A new security vulnerability in the OpenVPN protocol was recently revealed that would allow for sophisticated attacker to access a VPN user’s online activity.
At the most recent Black Hat and DEF CON(новое окно) security conferences, tech security researcher Ahamed Nafeez presented VORACLE, an attack that can eventually allow the attacker to decrypt data protected by the VPN. Shortly after the presentation, the Proton VPN team immediately began investigating our infrastructure for this vulnerability. Less than a day after Nafeez’s presentation, all Proton VPN servers which were susceptible to VORACLE have been updated and secured. More details about the attack and how we mitigated it can be found below.
A VORACLE attack
VORACLE is a remix of the older BREACH and CRIME cryptographic attacks. It decrypts HTTP traffic sent through VPNs built on OpenVPN protocols. It takes advantage of the fact that OpenVPN’s default setting is to compress all data before encrypting it with TLS. If an attacker repeatedly adds plain text information into the data prior to compression and then recovers the passing traffic, they can measure the packet length and then compare it to brute-forced potential value. This could eventually allow them to obtain the session cookie or session data.
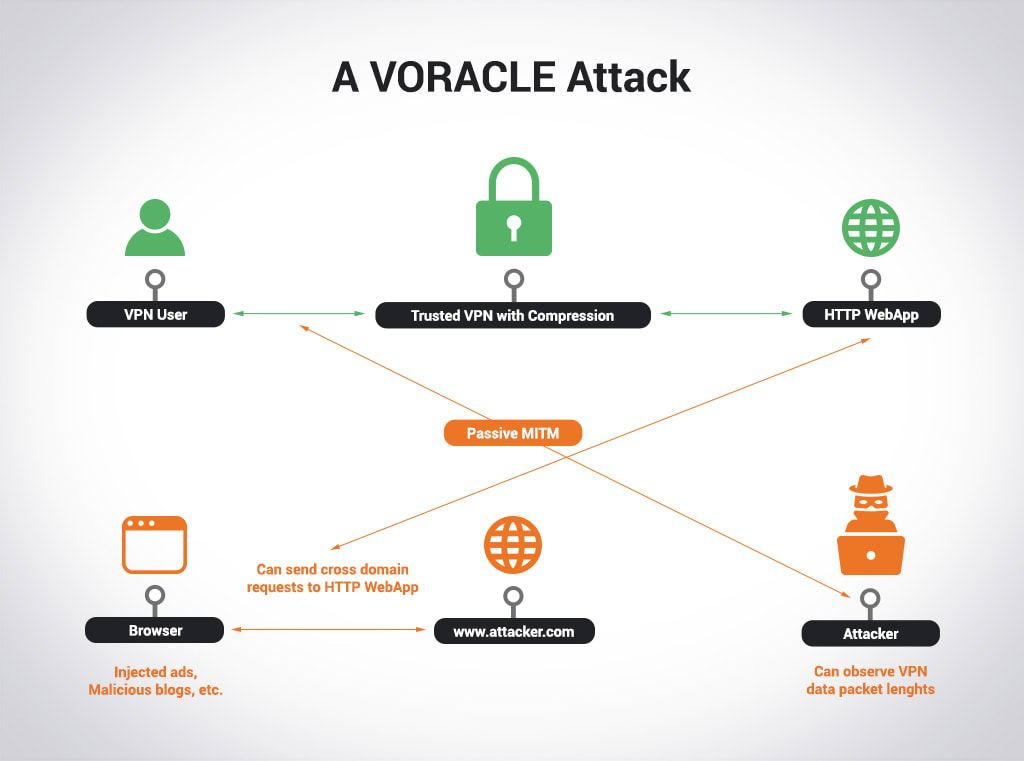
Since the VORACLE attack requires that the attacker be able to insert plain text information into the data before encryption and see the data after it has been encrypted, it often requires the attacker lure you to an HTTP site – either one under the attacker’s control or one where they can execute malicious code. Even then, using a Chromium-based browser (Chrome) can foil the attack since they split HTTP requests into multiple parts. Effectively, this makes the VORACLE attack hard to carry out in practice, although not impossible.
Proton VPN’s solution
As ingenious as the VORACLE attack is, it relies on OpenVPN’s default setting of compressing data before encryption. To protect against VORACLE, we have disabled compression on our OpenVPN servers. This eliminates the possibility of such an attack being used against Proton VPN users. Our initial assessment shows that disabling compression also does not lead to a noticeable performance degradation. For most users, the impact is less than one percent. In some cases, you may even experience faster performance due to decreased latency.
Best Regards,
The Proton VPN Team
You can follow us on social media to stay up to date on the latest Proton VPN releases:
Twitter (новое окно)| Facebook(новое окно) | Reddit(новое окно)
To get a free Proton Mail encrypted email account, visit: proton.me/mail(новое окно)







