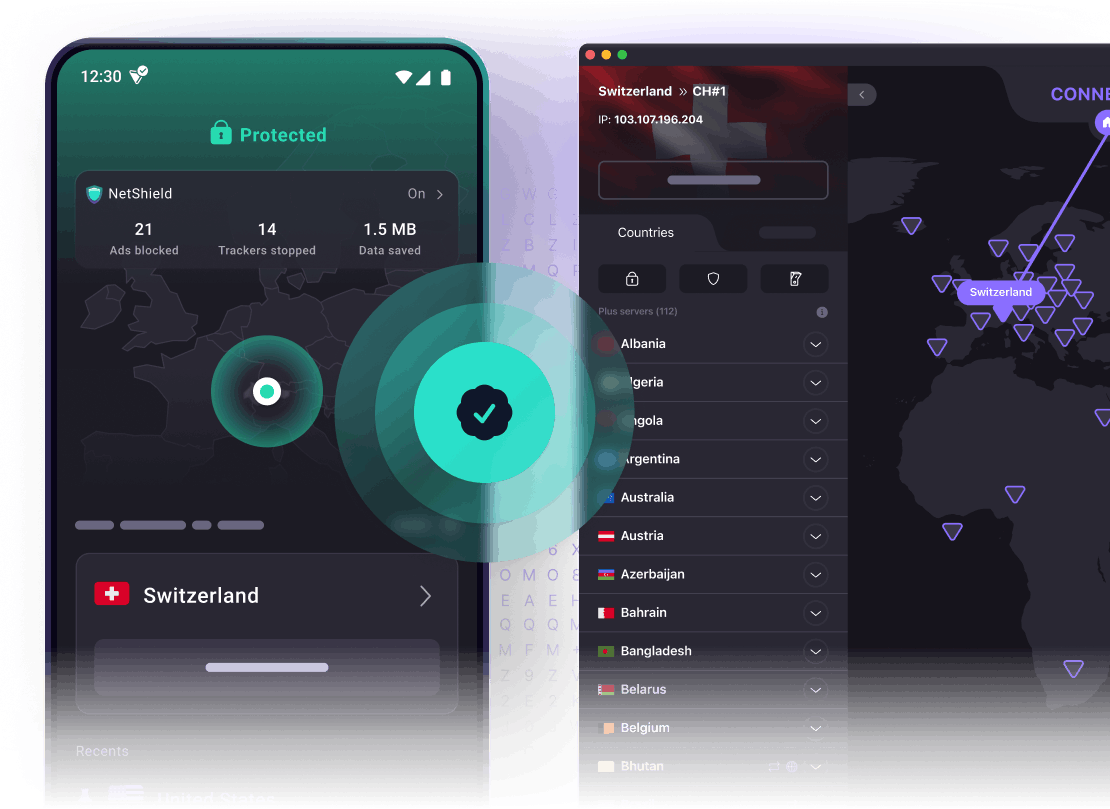
Proton VPN only uses strong, secure VPN protocols
The VPN protocol determines the security, stability, and speed of your VPN connection, which is why we only use protocols with strong security track records.
- Establish secure VPN tunnels using OpenVPN or WireGuard®
- Protect all past and future sessions with perfect forward secrecy
- Secure your DNS queries
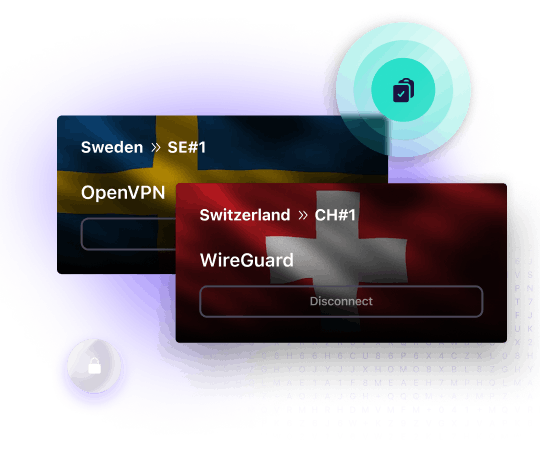
Our VPN protocols are secure, fast, and let you bypass internet blocks
Your security is our first priority, which is why Proton VPN protects your internet connection with strong VPN protocols that have a long track record of being secure and deploys these VPN protocols at their highest encryption settings.

OpenVPN
When properly configured, this tried and tested open-source VPN protocol is recognized by the cybersecurity community as being secure. Proton VPN implements OpenVPN at its strongest encryption settings and uses forward secrecy to ensure new keys are generated for each session.
A big advantage of OpenVPN is that it can be run using UDP or TCP transmission protocols. UDP is faster, but with TCP, we can configure OpenVPN to use the same port as the HTTPS protocol that secures all sensitive communications on the internet. This makes OpenVPN effective at defeating most censorship.
WireGuard
WireGuard is an open-source and lightweight VPN protocol that is faster than traditional VPN protocols. It also uses the advanced ChaCha20 encryption cipher to protect your VPN connection.
Stealth
Stealth is our custom VPN protocol that lets you bypass internet censorship and VPN blocks by disguising your VPN connection. With Stealth, you’ll be able to access censored sites and communicate with people on social media, even if your government is trying to restrict access. Stealth is available with all Proton VPN plans, including our Free plan.
Secure your internet with Proton VPN
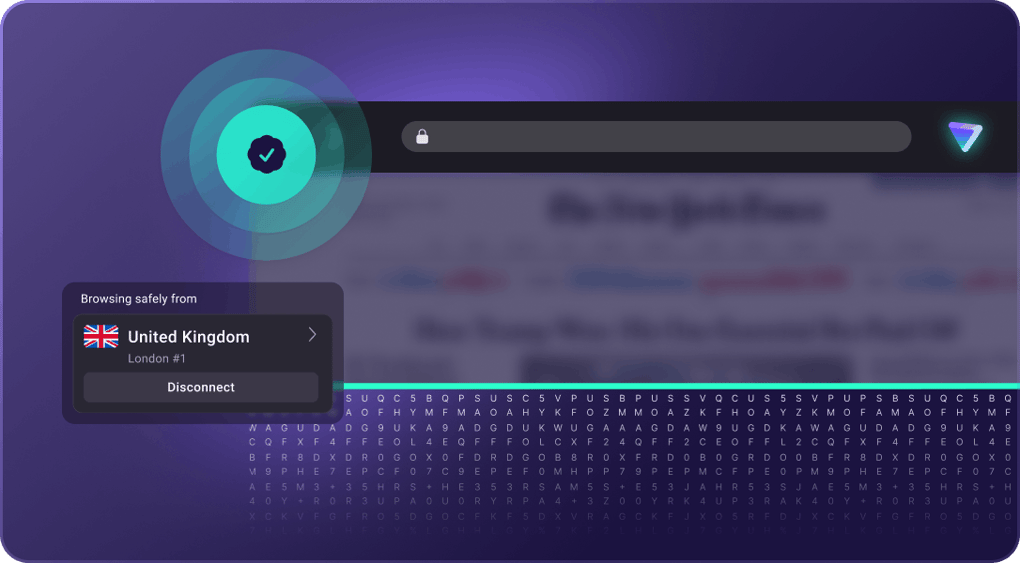
Encrypted data transfer
All data passing between your device and our VPN servers is encrypted using strong VPN and encryption ciphers protocols. Your internet provider, your government, and WiFi hackers cannot access your data.
Encrypted DNS resolution
When you connect to Proton VPN, we resolve your DNS queries by converting the URL into the IP address used by computers to identify a website. Your DNS queries are sent through the encrypted VPN tunnel so that no one, not even your internet provider, can monitor what you do on the internet.
Encrypted VPN servers
All Proton VPN servers use full-disk encryption to ensure that no one can intercept your data or steal our servers’ encryption keys, even in the unlikely event that attackers get physical access to our data centers.
Keep your personal information private with Proton VPN
Trusted
Proton is supported by the European Commission, recommended by the UN, and used by journalists, activists, and millions of people around the world to stay safe online.
Based in Switzerland
Proton VPN is based in Switzerland, which has some of the strongest data privacy laws in the world.
Kill switch
Our apps feature a kill switch to protect your IP address if the VPN connection is disrupted.
No-logs VPN
We do not keep any activity logs or metadata, meaning we have no data to share with anyone.
Open source
Proton VPN apps use open-source VPN protocols, like WireGuard and OpenVPN, so that anyone can check their code.
Audited by independent experts
Our open-source apps have been fully audited by independent security professionals, with the results openly published on our website.
VPN Accelerator
VPN Accelerator is a set of technologies unique to Proton VPN that can increase your VPN speed by over 400%.
Easy to use
Simply install our VPN app, tap our Quick Connect button, and it will automatically connect you to the fastest server.
Get a secure and fast VPN with Proton VPN
- Defeat censorship with alternative routing
- Protection from WiFi hackers
- Fast 10 Gbps server network
- Secure Core VPN
- Tor over VPN