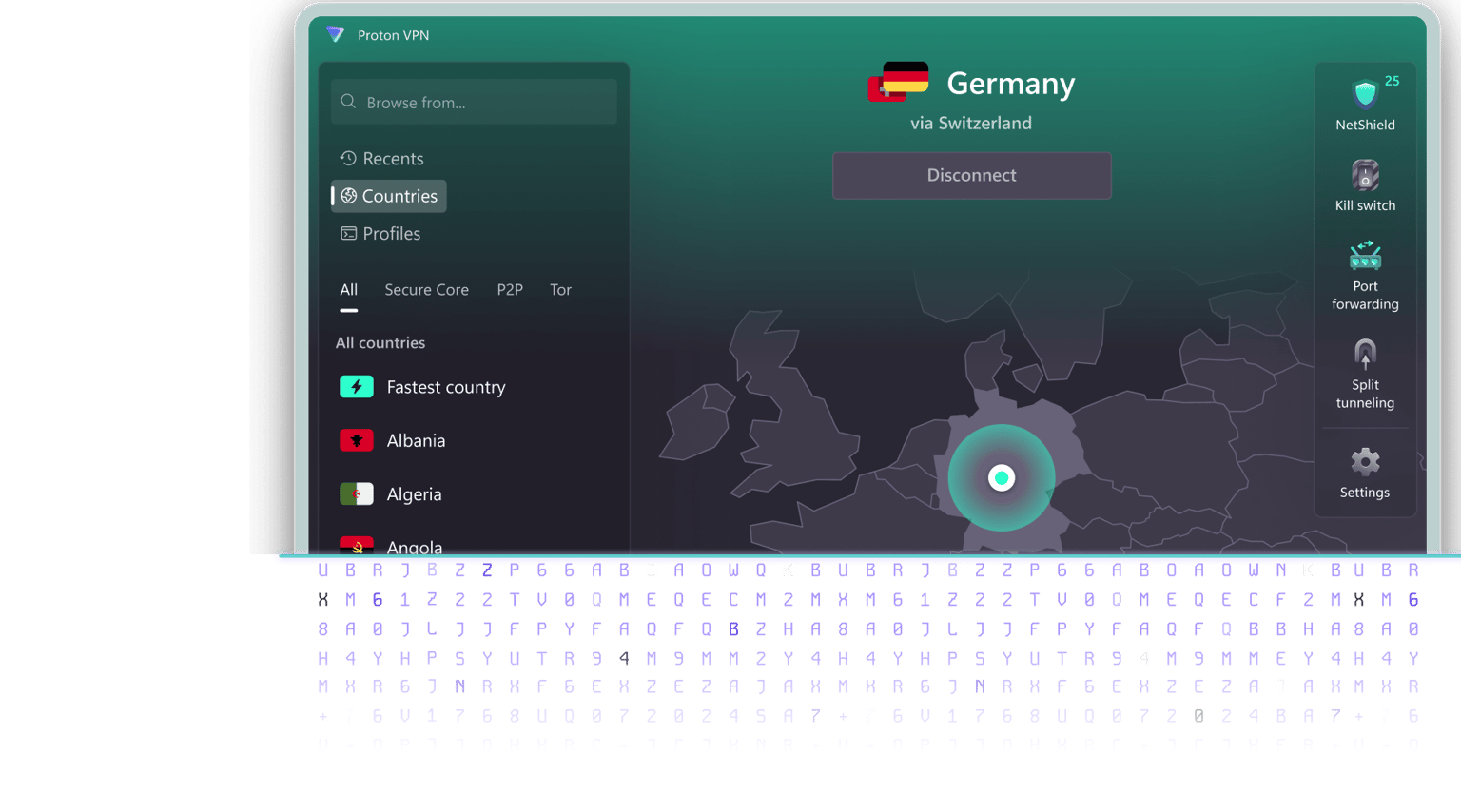
Secure Core
Proton VPN's Secure Core architecture gives you the unique ability to defend against network-based attacks. Secure Core protects your connection by routing your traffic through multiple servers before leaving our network.
This means an advanced adversary who can monitor the network traffic at the exit server will not be able to discover your true IP address or match your browsing activity to your IP address.
Secure Core servers are located in hardened data centers in Switzerland, Iceland, and Sweden, protected by strong privacy laws, and operated on our own dedicated networks.
Stealth
Proton VPN's Stealth is a unique VPN protocol that evades detection and allows you to bypass most firewalls and VPN blocking methods.
Unlike other VPN services, we’re deeply committed to advancing freedom and developing new technologies to beat censorship worldwide.
For instance, our alternative routing technology bypasses internet blocks by rerouting connections over other paths.
Similarly, our Stealth VPN protocol fights censorship by making your VPN traffic look like regular traffic, allowing you to access otherwise blocked information.
Swiss privacy
In addition to strong technical security, Proton VPN also benefits from strong legal protection. Because we’re based in Switzerland, Proton VPN is protected by some of the world's strongest privacy laws and remains outside US and EU jurisdiction.
This means that unlike a VPN provider based in a fourteen eyes country(new window), we cannot be coerced into spying on our users.
Physical security
We have gone to extreme lengths to protect Proton VPN's Secure Core servers to ensure their security.
Critical infrastructure in Switzerland is located at a high-security data center outside of Zurich that requires biometric access, and our infrastructure in Iceland resides in a secure former military base.
Our servers in Sweden are also located in an underground data center.
By shipping our own equipment to these locations, we ensure that our servers are as protected at the hardware level.
Trusted
It’s important you use a trustworthy VPN, which is why we are one of the only VPN companies transparent about exactly who runs our service.
Our team has a long track record in security, having previously built Proton Mail(new window) — the world's largest encrypted email service.
Whether challenging governments(new window), educating the public(new window), or training journalists(new window), we have a long history of fighting for privacy online and contributing to the open-source community(new window).
Open source
Founded by MIT and CERN scientists, Proton VPN believes in transparency and peer review. Our apps are 100% open source, so anyone can examine our code.
This transparency means that you can be confident that our apps do what they’re supposed to — and only what they’re supposed to.
You can see the code for all our apps on GitHub(new window).
Independently audited
Although being open source means anyone can check our code, Proton VPN also regularly commissions professional audits for all our full-release software from independent security experts.
Unlike some VPN companies, we publish the full results of these audits(new window) online for all to see.
No-logs policy
Under Swiss law, we are not obligated to save any user connection logs, nor can we be forced to perform targeted logging on specific users.
This allows us to ensure that your private browsing history stays private and cannot be turned over to a third party under any circumstances.
Our no-logs policy applies to all our users, including anyone using our free VPN.

DNS leak prevention
Proton VPN doesn't just protect your browsing traffic, we also protect your DNS queries.
By routing your DNS queries through the encrypted tunnel and not relying on third-party DNS providers, we ensure that your browsing activity cannot be exposed by leaks from DNS queries.
Kill switch and always-on VPN
Proton VPN applications offer built-in kill switch and always-on VPN features.
If you lose connection with the VPN server, kill switch blocks all network traffic, while always-on VPN automatically re-establishes your connection to a VPN server.
These features prevent a VPN server disconnect from inadvertently compromising your privacy by revealing your true IP address.
Tor over VPN
Proton VPN comes with built-in Tor support.
Through our VPN servers that are connected to Tor, you can route all of your traffic through the Tor anonymity network.
This provides a convenient way to access Onion sites with just a single click.
Anonymous
We respect your privacy, so we don’t require any personal identifying information to obtain a Proton VPN account.
You can sign up with a secure Proton Mail email account or a Proton Pass email alias(new window) to use Proton VPN without disclosing your identity.
High speed
For optimal performance, we use only high-speed servers.
All Proton VPN servers have a minimum of 1 Gbps bandwidth, and many of our servers utilize 10 Gbps connections.
This allows us to provide blazing-fast speeds even though we use only the strongest encryption, so you don’t have to sacrifice speed for security.
Easy to use
We understand that it’s important for security technology to be easy to use.
We have designed all Proton VPN applications to have a simple and intuitive user interface so that you can browse privately with a single click.
You can also create custom connection profiles that automatically protect your device whenever you connect to the internet.