Proton VPN and IPv6 support
There are two versions of the Internet Protocol in common use today. The older Internet Protocol version 4 (IPv4) is still by far the most commonly used standard, but thanks to the explosion of internet-capable devices that have become available over the last few years, IPv4 addresses are running out(new window).
The IPv6 standard was created to solve this problem. It uses 128-bit internet addresses, expanding the maximum available number of IP addresses to 2^128 (around 340 undecillion(new window)), more than enough to keep us going for the foreseeable future.
While most of the internet continues to use the IPv4 protocol, there are ISPs that provide support for IPv6 as well. In fact, there are now some ISPs that only support IPv6. This trend toward IPv6 is only likely to continue.
Proton VPN and IPv6
To address this issue and support our community, Proton VPN is transitioning to offering full IPv6 support. We currently support IPv6 on the following platforms:
To use IPv6:
- You must use a VPN client that supports IPv6 (currently our browser extension. Android app, and Linux app)
- You must connect to a VPN server that supports IPv6
Note that for now, while data inside the VPN tunnel is routed using IPv6, the initial connection to the VPN server is made over IPv4.
Approximately 80% of our servers now support IPv6. To see if a server you’ve connected to supports IPv6, visit test-ipv6.com(new window).
How to turn on IPv6 support
IPv6 support is automatically turned-on for our Linux apps, with no user-configuration required. It’s also turned-on by default on our Android and Linux apps. To change this setting on:
Android
Open the app and go to ⚙Settings → Connection → Advanced Settings → IPv6 to toggle the switch on (or off).

Linux
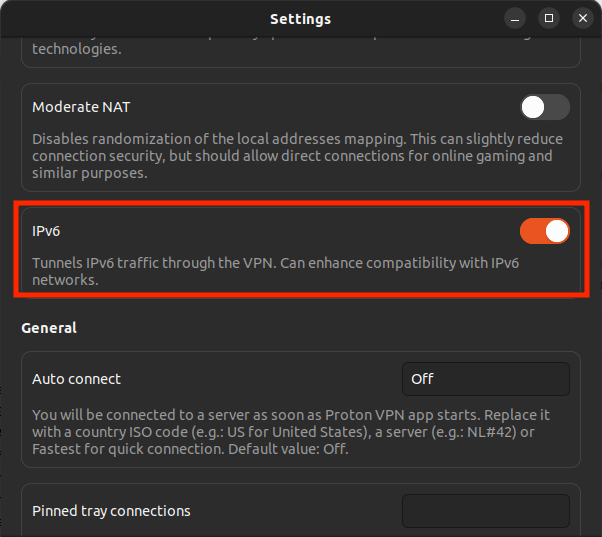
Open the app and go to Menu (⏷) → Settings → Connection → IPv6 and toggle the switch on (or off).
Other platforms
We’re working to bring full IPv6 support to all our apps. Until this happens, IPv6 is turned off on our Windows, macOS, and iOS/iPadOS apps to ensure that your IPv6 address can’t be accidentally exposed to servers on the internet. And unless you use an IPv6-only ISP (which is still very rare), using IPv4 instead of IPv6 doesn’t impact your internet experience.
If you wish, you can manually turn off IPv6 on Windows, macOS, and Linux, but this should only be necessary if you’re using third-party VPN apps (not our official apps).













