A virtual private network (VPN) provides privacy and a host of other benefits when connecting to the internet. Our page What is a VPN?(새 창) explains what this technology does and some reasons you might find it useful to install your own VPN on your device.
In this article, we will go deeper and explain the more technical aspects of how a VPN works in a way that’s easy for anyone to understand.
We’ll start with some internet basics and then talk about how a VPN fits into the picture, followed by a question-and-answer section at the end.
How the internet works (without a VPN)
Your internet service provider (ISP) connects your device to the internet, so all data between your device and the servers (e.g., websites) you connect to on the internet flows through your ISP’s servers. Each device on the internet is assigned a unique number known as an IP address.
When you type a website’s URL into your browser’s address bar, your browser will send a request known as a DNS query to your ISP, asking for the correct computer-friendly IP address that you wish to connect to.
DNS is similar to a big telephone directory that maps URLs like “protonvpn.com” to their corresponding IP addresses. Once your browser has obtained the correct IP address from your ISP, it will initiate a connection with the website (or other internet resource).
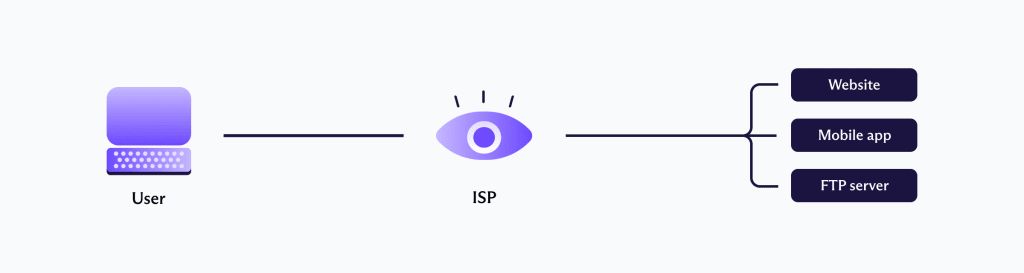
What your ISP can see
Your ISP (such as Verizon, Vodafone, or Comcast) knows the IP address of the router you are using and whose account it belongs to. It also knows which websites you have visited because just about every ISP in the world logs the DNS queries they process (together with a timestamp of when you make the query).
Even if your ISP doesn’t perform the DNS lookup (for example, if you manually typed in the IP address or used a third-party DNS service), it can still see the DNS request because these usually are not encrypted.
In recent years there has been a growth in third-party DNS services that do, in fact, encrypt DNS queries made to them. This is good, but your ISP can see which website you visit anyway, thanks to the fact that even if the DNS query is encrypted, the IP destination information required to correctly route your data isn’t.
HTTPS is an encryption protocol that secures the connection between a website and your device. Thanks in large part to the heroic efforts of the Let’s Encrypt(새 창) campaign, the use of HTTPS has increasingly become the norm, rather than the exception it was just a few short years ago.
Without HTTPS, your ISP can see everything you do on a website. This includes the individual pages you visit, any payment details you enter, and any form data that you submit. HTTPS prevents this. Even when HTTPS is used, though, your ISP can still see and log which websites you visit (just not what you do on them).
And what your ISP can see, so can your government.
What websites can see
Websites can see the last IP address in the chain of connections between your device and the webserver. Without a VPN, this is the unique IP address that your ISP has assigned to your router.
Websites routinely log this information, together with timestamps, frequency, and duration of visits, in order to understand how the website is being used and how it is performing. Should the police need to identify a particular user of that website, it’s a simple matter of asking the ISP to identify the customer it has assigned that IP address to.
Identifying an individual in this way is, of course, quite unusual. It may even sometimes require legal coercion, although most ISPs are happy to voluntarily cooperate with legitimate law enforcement requests.
Even without uniquely identifying you by your IP address, however, your IP address always tells websites which country you are in, and probably even in which city. This is thanks to the fact that ISPs usually assign IP addresses to home users in the same geographical vicinity in blocks, and databases of where these blocks of IPs have been assigned are publicly available.
In short, the internet was not built for privacy, so you should not expect any when using it as is.
With a VPN
When you use a VPN app on your device, it establishes an encrypted connection to a VPN server. This connection is made over the internet (so you still need your ISP), and is often referred to as a “VPN tunnel.”
This VPN server handles all DNS queries and acts as an intermediary that sits between your device and the internet, routing your data to the correct destinations.
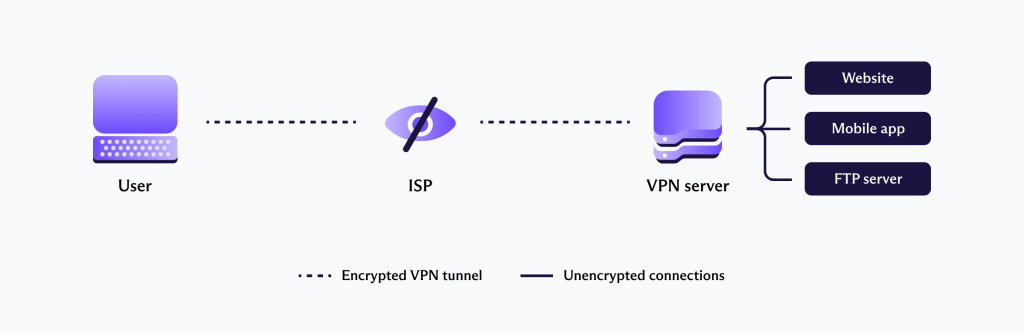
What your ISP can see
Your ISP can see that you are connected to an IP address belonging to a server. It won’t automatically know this is a VPN server, but it wouldn’t take Sherlock Holmes to figure it out, since it is the only IP address you appear to be connecting to.
What it can’t see are any websites or other internet resources that you connect to through the VPN server. This is because the VPN server handles DNS queries and routes your data to the correct IP address.
You ISP also can’t see the contents of your data (including IP destination data and DNS lookup requests) because all data traveling between your device and the VPN server is encrypted.
So when using a VPN, your ISP can’t see which websites you visit, and it can’t see the contents of your data (even when HTTPS is not used). The same is true of WiFi hackers, public WiFi router operators, or anyone else who might normally be able to see your data as it travels between your device and its destination.
What websites see
When using a VPN, the last IP address in the chain of connections between your device and the webserver is that of the VPN server. The VPN server, therefore, shields your real IP address from websites you visit, which will only be able to see the IP address of the VPN server.
In addition to its clear privacy benefits, this feature of a VPN is useful spoofing your geographic location, since you appear to access the internet from wherever the VPN server is located.
What the VPN server sees
In many ways, the VPN provider takes over the role of your ISP. It handles DNS queries and can monitor the IP addresses you visit.
Although the connection between your device and the VPN server is encrypted by the VPN, the connection between the VPN server and the websites you visit is not. This means that (like your ISP normally can), the VPN server can view the content of traffic that is not protected by HTTPS.
It is, therefore, of critical importance to choose a VPN service that is trustworthy and secure.
How Proton VPN ensures privacy and transparency
At Proton, our commitment to users’ privacy is well known. Proton VPN and Proton Mail(새 창), the largest encrypted provider in the world, are trusted by journalists and activists in the field, and we have taken a number of steps to strengthen your security and privacy:
- Unlike most ISPs, we keep no logs that can compromise your privacy. A timestamp is kept of your last successful login attempt, but this is not connected to the IP address you connect from or to any activity while using our service.
- Our apps are all fully audited and open source, so anyone can check them.
- We are based in Switzerland, a country with no ties to the USA-led Five Eyes mass surveillance alliance, and which has among the strongest data privacy laws(새 창) in the world.
- We use only the most secure VPN protocols(새 창), with strong encryption and forward secrecy.
- We offer a specially hardened Secure Core VPN service for those who need it.
- Our apps offer DNS leak protection to ensure DNS lookups are handled exclusively by Proton. IPv6 leak protection ensures no data is ever routed outside the VPN tunnel.
FAQ
Encryption is a mathematical process that converts data into illegible characters so that no one without the correct key can access it. It is the cornerstone of keeping your data safe on the internet. Proton VPN uses only the strongest encryption suites; please see our post on strong encryption(새 창) for more information.
AES is a symmetric key encryption cipher used to secure large chunks of data at rest. AES-256 is AES implemented with a 256-bit key size, which is its strongest setting.
AES is approved by NIST, and the US government secures its top secret data with AES-256. This has led many VPN services that use AES-256 to describe their encryption in terms such as “military grade.” AES-256 is, indeed, very secure, but it is only one of the components required to ensure a VPN connection is secure.
A VPN encrypts your data as it travels between your device and the VPN server, thus preventing anyone who would otherwise be able to access the data (such as your ISP or public router operator) from seeing its contents.
Individual “packets” of data are encrypted on your device and then decrypted on the VPN server. The tunnel analogy is a useful way to think about this encrypted connection.
A VPN protocol is the set of instructions used to establish a secure connection between two computers (your device and the VPN server). Various VPN protocols exist, but Proton VPN supports OpenVPN, IKEv2, and WireGuard.
OpenVPN – A battle-tested VPN protocol that is still widely regarded as the last word when it comes to VPN security.
IKEv2 – A more modern VPN protocol that is fast while also considered by experts to be very secure.
L2TP/IPsec – Although believed compromised by the NSA, under most circumstances, this protocol is still considered secure. It has, however, been superseded by the superior IKEv2.
PPTP – A highly insecure protocol that some providers continue to support for compatibility reasons.
WireGuard® – A very new VPN protocol that, while fast and secure (at least in theory), is still experimental. Proton VPN is watching the development of WireGuard (now out of beta phase on Linux) with great interest and has helped to fund its development.
Learn more about VPN protocols.
Yes, but not too much. Encrypting and decrypting your data requires processing power, which, in theory, can slow down your internet connection. In practice, even low-end modern smartphones can handle VPN encryption with no noticeable slowdown.
A bigger issue is how far your data travels. Connecting to a VPN server adds another “leg” to its journey, which inevitably slows it down. This is particularly true if the VPN server you connect to is located on the other side of the world from you.
If you connect to a VPN server fairly nearby, however, (for example, anywhere in Europe if you are based in Europe), then it is unlikely you will notice any slowdown. In addition to this, our unique VPN Accelerator technology can increase speeds by over 400% under certain conditions and is particularly effective at mitigating speed loss when connecting to geographically distant servers.
Learn more about VPN Accelerator
Another factor to consider is the “server load” of the VPN server you are using. That is, how many people are using it at the same time as you and thus making demands on its resources.
This is the only reason that our free servers, which can get a little busy during peak times, do not always allow the speeds that are available when using our Plus servers, which tend to be less busy.
Every device connected to the internet is assigned a unique number to identify it. The huge expansion of the internet in recent years, however, means that numbers assigned using the old IPv4 system are running out. Fast.
IPv6 fixes this problem by using 128-bit web addresses, making some 2^128 (around(새 창) 340 billion billion billion billion) new numbers available, which should keep us going for quite some time.
All modern operating systems support IPv6, but most of the internet still uses IPv4. As a hybrid compromise solution to this problem, your device will send connection requests to websites you visit using both their IPv4 and IPv6 addresses.
If the website supports IPv6 then it will accept the IPv6 connection. If it only supports IPv4 then it won’t even be aware of the IPv6 connection attempt and will initiate an IPv4 connection.
Many VPN apps from other VPN services are also IPv4 only, and thus only route IPv4 connections through the VPN tunnel. When an IPv6 connection is established, the VPN app is not aware of it, and the connection is thus routed by your OS outside the VPN tunnel.
The website you have connected to can therefore see your real IPv6 address, even though you are using a VPN. This is an IPv6 leak.
Proton VPN applications block all IPv6 traffic by default to ensure this does not happen. This has no effect on our internet experience.
When using a VPN, DNS queries are supposed to go through the VPN tunnel so that only the VPN service can see and resolve them. A DNS leak occurs when a DNS request is somehow routed outside the VPN tunnel so that it can be seen by (and usually also resolved by) your ISP.
There are a number of reasons this can happen, and while Windows tends to be the worst offender, it can happen on any platform. DNS leak protection solves the problem by using firewall rules to ensure no traffic can leave your device outside the VPN tunnel.
You can follow us on social media to stay up to date on the latest Proton VPN releases:
Twitter (새 창)| Facebook(새 창) | Reddit(새 창) | Instagram(새 창)
To get a free Proton Mail encrypted email account, visit proton.me/mail(새 창)







