How to set up SSO for Proton VPN using Okta
Our Proton VPN for Business plans support single sign-on (SSO) as an early access (beta) feature. In this article, we look at how to set up SSO on Proton VPN for Business using Okta as your identity provider (IdP).
SSO for Proton VPN supports the following features:
- IdP-initiated SSO
- Service provider (SP) initiated SSO
For more information on these, please visit the Okta Glossary(new window). In this support article, we’ll look at:
- How to configure Proton VPN on Okta
- How to configure SAML SSO on your Proton VPN for Business account
- How to add SSO users in Okta
How to set up SSO for Proton VPN using Okta
Proton VPN currently supports SSO using Security Assertion Markup Language(new window) (SAML) 2.0, an XML(new window)-based open standard for transferring data that verifies your identity between an IdP and SaaS applications.
Before you start, you’ll need the following:
- A Proton VPN for Business account with Administrator privileges
- An account with Okta(new window).
Once you have an account with Okta, you’ll need to configure it for Proton VPN. You can then configure SAML on your Proton VPN for Business account.
Here’s what we’ll cover next:
- How to configure Proton VPN on Okta
- How to configure SAML SSO on your Proton VPN for Business account
- How to add SSO users in Okta
- How to use SSO to sign in to Proton VPN for the first time
- How to use SSO to sign in to Proton VPN
- How to manage SSO for Proton VPN
- Troubleshooting
How to configure Proton VPN on Okta
Option 1. Use the official integration
This option uses the official Proton VPN Okta SSO application, and is the recommended option if you don’t plan to use SCIM. If you do plan to use SCIM, for now, you’ll need to create your own Proton VPN Okta SSO application instead (see option 2 below).
1. Log in to your Okta account(new window) and go to Applications → Browse App Catalog.
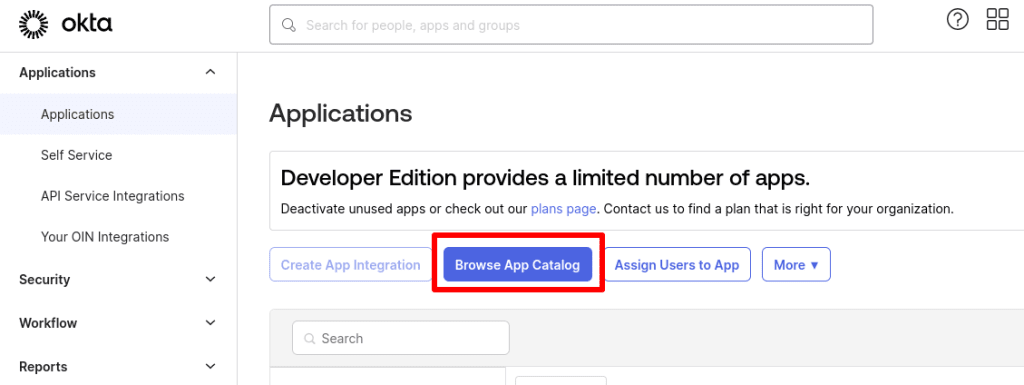
2. Search for Proton VPN SAML.
3. Click Add Integration.
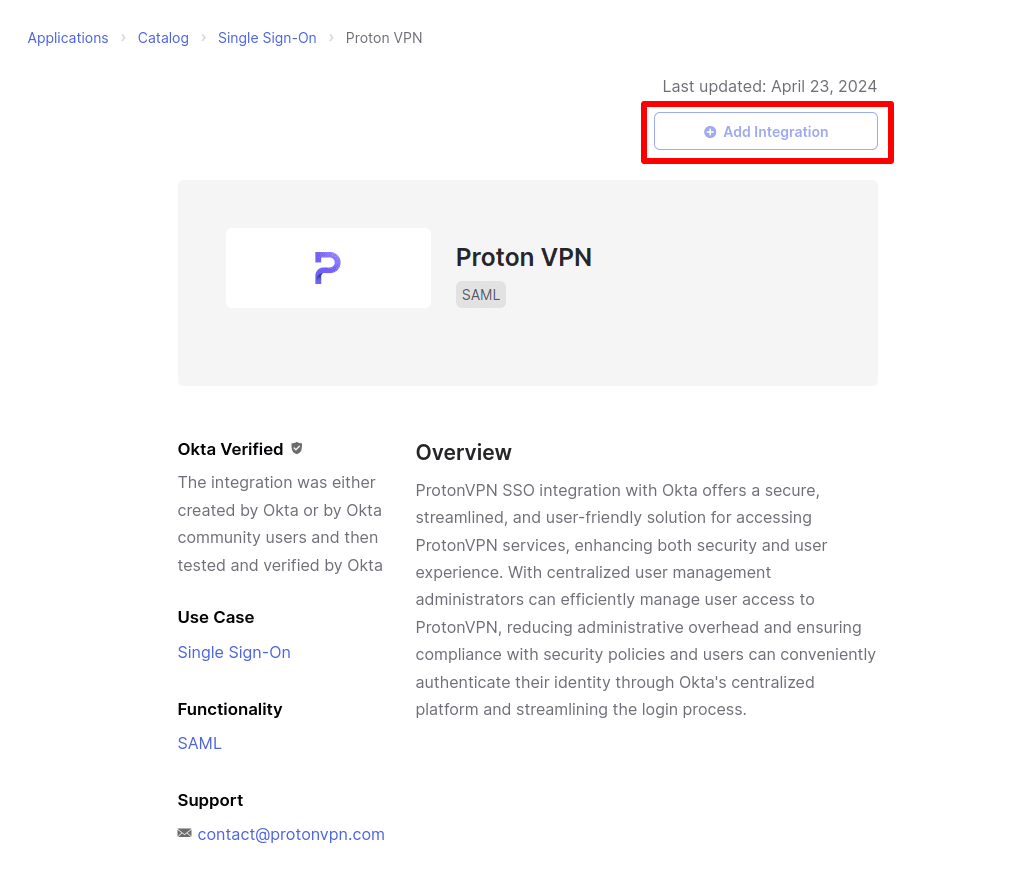
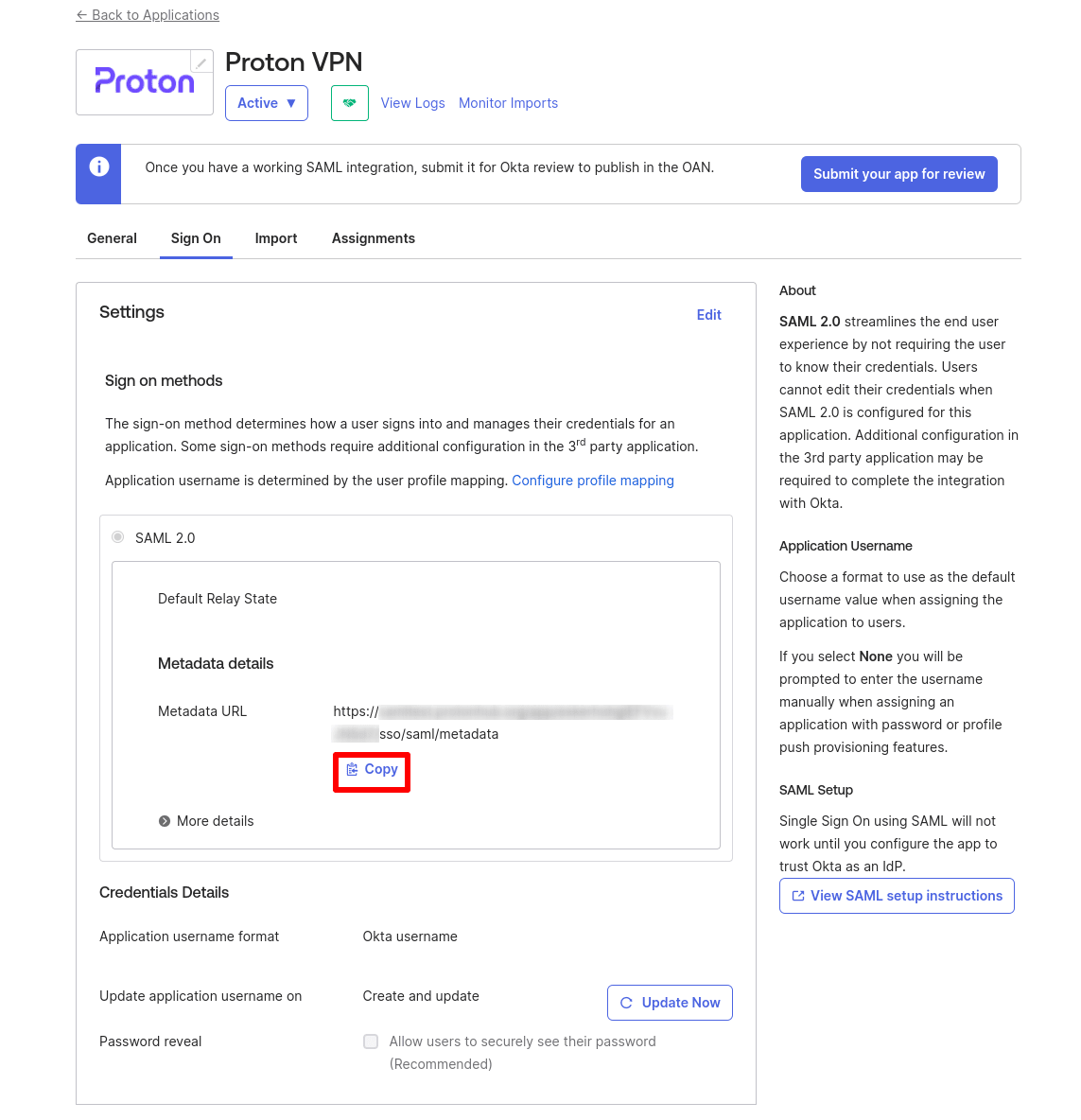
4. You’ve now created a SAML integration for Proton VPN. Go to SAML 2.0 → Metadata details → Metadata URL → Copy.
Option 2. Create your own integration
If you want to use SCIM, you’ll need to create your own Proton VPN Okta SSO application.
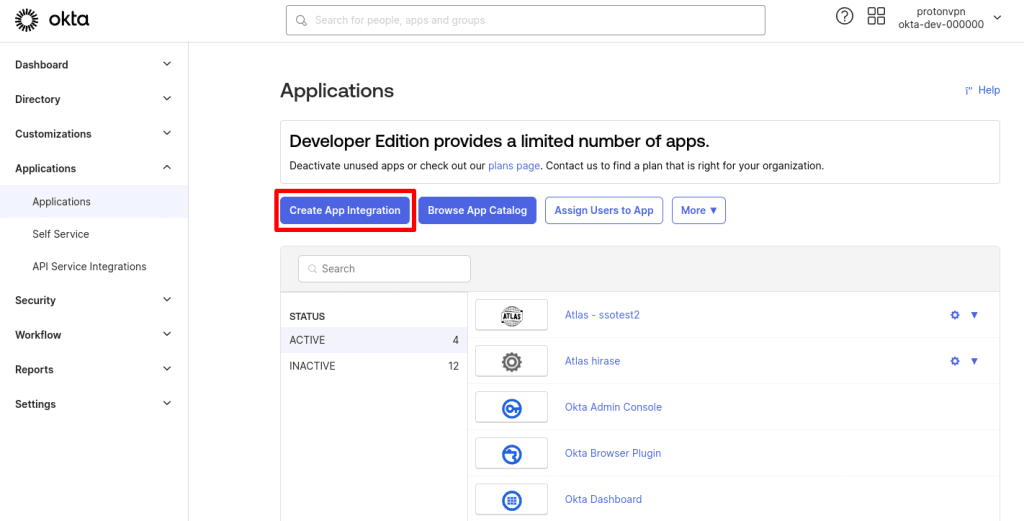
1. Sign in to your Okta account(new window) and go to Applications → Create App Integration.
2. Select SAML 2.0 and then click Next.
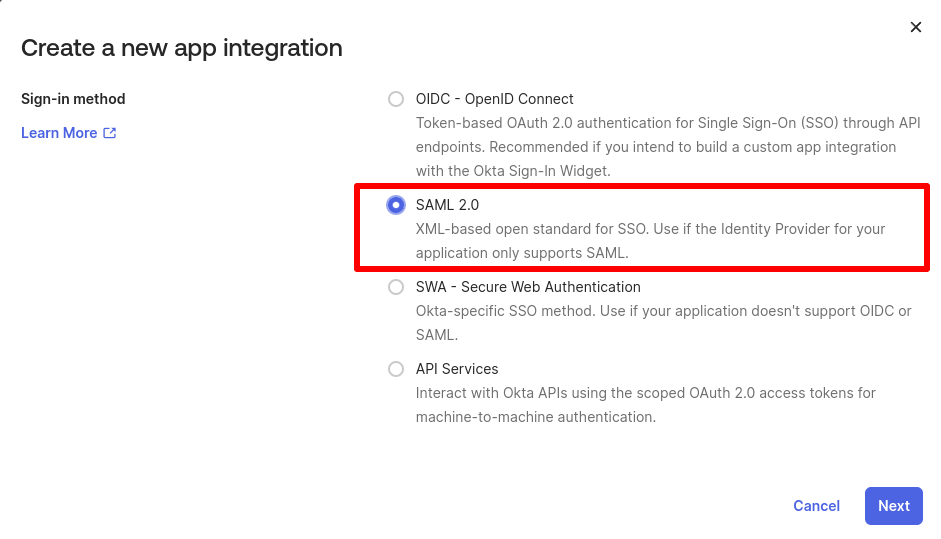
3. Give your app a name and upload a logo for it (optional). Click Next when you’re ready.
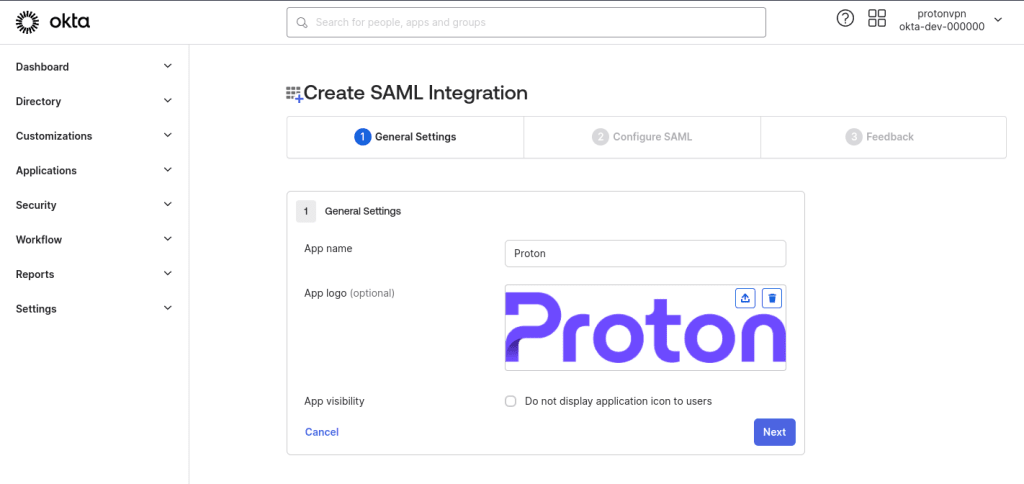
4. Under section A SAML Settings → General, enter the following information:
- Single sign-on URL: https://sso.proton.me/auth/saml(new window)
- Audience URI (SP Entity ID): https://sso.proton.me/sp(new window)
- Name ID Format: Select EmailAddress from the dropdown menu
Now scroll down to the bottom of the page and click Save.
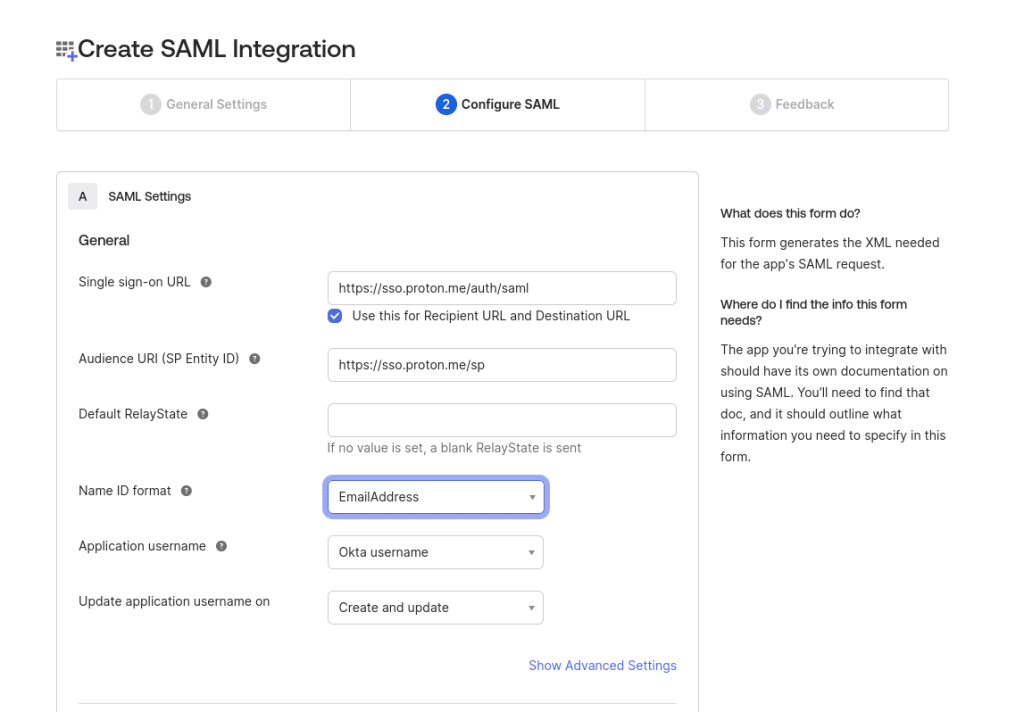
5. Answer the question Help Okta Support understand how you configured this application as best describes the use of your app. This answer is simply feedback for the Okta support team, and doesn’t affect your setup in any way. Click Finish when you’re ready.
6. You’ve now created a SAML integration for Proton VPN. Go to SAML 2.0 → Metadata details → Metadata URL → Copy.

How to configure SAML SSO on your Proton VPN for Business account
1. Log in to your Proton VPN for Business administrator account at account.protonvpn.com and go to ⚙ → Single sign-on → SAML authentication → Configure SAML.

2. Add your organization’s domain name and click Add domain.
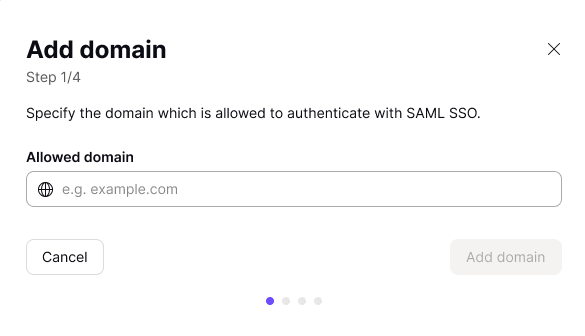
3. Verify the domain for your identity provider. To do this, log in to your domain provider’s web portal and enter the DNS TXT record(new window) displayed on this screen.
Back at account.protonvpn.com, click Continue once you’ve done this.
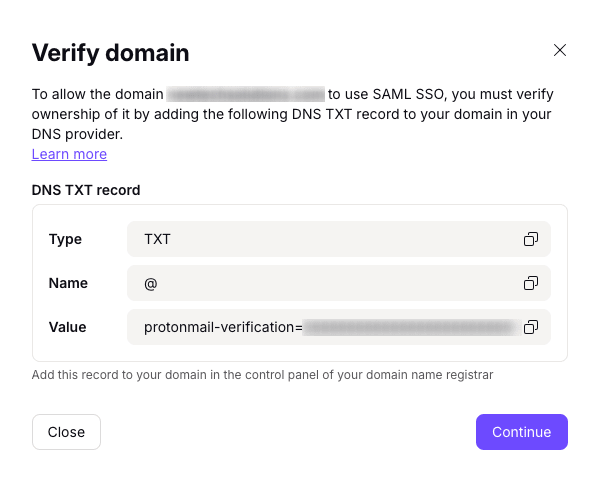
4. A screen will show you the endpoints needed by Okta. However, this has already been automatically configured in the official Proton VPN SSO application for Okta that you set up above. So just click Continue.
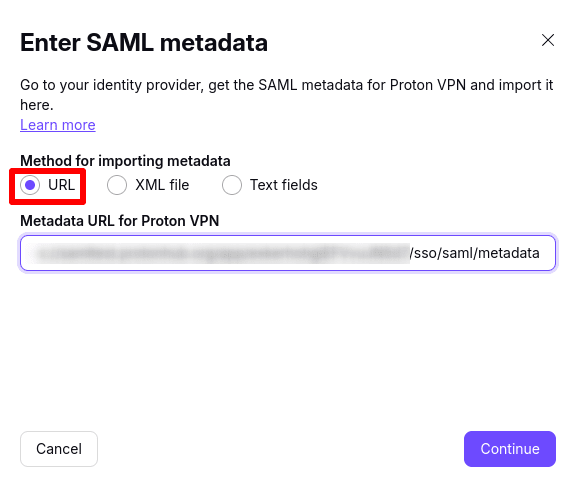
5. Import the SAML metadata for Proton VPN from Okta. Select URL and paste in the URL you copied in step 4 of Configure Proton VPN on Okta (above). To find this page again in your Okta console, go to Applications → Applications → [the application you just created] → Sign-on tab.
Click Done when you’re ready.
SSO using Okta should now be configured on your Proton VPN for Business account. Click See details for an overview of your SSO settings.

How to add SSO users in Okta
Before your users can sign in to our organization using SSO, you’ll need to add them in Okta.
1. Log in to your Okta account(new window) and go to Directory → People → Add person.
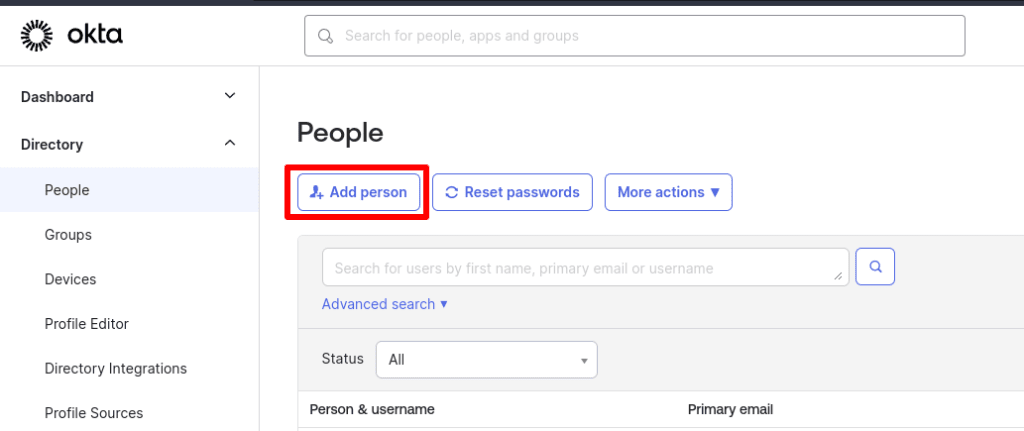
2. Go to User type and select User from the dropdown menu. Now fill in their details. The username and primary email address must use your organization’s domain. Click Save or Save and Add Another when you’re done.
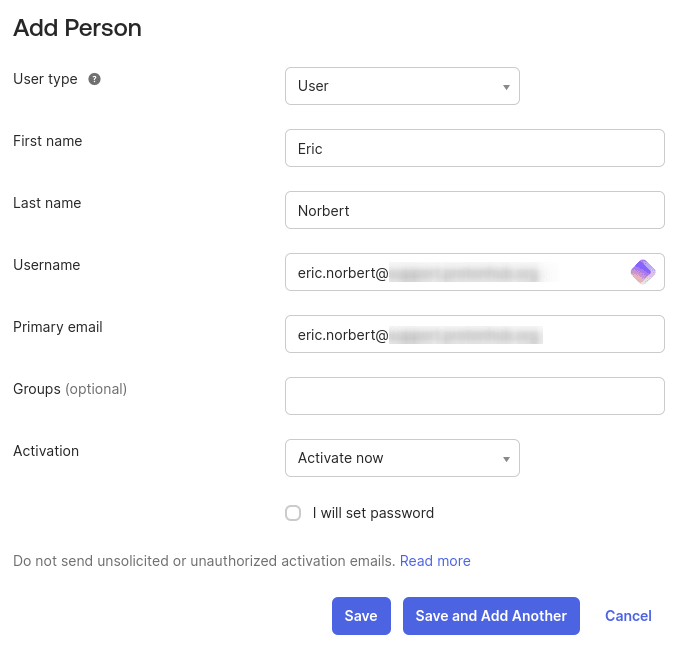
3. When you’re done, go to Directory → People to see a list of users you’ve added. Click on a name.
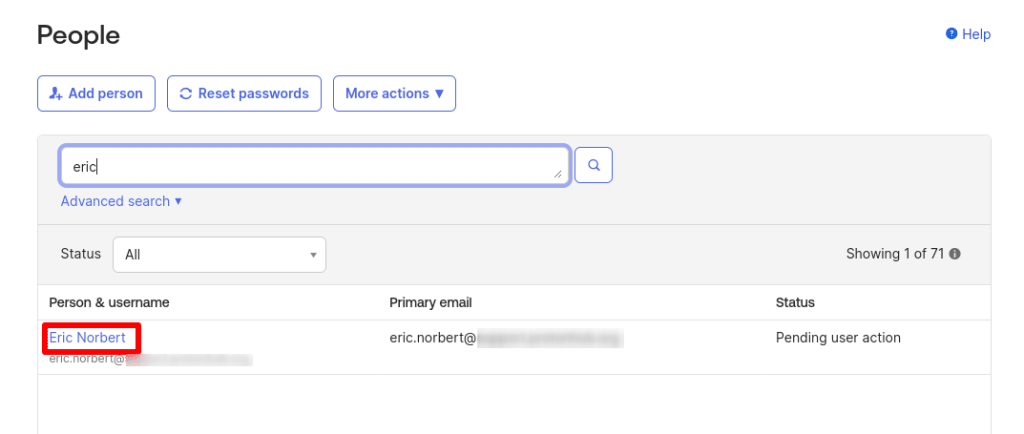
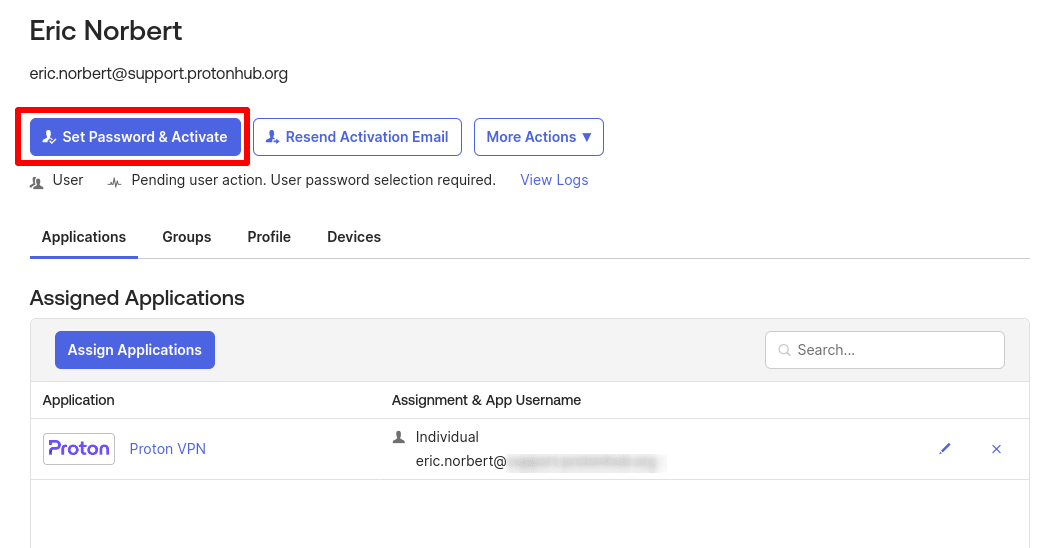
4. In the Applications tab, click Assign Applications.
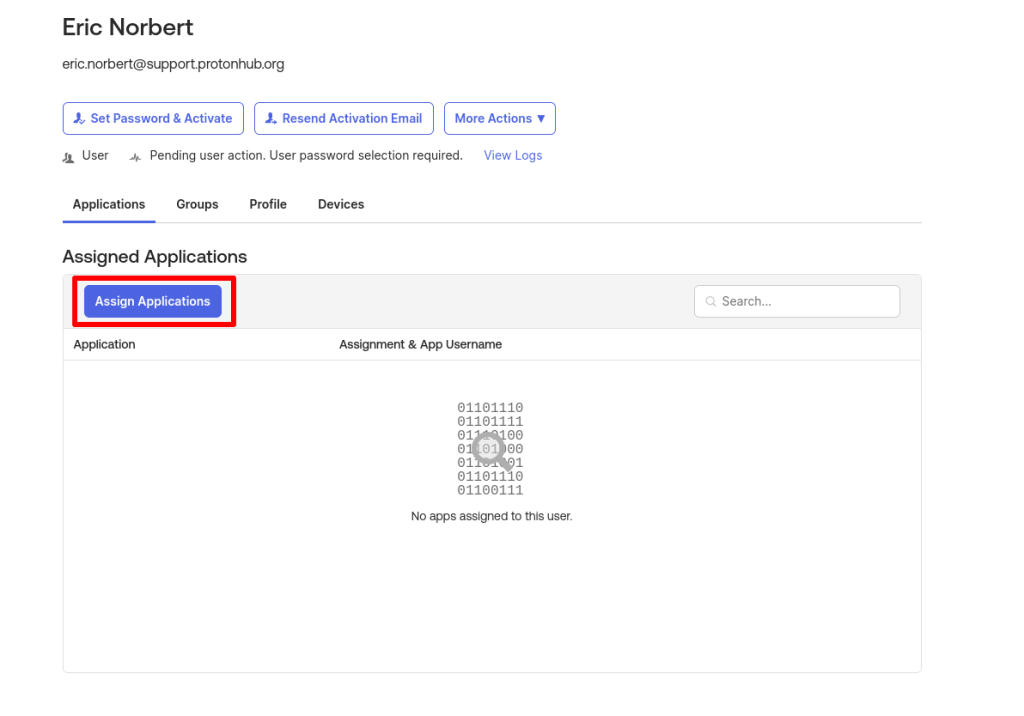
5. Click Assign next to the Proton VPN application you created above., followed by Done.
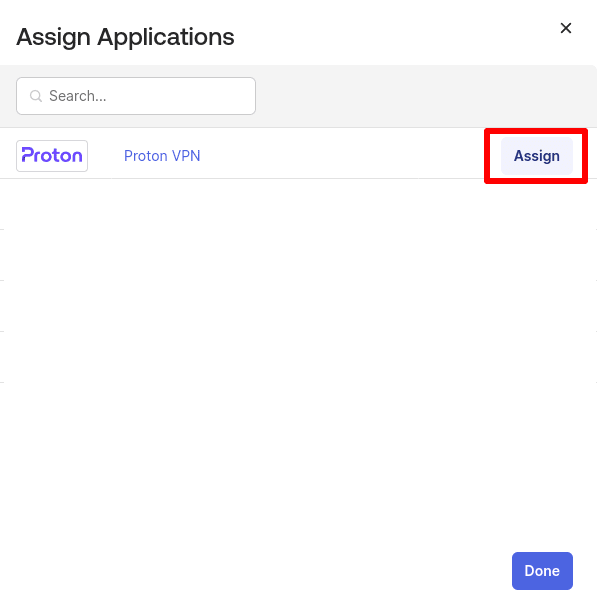
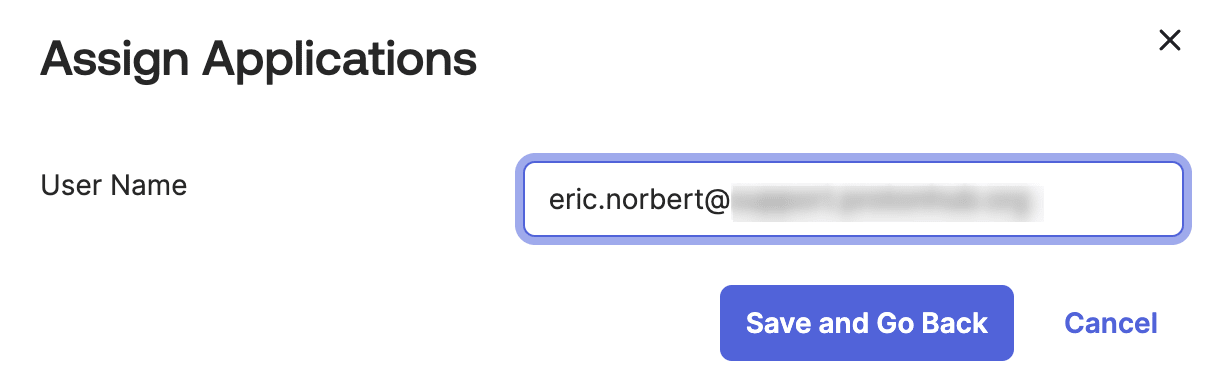
6. Re-enter the user’s User Name, then click Save and Go Back.
7. Click Done.
8. Repeat the process for as many SSO users as you like. When you’re done, click Set Password & Activate.
9. At the confirmation screen, click Set Password & Activate.

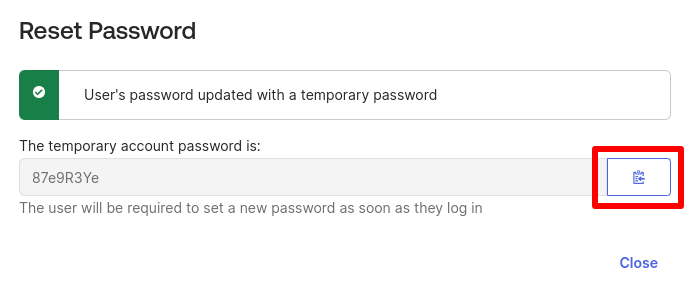
10. Create a temporary password and make a note of it (there’s a copy button to copy it to your device’s clipboard). Each new user will use this password just once to sign in to Proton VPN via SSO for the first time. Click Close when you’re ready.
How to use SSO to sign in to Proton VPN for the first time
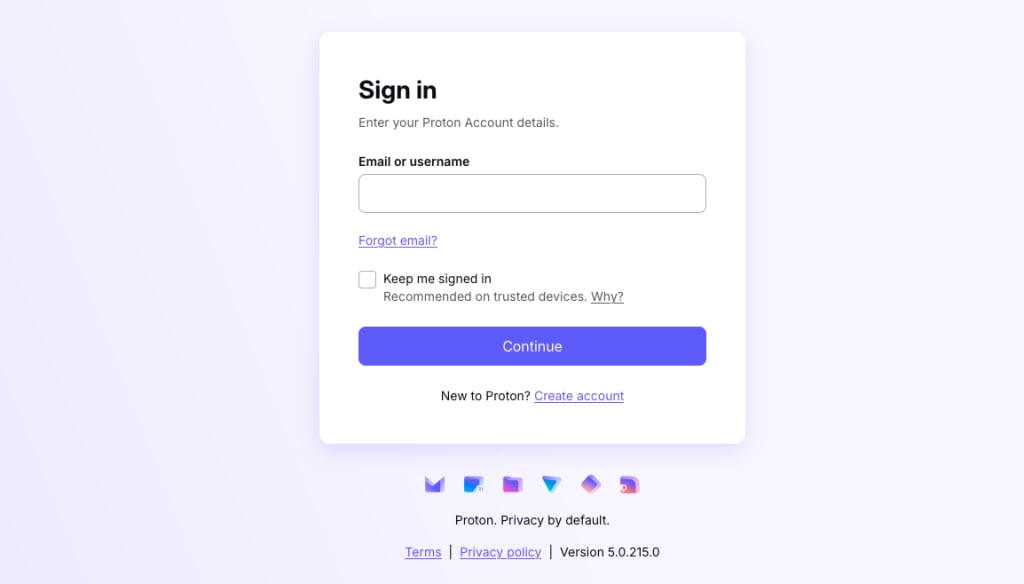
As a user with a new SSO account configured on Microsoft, go to account.proton.me/vpn . Enter your email address (as configured on Okta) and click Continue.
2. We’ll detect that you’re using a Okta SSO password and automatically direct you to the Okta sign-in page. Enter your temporary SSO password (this will be supplied by your manager, or see steps 9 and 10 in the “How to add SSO users in Okta” section above), and click Sign in.
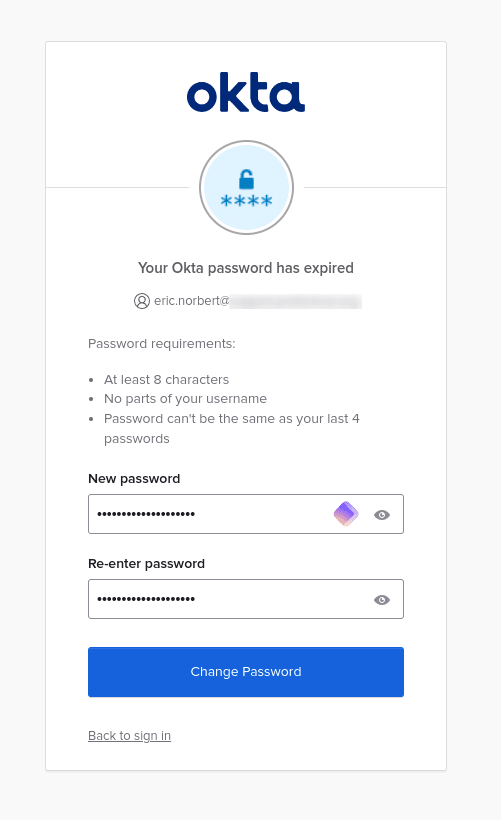
4. You’ll now be asked to create a new permanent password (that will replace the single-use temporary password you were provided). Once you’ve done this, click Change password and you’ll log in to your Proton Account.
How to use SSO to sign in to Proton VPN
As a user, once you’ve created your SSO password, you can use it (together with your company username) to sign in to Proton VPN apps. To do this, click or tap Sign in with SSO on any Proton VPN login screen.
How to manage SSO for Proton VPN
Your organization’s users can now log in to Proton VPN apps using the username and password they created (see above). To view which users can do this, log in to your Proton VPN for Business administrator account at account.protonvpn.com and go to Organization → All users. Note: SSO users will only appear here once they have signed in at least once.
To manage access to your Proton VPN organization, log in to your identity provider.
You can manage individual users using the dropdown menu in the Edit column of the user you wish to manage SSO access for.

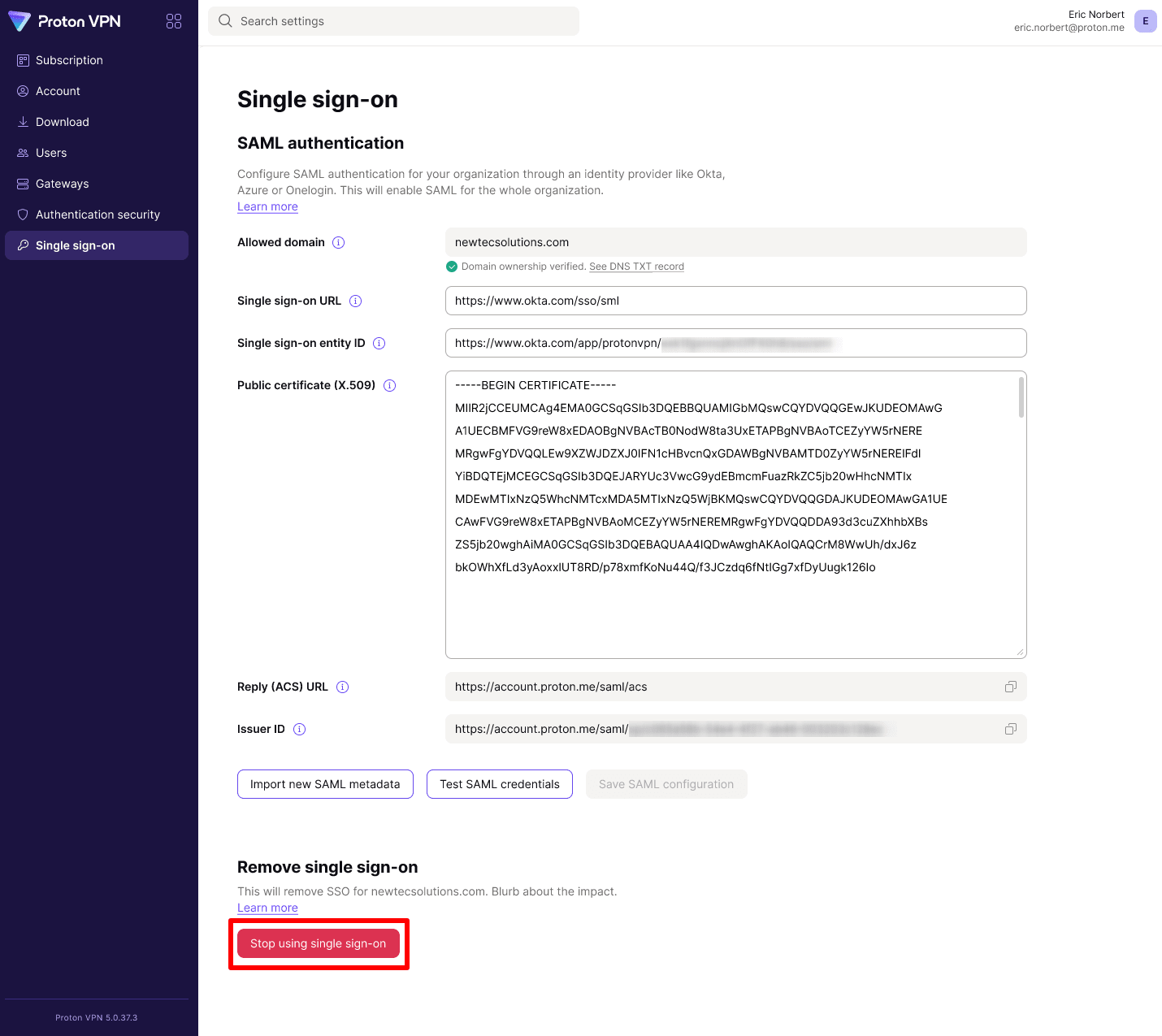
To turn off SSO for your whole organization, go to Single sign-on → Remove single sign-on → Stop using single sign-on.
Please note that doing this deletes all configurations and users associated with your domain. We therefore strongly recommend against turning off SSO for your whole organization.
Troubleshooting
If you see the following message:
There is an error in the single sign-on configuration, please contact your organization administrator.
Please:
- Confirm that the certificate you uploaded on the Proton VPN SAML configuration page matches the one provided by the Okta IdP.
- Confirm that the Single sign-on entity ID on the Proton VPN SAML configuration page is the same as the Issuer.













