Silné šifrování pro všechny
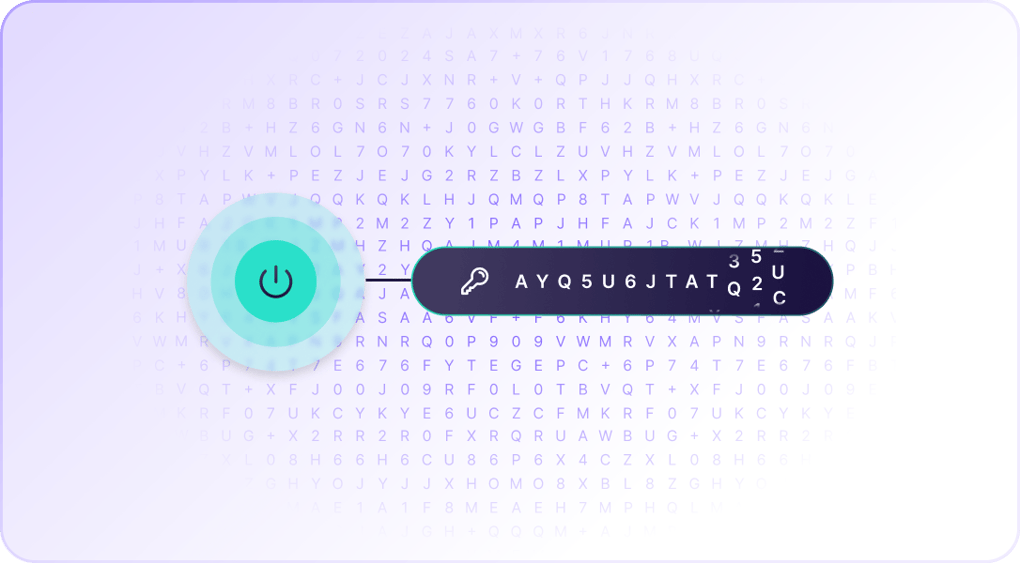
Zabezpečení VPN začíná silným šifrováním. Proton VPN chrání vaše data pomocí šifrování, které se osvědčilo.
- Šifrujte svůj provoz pomocí zabezpečeného šifrování AES-256 nebo ChaCha20
- Chraňte se před budoucími narušeními pomocí dokonalého utajení.
- Procházejte soukromě a bezpečně
Spolehlivá síť VPN se silným šifrováním
Proton VPN vytvořil stejný tým, který vytvořil Proton Mail, největší šifrovanou e-mailovou službu na světě. Máme dlouholeté zkušenosti s implementací řešení kybernetické bezpečnosti a zavázali jsme se chránit vaše soukromí pomocí pokročilých šifrovacích technologií.
Šifrovaný síťový provoz
Proton VPN šifruje veškerý síťový provoz pomocí AES-256 nebo ChaCha20, které jsou extrémně bezpečné.
Připojení VPN, která používají protokol OpenVPN nebo IKEv2 VPN, jsou zabezpečena pomocí AES-256. Žádné šifrování není neprolomitelné, ale prolomit AES-256 útokem hrubou silou by trvalo miliardy let i tomu nejvyspělejšímu počítači.
Pokud používáte protokol WireGuard® VPN, vaše připojení bude šifrováno pomocí ChaCha20, což je pokročilá šifra, která je stejně bezpečná jako AES-256 a o něco rychlejší.
Perfect Forward Secrecy
Proton VPN používá pouze šifry a protokoly VPN, které podporují dokonalé utajení. To znamená, že při každém připojení k naší VPN si vygenerujete jedinečnou sadu šifrovacích klíčů. Díky tomu zůstanou vaše předchozí relace VPN v bezpečí i v případě, že dojde ke kompromitaci budoucí relace VPN.
Bezpečná výměna klíčů
Proton VPN používá k bezpečnému generování klíčů relace výměnu klíčů Diffie-Hellman. Diffie-Hellman je bezpečný přístup, který umožňuje serveru a klientovi dohodnout se na klíči, aniž by si jej sdělovali.
Proton VPN je důvěryhodná, bezpečná a zabezpečená síť

Open source
Aplikace Proton VPN mají otevřený zdrojový kód a jsou k dispozici veřejnosti k nahlédnutí. Díky tomu můžeme při hledání a opravách případných zranitelností využít celou komunitu kybernetické bezpečnosti a kdokoli může zajistit, aby naše aplikace fungovaly tak, jak je inzerováno.
Nezávisle auditováno
Všechny aplikace Proton VPN prošly důkladným nezávislým auditem předních firem zabývajících se kybernetickou bezpečností. Tyto audity jsou nezbytné, aby lidé viděli, co si o bezpečnosti našich aplikací myslí odborník. Výsledky všech těchto auditů najdete na našich webových stránkách.
Sídlo ve Švýcarsku
Proton VPN sídlí ve Švýcarsku, takže vaše data jsou chráněna jedněmi z nejpřísnějších zákonů na ochranu osobních údajů na světě. Švýcarsko také není součástí žádných dohod o sdílení zpravodajských informací typu 5 Eyes, 9 Eyes nebo 14 Eyes a veškeré žádosti o data od zahraničních vlád musí nejprve schválit příslušný švýcarský úřad.
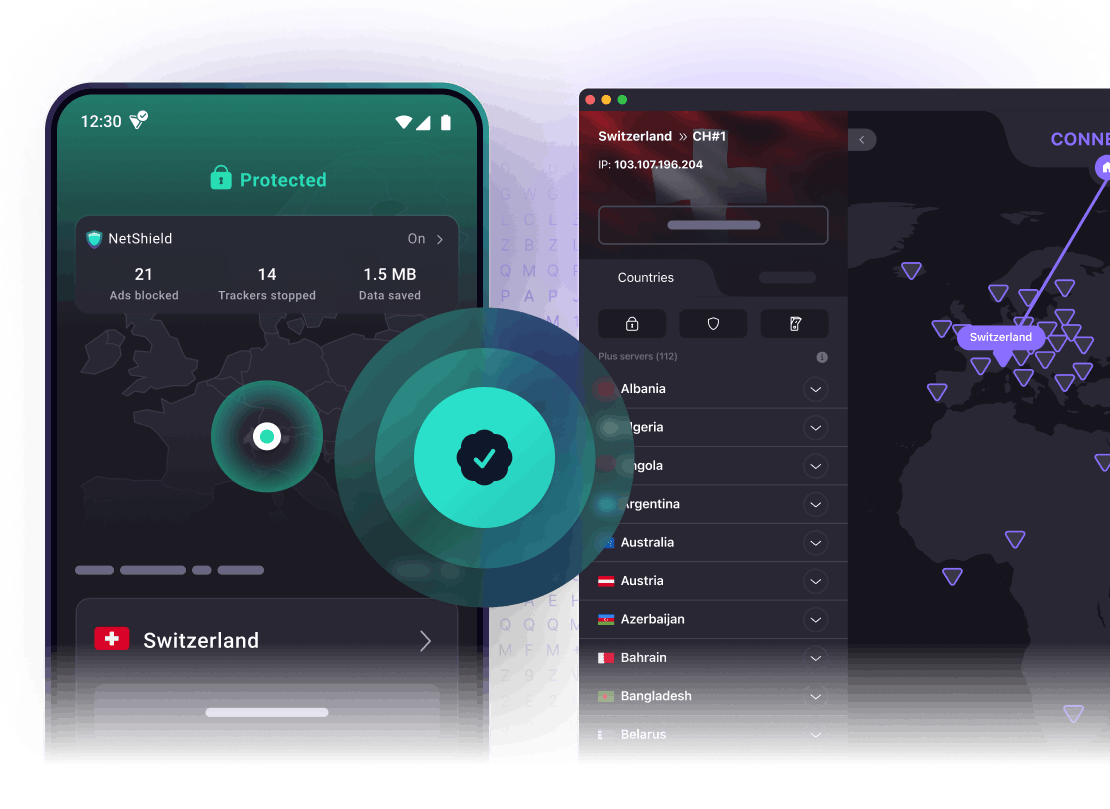
Přístup k blokovanému obsahu pomocí zabezpečené sítě VPN
Secure Core VPN
Naše zabezpečené servery Secure Core se nacházejí v zemích s přísnými zákony na ochranu osobních údajů. Váš online provoz je z důvodu vyšší bezpečnosti směrován přes jeden z těchto serverů.
Blokování reklam NetShield
Blokování reklam NetShield služby Proton VPN zabraňuje online sledovacím prvkům a dalšímu malwaru infikovat vaše zařízení.
Ochrana proti úniku DNS
Proton VPN nespoléhá na servery DNS třetích stran, ale provozuje vlastní servery DNS. Naše aplikace také šifrují dotazy DNS a zahrnují je do tunelu VPN.
Kill Switch
Pokud dojde k přerušení vašeho připojení k internetu, náš Kill Switch ukončí veškerý provoz, aby nedošlo k náhodnému úniku vaší IP adresy.
VPN bez logů
Neukládáme žádné informace o vašem online provozu, délce relace ani jiná metadata, která by vás mohla identifikovat.
VPN Accelerator
VPN Accelerator je jedinečná sada technologií, která funguje na všech našich protokolech VPN a dokáže zvýšit rychlost o více než 400 %.
Globální síť serverů
Máme více než 15000 serverů VPN s rychlostmi až 10 Gb/s ve více než 120 zemích, takže máte vždy přístup ke geograficky omezenému obsahu.
Celosvětové streamování
Sledujte své oblíbené televizní pořady na oblíbených streamovacích webech, jako je Netflix, Amazon Prime Video, Disney+ a další, ať jste kdekoli.
Stáhněte si důvěryhodnou VPN
- Přísná politika žádných logů
- Od tvůrců aplikace Proton Mail
- Auditováno nezávislými bezpečnostními experty
- Open source
- Používají novináři a aktivisté