An evil twin attack is a cyberattack that occurs when an attacker sets up a malicious WiFi network that mimics a legitimate one, often in public places like coffee shops, airports, or hotels.
This rogue WiFi network is the “evil twin” of a legitimate network, designed to deceive you into connecting to it instead of the real network.
Once you connect to this fake network, the attacker can intercept the unencrypted data you transmit over it, including sensitive information like your usernames and passwords, credit card numbers, and other personal data.
In this article, we’ll look at how evil twin attacks work and discuss why evil twin hotspots are, in reality, no longer a major threat.
- How an evil twin attack works
- Most connections are now encrypted
- You should still use a VPN on public WiFi
- Final thoughts
How an evil twin attack works
You can break down an evil twin attack into the following steps:
1. Setup
The attacker sets up a WiFi hotspot with a name (SSID) that closely resembles a legitimate one in the area. For example, it might have a name that resembles that of the coffee shop you’re sitting in or something like “Free Airport WiFi” at an airport.
Learn more about SSIDs and how they can be faked
2. Deception
You unsuspectingly connect to the malicious WiFi network, thinking it’s legitimate.
3. Data Interception
Once you connect, the attacker can eavesdrop on your unencrypted internet activity (including capturing passwords and payment details as you enter them), potentially inject malware, or redirect you to phishing sites.
Most connections are now encrypted
Until a few years ago, evil twin hotspots run by opportunistic hackers were a serious menace to anyone who used public WiFi networks.
This was because most online connections (such as the connection between your device and a website) were unencrypted. Data was sent in plaintext(new window), meaning that if you were tricked into connecting to an evil twin hotspot, the hacker running it could see everything you did on most websites you visited. The best defense against such attacks was to use a VPN (which we’ll discuss later).
The dangers of a largely unencrypted internet went far beyond just those posed by public WiFi hackers, as it allowed pretty much anyone to see everything you did on the internet. To combat this pervasive threat, the non-profit Let’s Encrypt(new window) campaign started issuing free HTTPS certificates to anyone who asked for them in 2015.
Now used by over 300 million websites, Let’s Encrypt quickly became the world’s largest certificate authority (CA) and kickstarted an encryption revolution on the web. As of January 2024, 85.1% of all websites use the HTTPS protocol(new window) (that figure rises to almost 100% for websites that deal with sensitive data, such as websites that process payments).
When a website uses HTTPS, its connection to your browser or mobile app is securely encrypted. This prevents hackers and anyone else (such as your WiFi host, ISP, or government) from accessing your data or knowing what you did on a website.
Learn how HTTPS keeps your connections safe (if not private)(new window)
As long as HTTPS is used, attackers can’t use evil twin hotspots to spy on your browsing, even if you’re connected to their network. All modern browsers clearly warn you when visiting a website not secured by HTTPS.
There is still some theoretical danger from evil twin attacks if you visit the 15% of websites that don’t use HTTPS, but as these are mainly “trash sites” that are obviously insecure, the danger is minimal. Perhaps even more importantly, the chances of a hacker gaining valuable information through an evil twin attack are so low these days that there’s little reason for them to bother trying.
The same is also true of WiFi sniffing attacks(new window) that attempt to intercept unencrypted data sent over public WiFi networks, which used to be the other big danger for anyone using a public hotspot. The result is that using public WiFi is much safer than it used to be, and the chances of your data being stolen by a criminal hacker are now minimal.
You should still use a VPN on public WiFi
HTTPS keeps your connections secure — but not private. It prevents criminals from seeing what you do on a website (including any passwords or payment details you enter), but it doesn’t prevent your Internet Service Provider (ISP) or public WiFi host (the person or business who operates the WiFi hotspot you’re connected to) from seeing which websites and services you connect to. And in this age of ubiquitous surveillance capitalism(new window), where everything we do online is monitored and used to target us with ever more personalized ads, this is valuable information.
There is a reason many public WiFi networks (many of which are operated by commercial third-party companies) require you to provide a valid email address and agree to an intimidatingly long and impenetrable Terns of Service (ToS) agreement(new window) before allowing you to use the “free” WiFi. They are selling your browsing history to advertisers.
Using a virtual private network (VPN) prevents this. It creates an encrypted tunnel between your device and a VPN server so no one else can see what you do online. This includes WiFi operators and your ISP.
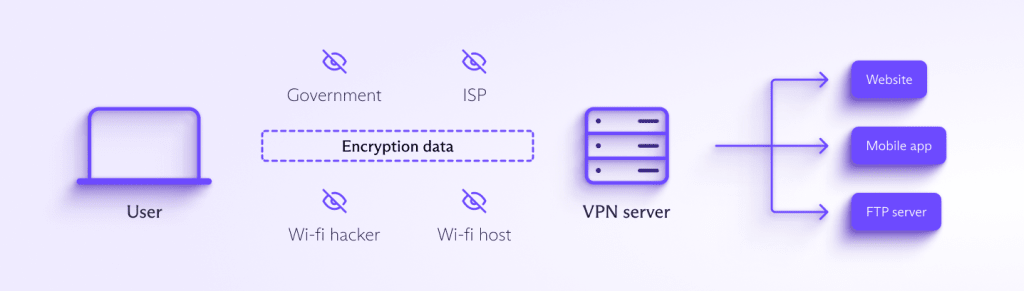
Learn more about how VPNs work
The VPN provider running the VPN server can see what you do online, but (unlike your ISP or public WiFi host) it’s in the business of protecting your privacy. A good VPN service (such as Proton VPN) keeps no logs of your online activity.
Final thoughts: how do you prevent an evil twin attack?
Thanks to the widespread adoption of HTTPS, you don’t really need to worry about evil twin attacks anymore. If they do still concern you, using a good VPN service will provide you with an extra layer of protection and ensure you can visit even non-HTTPS websites safely.
More importantly, a VPN will protect your privacy when using public WiFi networks, ensuring the WiFi host can’t log your browsing history and sell it to advertisers.


