A firewall is a security system designed to monitor and control incoming and outgoing network traffic based on predetermined security rules. It acts as a barrier between a trusted internal network and untrusted external networks, such as the internet, thus protecting against unauthorized access and other cyberthreats.
In this article, we’ll look at what firewalls are and how they work. We’ll also discuss how they interact with VPN services, and how they can be used together to improve your home or office cybersecurity.
In this article, we’ll look at:
- How does a firewall work?
- What does a firewall do?
- Why is a network firewall important?
- Types of firewalls
- How do VPNs and firewalls interact?
How does a firewall work?
Imagine your house is a local private network (LAN) – that is, all the devices in your house that connect to your modem/router, which connects to the internet. A firewall works like a security guard at the door of your house. It lets in trusted visitors (safe data), blocks strangers (dangerous data), and keeps an eye on everyone inside to make sure they behave appropriately.
The security guard has a guest list (a set of rules) that says who is allowed to enter the house. For example, friends and family are on the list, but strangers and suspicious people are not.
When someone approaches the door, the security guard asks for their ID (checks the data packet(новое окно) — a unit of data transferred over a network). The guard looks at important details like their name (IP address) and reason for visiting (protocol/port number). If the person (data packet) matches the guest list, the security guard lets them in. If the person is not on the list or looks suspicious, the guard turns them away.
Once inside, the security guard keeps an eye on your visitors to ensure they don’t go into off-limits rooms (sensitive parts of your network). If someone tries to access these rooms without permission, they get escorted out.
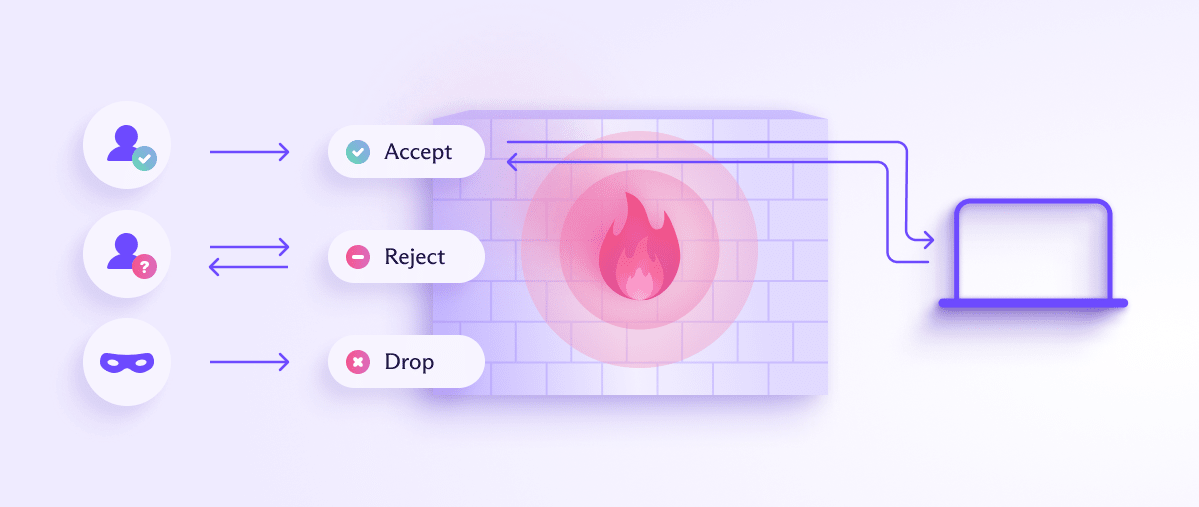
Firewalls often work in both directions. That is, they filter both incoming and outgoing traffic, preventing not only those on the internet from connecting to restricted local resources, but also preventing local users from connecting to specified resources on the internet. Some firewalls are outgoing-only.
An outgoing firewall might prevent a local device from connecting to an IP address associated with malware, or it could be used to censor content. A school might use a firewall to prevent students from accessing social media content, or a restrictive government might use firewalls to block content it deems objectionable on social, religious, cultural, or political grounds.
What does a firewall do?
A firewall performs three key functions:
1. Traffic filtering
Firewalls analyze data packets to determine if they should be allowed or blocked based on specific criteria, such as IP addresses, port numbers, protocols, and content.
2. Enforcing rule sets
Administrators configure firewalls with rule sets that define which traffic is permitted or denied. These rules are based on security policies that specify allowed and disallowed activities.
3. Monitoring and logging
Firewalls can continuously monitor network traffic and log significant events, providing network administrators with valuable insights into network activity and potential security risks.
Why is a network firewall important?
Using a firewall has several advantages:
- Enhances security by identifying and blocking potential threats before they enter the network.
- Safeguards sensitive information
- Assists in meeting regulatory and compliance requirements
- Helps to control and optimize network traffic
Firewalls can be deployed as a boundary between the internal network and the internet (which is known as a perimeter firewall), or within the network to protect specific segments and/or resources within that network (known as an internal firewall).
Cloud firewalls, also known as firewall-as-a-service(новое окно) (FWaaS), are hosted in the cloud and provide firewall protection for cloud-based infrastructure. Such firewalls are managed by cloud service providers.
Types of firewalls
Firewalls come in various types, each designed to meet different security needs and provide varying levels of protection.
What is a packet-filtering firewall?
Packet-filtering firewalls examine the headers of data (IP) packets, which include source and destination IP addresses, port numbers, and protocol information. They then apply rules based on these headers to either allow or block the packets.
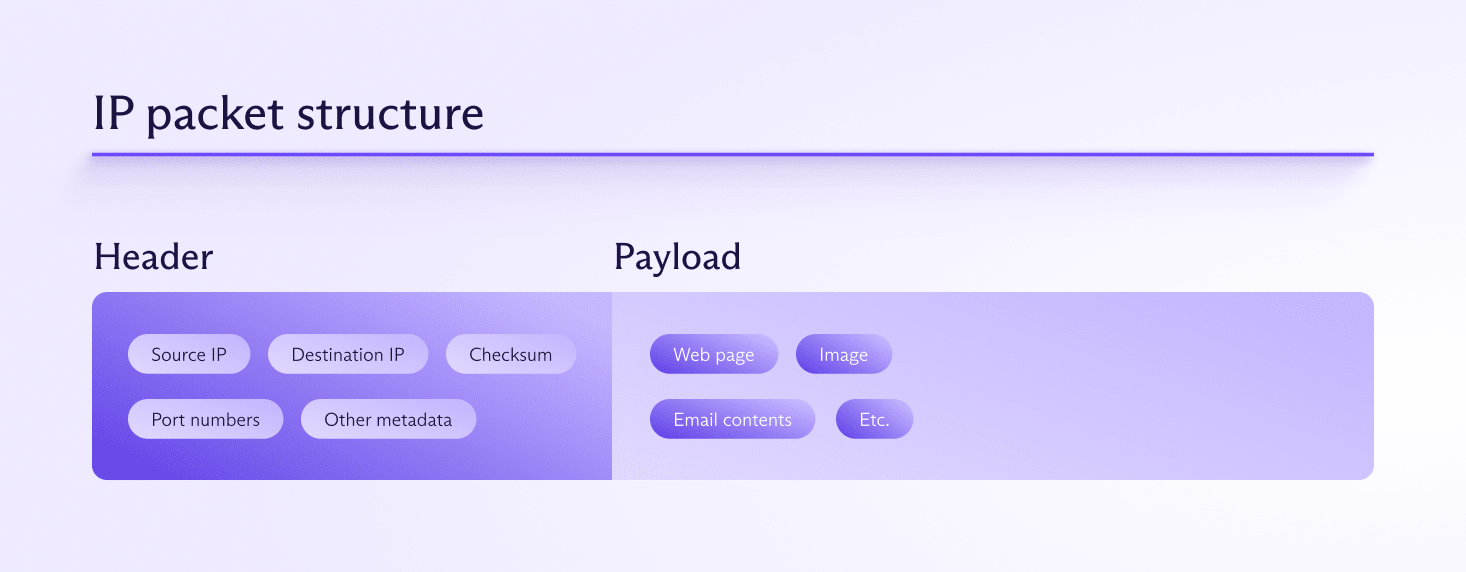
While stand-alone packet-filtering firewalls exist in theory, the reality is that all firewalls filter packets — it’s the most basic function of a firewall.
What is a stateful firewall?
Also known as dynamic packet filtering, these firewalls track the state of active connections and make decisions based on the state and context of traffic. They inspect packet headers and maintain a state table that records information about active connections.
Unlike stateless firewalls, which filter packets solely based on predefined rules and the information contained in the packet headers (such as IP addresses and port numbers), stateful firewalls track the state of active sessions and use this information to make more informed decisions about whether to allow or block traffic.
The state table includes information such as the source and destination IP addresses, port numbers, and the current state of the connection. By understanding the context of the connection, stateful firewalls can make more sophisticated decisions. For example, they can recognize whether a packet is part of an existing, legitimate connection or if it is an unsolicited packet that might be part of an attack.
Almost all real-world firewalls are stateful firewalls. They might offer additional functionality, as you will learn below,, but these are almost invariably a refinement of the stateful firewall.
What is a proxy firewall?
These firewalls act as intermediaries between you and the internet. They make requests on your behalf, inspect the entire data packet (header and payload), and, if deemed safe, send the data to the destination.
Proxy firewalls are best suited to environments where deep inspection of application data is crucial, such as corporate networks handling sensitive information.
Learn more about deep packet inspection
In principle, Proxy firewalls improve performance and reduce bandwidth usage. However, this is often countered by the fact that they can be complex and resource-heavy, thus becoming a bottleneck that slows down network performance.
What is a next-generation firewall (NGFW)?
NGFWs combine traditional firewall features with additional functionalities, such as deep packet inspection, intrusion prevention systems (IPS), and encrypted traffic inspection. They can identify and control applications, detect and prevent advanced threats, and enforce security policies.
Next-generation firewalls are highly effective at identifying and stopping advanced threats and provide comprehensive security by integrating multiple security functions. However, they’re more expensive and complex to manage, making them best suited to organizations that require advanced security capabilities to protect against sophisticated cyberthreats.
What is a unified threat management (UTM) firewall?
UTM firewalls integrate a mix of security services— various firewall types, antivirus software, and intrusion detection, for example —to provide a holistic approach to network security.
Although they lack the advanced features and flexibility of specialized security solutions like NGFW firewalls, UTM firewalls are often regarded as a cost-effective solution for small to medium-sized businesses, as they simplify security management by consolidating multiple security functions.
What is a network address translation (NAT) firewall?
NAT firewalls modify network address information in IP packet headers while in transit, so that multiple devices on a local network can share a single public IP address. They are often used by domestic routers and office LAN gateway servers, through which local devices connect to the internet.
NAT firewalls add a layer of security by hiding internal IP addresses, but are usually used in conjunction with other firewall types to provide more comprehensive security.
What is a web application firewall (WAF)?
A web application firewall (WAF) is a specialized firewall designed to protect web applications by filtering and monitoring HTTP/HTTPS traffic between a web application and the internet. WAFs help to safeguard web applications from various attacks, such as SQL injection, cross-site scripting (XSS), and other common web exploits, by inspecting and filtering incoming traffic.
What is a human firewall?
A “human firewall” is an analogy that refers to the collective effort of employees within an organization to act as a line of defense against cybersecurity threats. This concept emphasizes the role of human awareness and behavior in enhancing organizational security, complementing technological defenses like firewalls, antivirus software, and intrusion detection systems.
How do VPNs and firewalls interact?
A VPN creates an encrypted tunnel between your device and the VPN server.
This prevents any firewall between the VPN server and your device from interacting with your data, so data inside the VPN tunnel simply bypasses the firewall. This includes firewalls on domestic modem/routers and office corporate servers.
Learn more about how VPNs work
To address this issue, most VPN providers (including Proton VPN(новое окно)) implement firewalls on their servers to protect their customers. For example, Proton VPN servers use stateful firewalls to reject all incoming traffic connections that weren’t initiated by you.
If you want uninitiated incoming connections (for example, if you are torrenting), we offer a port forwarding feature, which punches a hole through the firewall. This introduces some (small) security risks, but port forwarding is only active if you choose to enable it.
Learn more about port forwarding
VPN apps also use firewall rules (and similar platform-specific operations) to prevent DNS and IPv6 leaks.
Learn how to check if your VPN is working
VPNs and firewalls used to censor content
Because an encrypted VPN connection prevents firewalls from examining and filtering VPN traffic, services such as Proton VPN are highly effective at bypassing firewalls that aim to block content on the web.
Learn more about how to bypass internet censorship with Proton VPN
Final thoughts: Firewalls and VPNs complement each other
Firewalls are an essential component of network security. Almost all firewalls are stateful firewalls, with variations that offer distinct features and benefits tailored to specific security needs and environments.
VPN services make extensive use of firewalls to keep both their own systems and those of customer devices safe, while at the same being an effective means of bypassing firewalls that aim to censor online content.







