Tor is a powerful privacy tool, but you may not want to use Tor all by itself. Learn why you may want to connect to Tor over a VPN.
When you connect to the Internet, especially if you’re using public WiFi, there’s a good chance people are watching you. Hackers, government spies, and the websites you visit can find out your IP address, your location, the pages you visit, and even the information you send and receive over the network. But there are two easy-to-use technologies that can protect you: Tor and VPN.
This article explains what Tor is and why you might want to consider using Tor over VPN than Tor by itself.
What is Tor and how does it work?
Tor is a free software program developed by The Tor Project(new window), a nonprofit organization based in Massachusetts. Tor allows users to anonymize their Internet traffic, making it a useful tool for journalists and human rights defenders who may be targeted online. Today a lot of people use Tor every day, from victims of domestic violence(new window) to high-profile whistleblowers and activists. Edward Snowden used a combination of Tor and PGP(new window) to communicate classified information about the NSA with The Guardian.
With Tor, you can also connect to hidden services known as onion sites, which are only accessible via the Tor network. Proton Mail, for instance, has its own onion site(new window). These can be useful for bypassing regional censorship(new window).
When you connect to the Tor anonymity network, your Internet connection is encrypted and bounced among multiple Tor servers operated by volunteers around the world. Unless the entire Tor network (or a significant fraction) of it is being monitored, a third party will not be able to identify the real IP address of the Tor user. Websites that you visit only see the IP address of the Tor exit node (the last node in the Tor network that your traffic passes through), and not your actual IP.
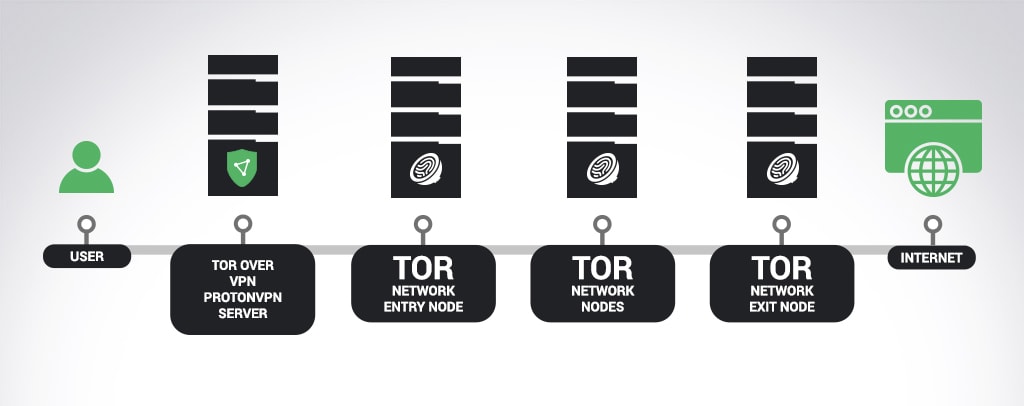
Using Tor in combination with a VPN
A VPN, or virtual private network, establishes an encrypted tunnel between your device and the VPN server, concealing your true IP address and your activities from your Internet service provider (ISP) and any hackers or spies who might be monitoring the network. (Follow these links to learn more about how VPNs work and the benefits of using one.)
There are a few advantages to using Tor in combination with VPN. Using Tor with a VPN gives you an extra layer of privacy because the VPN encryption prevents the Tor entry node (the Tor server where you enter the hidden network) from seeing your IP address. A compromised Tor entry node is one common way for an attacker to try to break Tor’s anonymity. The VPN will encrypt some Internet traffic that Tor does not support, like ICMP traffic. It also prevents your ISP from knowing you are connecting to Tor.
Additionally, using Tor over VPN gives you access to onion sites like those operated by Proton Mail(new window), Facebook(new window), and The New York Times(new window), among many others(new window).
However, there are also disadvantages of using Tor over VPN. While Proton VPN supports both TCP and UDP traffic, Tor only supports TCP. (For instructions on how to configure Proton VPN to use TCP, click here.) You must also use a VPN service you trust because the VPN server will be able to see your true IP address. VPN trust means using a reputable VPN service that does not keep logs of your activity and does not serve ads or malware. It’s also important to know what a VPN can and cannot protect against. Proton VPN is the only VPN service that provides this information in a comprehensive overview of our threat model.
Proton VPN and Tor
There are a number of ways to use Tor. For example, you can download the Tor browser(new window), use a Tor plugin, or run a Tor operating system(new window) on your machine. Proton VPN offers a simpler way of connecting to the Tor network as a convenience for paid users. With a single click, you can gain access to onion sites and to the privacy benefits of the Tor network.
At Proton VPN, we implement Tor over VPN, meaning your Internet traffic is encrypted all the way through the Tor network, and your true IP address is never revealed to your ISP or to any Tor nodes.
To start using Proton VPN, click the signup button below (it’s free). Or if you already have a free account, consider upgrading to take advantage of our advanced security features. When you’re ready to connect to Tor via Proton VPN, you can find step-by-step instructions here.
Sign Up UpgradeYou can follow us on social media to stay up to date on the latest Proton VPN releases:
Twitter(new window) | Facebook(new window) | Reddit(new window)







