Strong encryption for all
VPN security starts with strong encryption. Proton VPN protects your data using encryption ciphers that have proven to be robust.
- Encrypt your traffic with secure AES-256 or ChaCha20
- Protect yourself from future breaches with perfect forward secrecy
- Browse privately and safely
A reliable VPN with strong encryption
Proton VPN is built by the same team that created Proton Mail, the world’s largest encrypted email service. We have a long track record of implementing cybersecurity solutions, and we are committed to safeguarding your privacy with advanced encryption technologies.
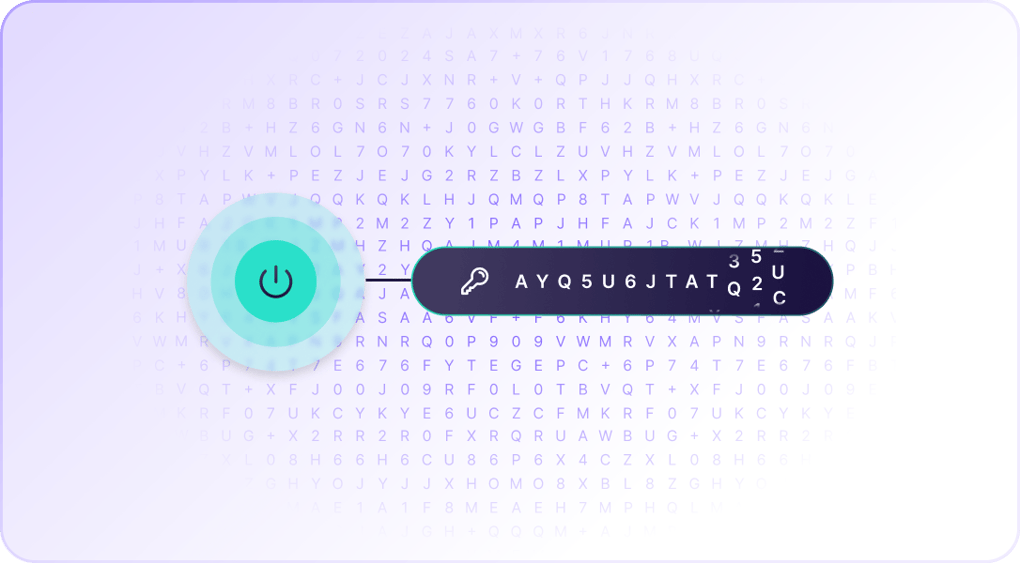
Encrypted network traffic
Proton VPN encrypts all network traffic using either AES-256 or ChaCha20, both of which are extremely secure.
VPN connections that use the OpenVPN or IKEv2 VPN protocol are secured with AES-256. While no encryption cipher is unbreakable, it would take even the most advanced computer billions of years to break AES-256 with a brute-force attack.
If you use the WireGuard® VPN protocol, your connection will be encrypted with ChaCha20, which is an advanced encryption cipher that is just as secure as AES-256 and slightly faster.
Perfect forward secrecy
Proton VPN only uses encryption ciphers and VPN protocols that support perfect forward secrecy. This means that each time you connect to our VPN, you generate a unique set of encryption keys. This way, even if a future VPN session is compromised, your past sessions will remain secure.
Secure key exchange
Proton VPN uses the Diffie-Hellman key exchange to securely generate session keys. The Diffie-Hellman is a secure approach that allows the server and the client to agree on a key, without ever communicating it.
Proton VPN is trusted, safe, and secure

Open source
Proton VPN apps are open source and available for inspection by the public. This enables us to take advantage of the entire cybersecurity community when it comes to finding and fixing any potential vulnerabilities and means anyone can ensure that our apps perform as advertised.
Independently audited
All Proton VPN apps have undergone a thorough, independent audit by leading cybersecurity firms. These audits are necessary so that people can see what an expert thinks of our apps’ security. You can find the results of all these audits on our website.
Based in Switzerland
Proton VPN is based in Switzerland, meaning your data is protected by some of the strongest privacy laws in the world. Switzerland is also not a part of any 5 Eyes, 9 Eyes, or 14 Eyes intelligence-sharing agreements, and any data requests from foreign governments must first be approved by the appropriate Swiss authority.
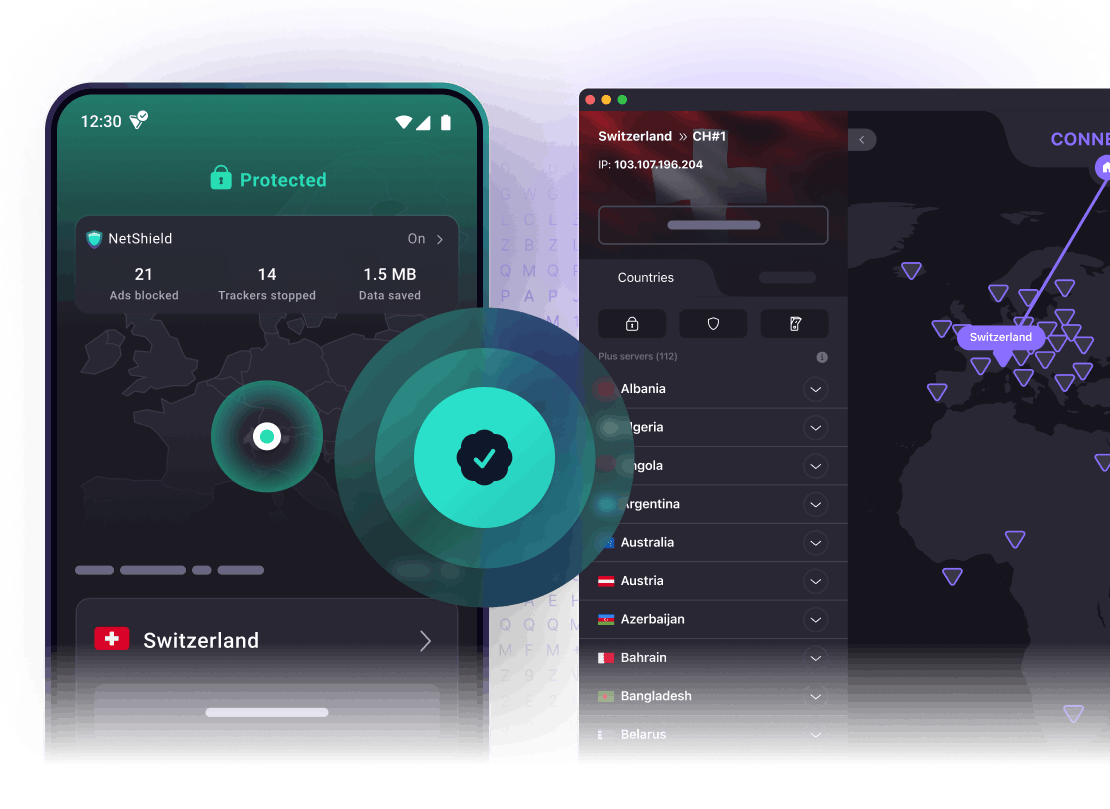
Access blocked content with a secure VPN
Secure Core VPN
Our hardened Secure Core servers are located in countries with strong privacy laws. Your online traffic is routed through one of these servers for added security.
NetShield Ad-blocker
Proton VPN’s NetShield Ad-blocker prevents online trackers and other malware from infecting your device.
DNS leak protection
Instead of relying on third-party DNS servers, Proton VPN runs our own DNS servers. Our apps also encrypt your DNS queries and include them in the VPN tunnel.
Kill switch
If your connection to the internet is interrupted, our kill switch terminates all traffic to prevent your IP address from being accidentally leaked.
No-logs VPN
We do not store any information about your online traffic, session lengths, or other metadata that could identify you.
VPN Accelerator
VPN Accelerator is a unique set of technologies that work on all our VPN protocols and can increase speeds by over 400%.
Global server network
We have over 15000 VPN servers with speeds up to 10 Gbps located in over 120 countries, so you can always access geographically restricted content.
Worldwide streaming
Watch your favorite TV shows on popular streaming sites like Netflix, Amazon Prime Video, Disney+, and more, no matter where you are.
Download a trustworthy VPN
- Strict no-logs policy
- From the makers of Proton Mail
- Audited by independent security experts
- Open source
- Used by journalists and activists