Shared servers | Proton VPN for Business
As an administrator for a Proton VPN for Business or Proton Business Suite account, you can customize the list of countries that your organization’s users can connect to and appear to access the internet from. Unlike Gateways (which only your organization can access), anyone with a paid VPN plan can connect to these servers. We therefore call them shared servers. In this support article, we’ll look at:
- Why customize access to shared servers?
- How to create a new shared servers policy
- How to edit a shared servers policy
Why customize access to shared servers?
Organizations in regulated sectors (like finance or healthcare) might want to limit which countries some or all of their employees can browse from. There are a few reasons for this. Reasons for doing this include:
1. To control who can access your data
Many countries have laws that require internet service providers (ISPs) to give the government access to data passing through their networks. Even if your data is encrypted by the VPN, these governments can collect metadata (information about who is communicating, when, and how much), even if they can’t see the actual content. This metadata can expose sensitive details about your organization’s activities and relationships, potentially compromising privacy and security.
Example: An employee at an international law firm connects to a VPN server in a country with laws that force ISPs to share metadata with the government. Even though the data content is encrypted, the government collects metadata revealing who the firm communicates with, when, and how often. This exposes sensitive information about the firm’s clients and activities, such as involvement in confidential mergers or legal cases. Unauthorized access to this metadata can lead to breaches of client confidentiality, legal violations, and damage to the firm’s reputation.
2. For compliance with regulations and sanctions
Connecting through VPN servers in sanctioned or restricted countries can inadvertently violate international laws or sanctions, leading to potential legal liabilities and damage to your company’s reputation.
Example: An employee working for a European pharmaceutical company connects to a VPN server located in Iran, a country under EU and US sanctions. By using an Iranian IP address to access corporate systems, the company might be seen as engaging in business activities with Iran, thus violating the EU’s sanctions regime. This could result in substantial fines, legal action, and damage to the company’s reputation for non-compliance with international laws.
3. To enforce security policies
By restricting VPN connections to certain countries, your organization can enforce its internal security policies and prevent employees from bypassing important network controls. This helps prevent security risks and compliance issues that can arise if these controls are circumvented.
Example: An employee at a US healthcare clinic wants to access a personal social media site that’s blocked on the company’s network. To get around this, they use a VPN server located in another country, where internet restrictions are minimal. This action bypasses the clinic’s internet filters designed to block non-work-related websites.
While browsing, the employee unknowingly downloads a virus from the social media site. This virus infects their computer and spreads to the clinic’s network, compromising sensitive patient health records. Because patient data is now exposed, the clinic violates the Health Insurance Portability and Accountability Act(new window) (HIPAA), which requires the protection of patient information.
As a result, the clinic faces heavy fines and legal consequences for not safeguarding patient data and for allowing an employee to bypass security measures. If the clinic had restricted VPN connections to approved countries and servers, the employee wouldn’t have been able to bypass the network controls, and the data breach could have been prevented.
4. Prevent access from restricted locations
When employees use VPN servers in other countries, it makes it look like they’re accessing the internet from those places. This can cause problems because it might seem like the company is operating or accessing data from countries where it doesn’t have permission or could be restricted by law. This misrepresentation can lead to legal issues and security risks.
Example: An employee at a US-based technology firm connects to a VPN server in Iran to browse the internet anonymously. While connected, they access the company’s internal systems to check their work email. The company’s security system logs show a login from Iran, a country under strict US sanctions.
This unauthorized access from Iran could be interpreted as the company conducting business or transferring data to a sanctioned nation, thus violating US regulations enforced by the Office of Foreign Assets Control(new window) (OFAC). The company could face severe fines, legal action, and damage to its reputation for not preventing access from prohibited locations.
By restricting VPN connections to approved countries, the company ensures that all employee activities appear to originate from permissible locations, maintaining compliance with international laws and avoiding unintended legal consequences.
5. Simplify compliance management
Limiting VPN connections to certain countries reduces the number of international laws and regulations your organization needs to follow. This makes it easier to manage legal compliance because the company doesn’t have to keep track of laws in many different countries, thus lowering the risk of accidentally breaking foreign laws.
Example: A European marketing agency operates mainly within the EU. An employee there connects to a VPN server in South Africa to test how their website appears from that region. While connected, they handle EU customer data. The company is now subject to South African data protection laws, like the Protection of Personal Information Act (POPIA)(new window), in addition to the EU’s GDPR(new window).
The company hasn’t assessed compliance with POPIA and is unaware of its requirements. This oversight could result in legal violations and penalties under South African law. By restricting VPN connections to only EU countries, the company simplifies its legal obligations, ensuring it only needs to comply with GDPR, which it is already structured to meet.
6. Easier or enhanced internal security monitoring
Restricting VPN use to specific countries can help your organization’s security team monitor network activity more effectively. If users can connect from any country, it creates a lot of “noise” in the system, making it harder to spot suspicious activities. Restricting VPN connections allows your security team to quickly identify and respond to genuine threats.
Example: A company’s security team watches for unusual login attempts to protect against hackers. If an employee connects through a VPN server in a country where the company doesn’t normally operate, like Ukraine, the security system flags this as a potential threat. The team must investigate to determine if it’s a real attack or just an employee using a VPN.
Frequent connections from unexpected countries can overwhelm the security team, causing them to miss actual cyberattacks. By limiting VPN connections to approved countries, such as those where the company has offices, any access attempts from other regions can be immediately treated as suspicious, improving the team’s ability to safeguard the company’s network.
How to create a new shared servers policy
1. Sign in to account.protonvpn.com.
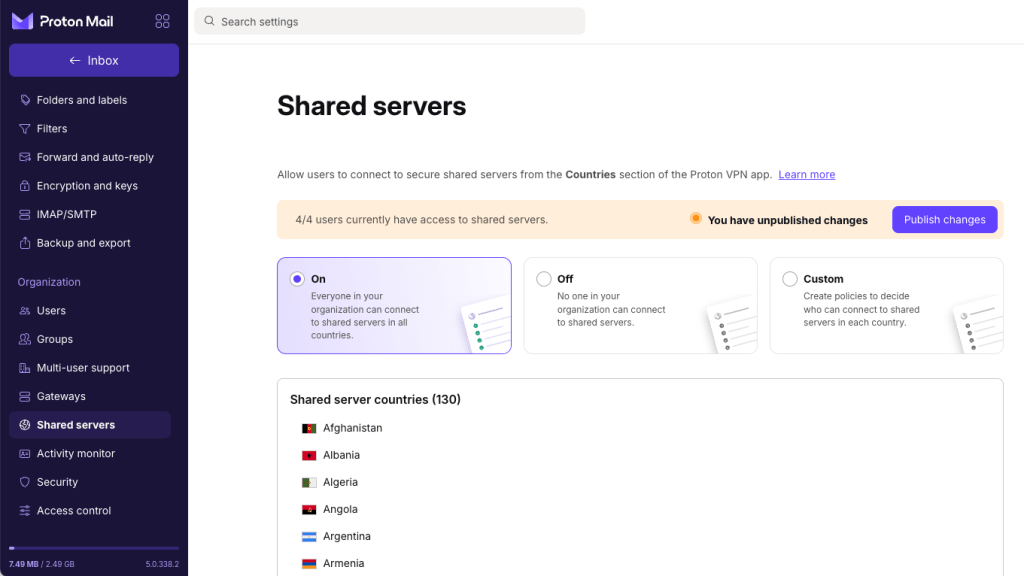
2. Select Shared servers from the sidebar.
3. Select how you’d like shared servers to work:
- On (default): Everyone in your organization can connect to shared servers in all countries
- Off: Nobody in your organization can connect to any shared servers.
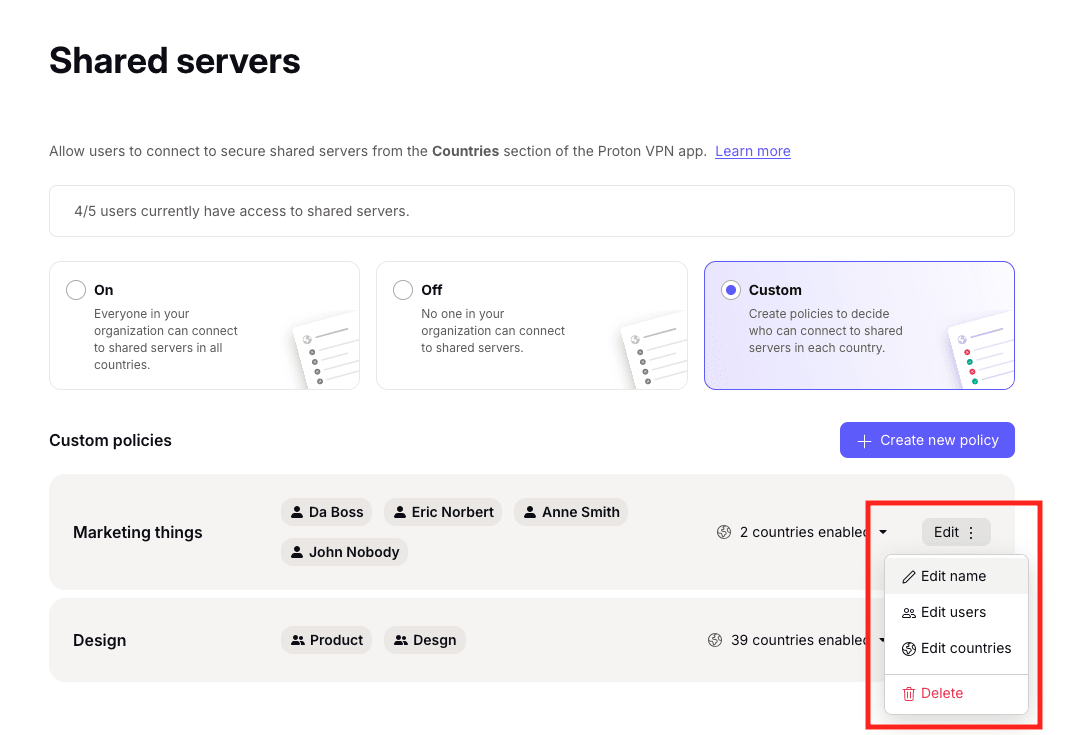
- Custom: Create policies to decide who can connect to shared servers in each country.
When you switch to On or Off, click Publish changes to confirm your choice. The rest of this support article assumes you’ve selected Custom.
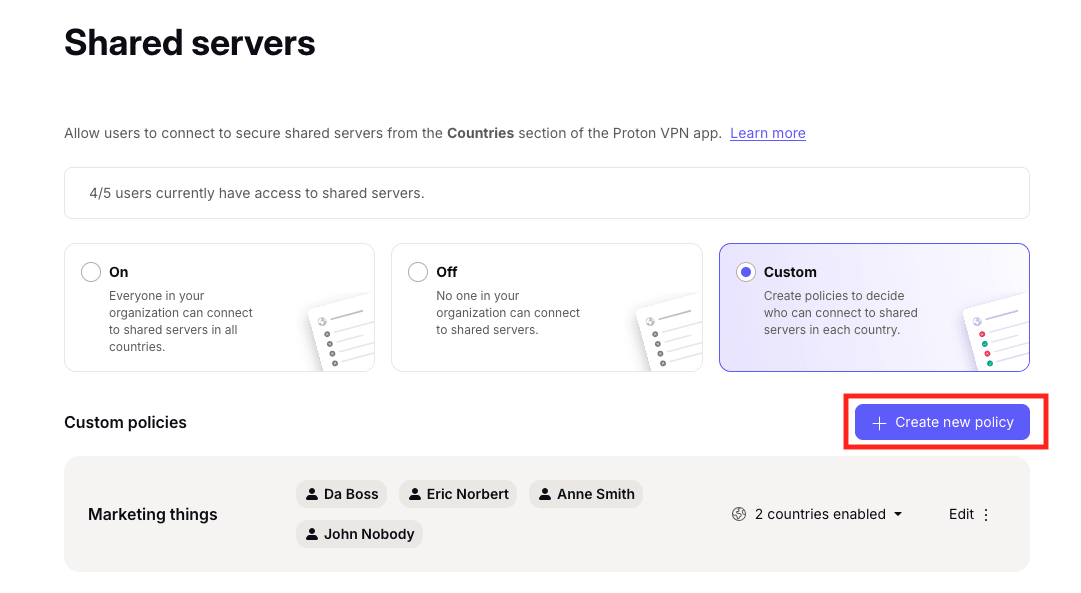
4. When you select Custom, you’ll see a list of custom policies that you (or another administrator) have already created for your organization. To create a new policy, select + Create new policy.
5. Give your policy a name and click Continue.

6. Shared server policies can be applied to individual users or groups.
- To add users: Select the Users tab. Select users from the list, or Search for their username or email address.
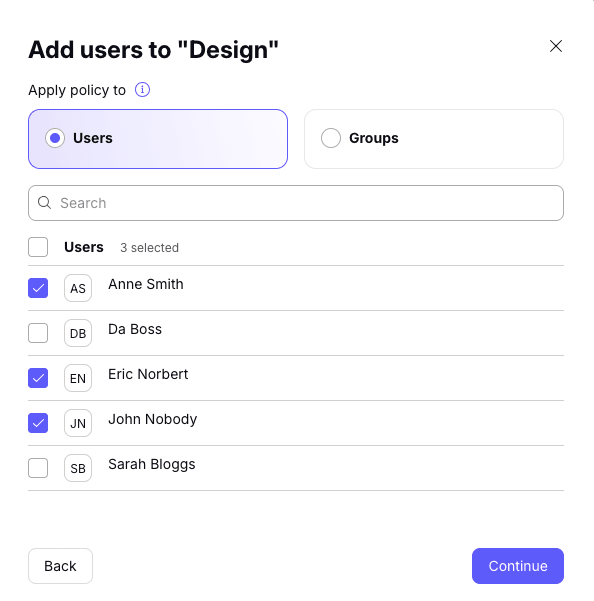
- To add groups: Select the Groups tab. Select groups from the list, or Search for the group’s name.
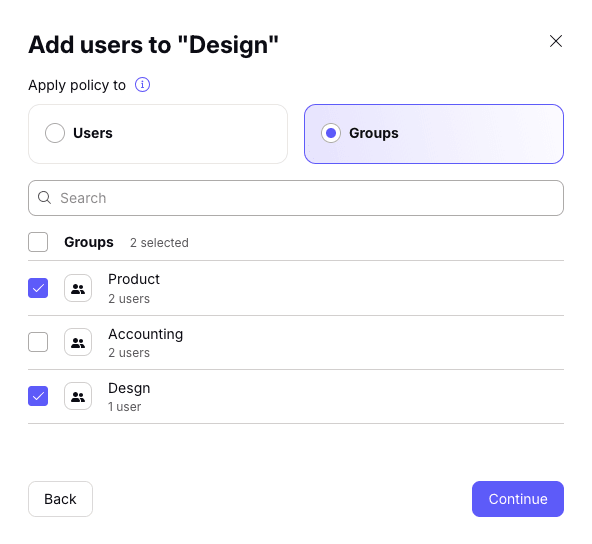
Once you’ve added everyone, click Continue.
7. Select the countries you want to allow users to connect to. You can also select cities or states in countries with multiple locations. Click Save when you’re done.

8. Your new shared server policy has been created. To make it active, select Publish changes. It may take up to a few hours for your changes to go live.
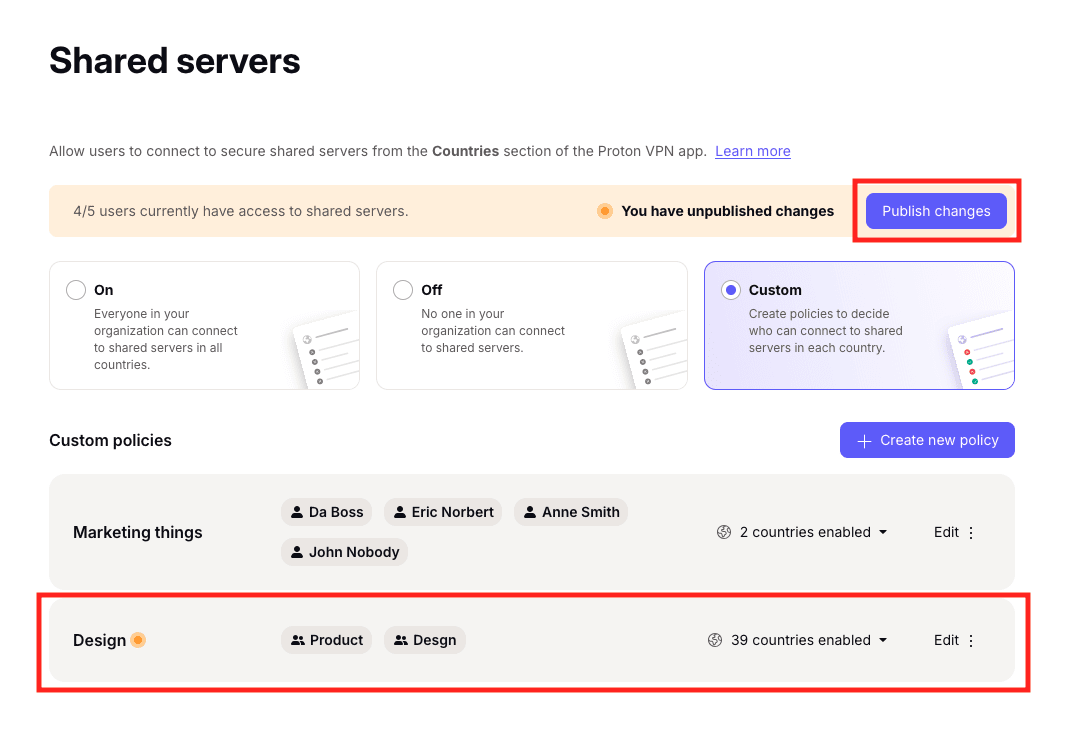
You’ll need to click Publish changes whenever you create, delete, or edit a shared server policy.
How to edit shared server policies
Go to Organization → Shared servers → Custom tab to see a list of your shared server policies. Select Edit to edit the policy name, users, or countries. You can also Delete the policy from here.