In recent years, journalists(새 창) have emerged as one of the top targets of surveillance by governments around the world. If you’re a reporter(새 창) working on sensitive topics, no country is safe for privacy in the context of an international market for spyware(새 창) apps that can secretly monitor all the data transmitted and stored on your iPhone.
As these apps proliferate, it has become critical to understand how to find hidden apps on iPhone and remove them.
- The spyware targeting journalists
- How hackers hide apps on iPhone
- How to check your iPhone for Pegasus spyware
- How to check your iPhone for Graphite spyware
- How to find hidden apps on an iPhone
- What to do with spyware on your device
The spyware targeting journalists
In June 2025, researchers at Citizen Lab(새 창) reported new evidence(새 창) that the Italian government is targeting journalists and activists with Graphite spyware developed by the Israeli firm Paragon Solutions(새 창).
Citizen Lab has previously found evidence of Graphite use(새 창) in Australia, Canada, Denmark, Singapore, Israel, and Cyprus, with potential links to police in Canada. Graphite is responsible for a hacking attack in January 2025 that targeted almost 100 journalists and other members of civil society using WhatsApp(새 창) on their iPhones. Notably, given current events in the United States, the US Immigration and Customs Enforcement (ICE) signed a $2 million contract(새 창) with Paragon in 2024.
Graphite works in a very similar way to the infamous Pegasus spyware(새 창) from NSO Group(새 창). Paragon Solutions’ competitor in the world of mercenary spyware, this company is known for its close relationship with the Israeli state, and its spyware is classified as a military export(새 창) by Israel. NSO Group sells its software to governments around the world(새 창), including Saudi Arabia, Dubai, India, Mexico, Morocco, Rwanda, and Hungary, and its Pegasus software is linked to the brutal assassination(새 창) of Saudi human rights activist Jamal Khashoggi(새 창).
How hackers hide apps on iPhone
Both Graphite and Pegasus are suites of exploits that target iPhones. Graphite is newer and much less documented than Pegasus, and it’s telling that the Israeli government sought to replace Pegasus with Graphite(새 창) in the Saudi armory.
Apple released a patch(새 창) to mitigate against Pegasus back in 2023, and following the WhatsApp attack it released a patch for iOS 18.3.1 to address the vulnerability exploited by Graphite. But there are no guarantees these patches will be effective against updated versions of the spywares.
Both apps exploit zero-day vulnerabilities in iOS using a variety of attack vectors. The most worrying of these are zero-click attacks(새 창) that exploit vulnerabilities in apps like iMessage, WhatsApp, or FaceTime to silently infect a device without any need for the victim to click links or otherwise interact with their phone.
Once an iPhone has been infected, the spyware uses a modular architecture to enable or disable components remotely based on the client’s surveillance goals. Capabilities include:
- Keylogging
- Microphone and camera access (for live audio and video eavesdropping)
- Call log, SMS, contact, and email access
- Encrypted messaging app data (Signal, WhatsApp, Telegram) access using accessibility services or by capturing data before encryption
- GPS tracking
- Screenshot capture
The spyware is very hard to detect on an iPhone, and can self-destruct to erase evidence if it doesn’t phone home for a set period of time, or on command. NSO Group has created a version of Pegasus that also targets Android devices(새 창). This has similar functionality to the iOS version, but uses a different mode of attack.
It is very difficult to estimate how many devices are affected by either spywares, but back in 2021 NSO Group leaked 50,000 phone numbers(새 창) of potential Pegasus targets.
How to check your iPhone for Pegasus spyware
Apple does not permit true anti-malware apps on the App Store (strictly speaking, “anti-malware” apps are available on the App Store, but limits on their access to system resources severely restrict their usefulness). And in any case, traditional anti-malware software is ineffective against Pegasus on other platforms.
Mobile device security firm iVerify offers a Threat Hunting(새 창) tool that it clams has already discovered seven Pegasus infections(새 창) (as of December 2024). Available for less than a dollar on the App Store (somehow skirting Apple’s malware scanning restrictions), iVerify Basic(새 창) is very easy to use. But as closed-source proprietary software, there’s no way to independently asses how effective it is.
Another option is to use Mobile Verification Toolkit (MVT(새 창)), a free, open-source tool from the human rights group Amnesty International’s Security Lab(새 창). This extracts various types of data from an iPhone backup to find evidence of a Pegasus attack, including
- SMS messages
- Call logs
- Data from installed apps
- System logs
It then analyzes this data to detect “Indicators of Compromise” (IOCs), such as specific processes and file names that are known to be associated with Pegasus. It should be noted, though, that to use the tool you’ll need a Linux PC or Mac and familiarity with the command line. Some deeper understanding of malware forensics is also required to get the most from the results.
A more user-friendly option (with a GUI) is the iMazing(새 창) tool, which uses methodology that “closely mirrors” that of open source MVT. It’s paid software, but a free trial includes the Pegasus detection tool. You’ll still need access to a Linux PC or Mac, though.
How to check your iPhone for Graphite spyware
There are no tools available yet that can specifically detect a Graphite infection.
The tools for detecting Pegasus discussed above might have some chance of detecting the newer spyware, but they cannot be relied on for this. The general tips discussed below may also be useful for detecting suspicious behavior.
How to find hidden apps on an iPhone
In general (outside of the kind of state-sponsored spyware discussed above), iPhones don’t allow third-party apps to truly “hide” in the background like they can on Android. However, some can be deliberately hard to find.
Despite Apple’s fairly robust sandboxing, code-signing, and App Store review process, iPhones are not immune to viruses or malware(새 창). People with direct access to your phone (such as domestic abusers) may also install less sophisticated forms of spyware when your back is turned.
This means everyone can benefit from periodically checking that nothing is running on your iPhone that shouldn’t be. Here are some tips for finding hidden apps:
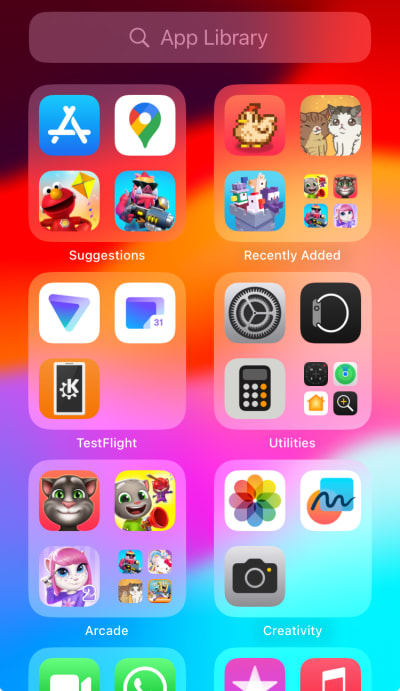
1. Check your App Library: Swipe all the way to the rightmost home screen. Here you’ll see all apps installed on your iPhone, even if you don’t see them on your regular home screens. Look for any apps that are unfamiliar to you, especially those with foreign names. Research online whether these represent legitimate software or are common malware disguises. If you have any doubt, uninstall the apps.
2. Check for malicious configuration profiles: These are designed for businesses and schools to remote-manage your iPhone, but can be an important vector for malware attacks(새 창). Open the Settings app and go to General → VPN & Device Management. Delete any profiles(새 창) you don’t recognize.
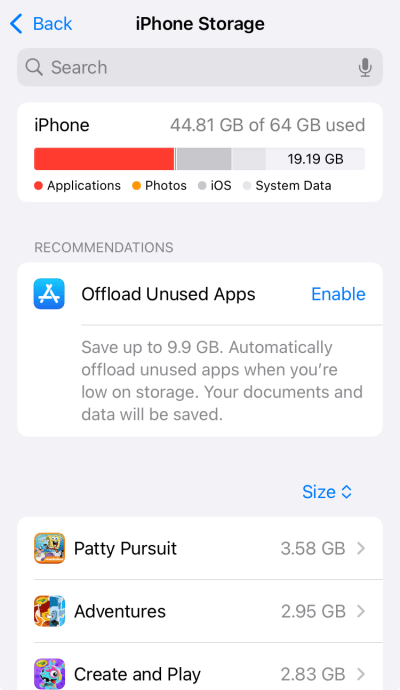
3. Check your storage: Open the Settings app and go to General → iPhone Storage. Review the list of installed applications displayed here. Any discrepancies between visible apps on your home versus those shown here warrant further investigation.
4. Be aware of suspicious behavior: Unusual battery drain or data usage, or a hot phone when not in use, may indicate malware. If you have the technical skills, you can use package capture tools such as Wireshark(새 창) to analyze where your iPhone’s data is going.
What to do about spyware on your device
One piece of encouraging news from Citizen Lab’s research is that spyware such Graphite and Pegasus is highly targeted — mainly at journalists, but activists, dissidents, political figures, and those work in sensitive sectors may also be targets.
If you’re concerned that you might be a target for this kind of surveillance, you should activate Lockdown Mode. This is a special feature designed by Apple to harden iPhones against just the kind of targeted cyberattacks used by Pegasus and Graphite. To turn Lockdown Mode on, open the Settings app and go to Privacy & Security → Security → Lockdown Mode.
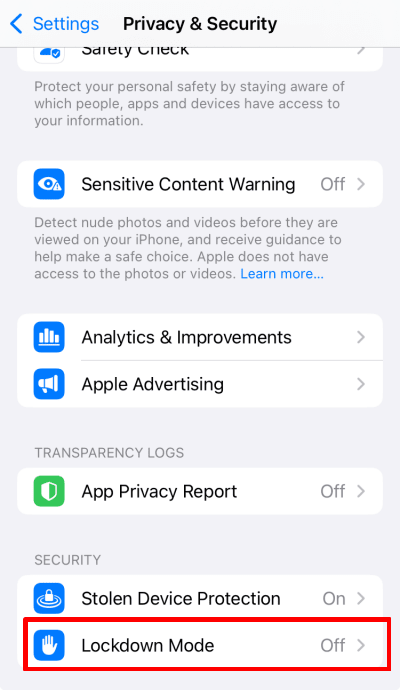
It’s worth noting that using Lockdown Mode comes some downsides, such limited functionality, reduced convenience, potential compatibility issues, and fewer customization options. It’s therefore not a great option for most people. But if you’re a journalist, or otherwise think you may be a target for spyware, its security benefits are likely to outweigh any relatively minor inconveniences.
Other things you can do include:
- Update iOS: The best defense against malware is to keep iOS up-to-date, as Apple routinely patches its mobile operating system to address new vulnerabilities as it becomes aware of them.
- Don’t jailbreak(새 창) your phone: This removes many of the security features that are normally built in to iOS, and potentially allows third parties to bypass the App Store and sideload(새 창) apps onto your phone without your knowledge.
- Factory reset your phone: If you’re suspicious about an app on your phone, you should factory reset your phone(새 창). This will get rid of almost all “consumer-level” malware. But it may not be sufficient to dislodge state-sponsored spyware such as Graphite and Pegasus. If you suspect this level of surveillance, its probably best to either call in a professional malware expert or simply replace your iPhone.
- Use NetShield Ad-blocker: Proton VPN’s DNS filtering solution can block DNS calls to known malware and phishing domains. The means even if your iPhone becomes infected with malware, it may not be able to “phone home”.
If you are at all concerned about being targeted with state-sponsored malware, Lockdown Mode is specially designed to counter such threats. For everyone else, Apple largely does a good job at keeping iPhones secure, but be sure to keep yours up-to-date with the latest iOS version and to stay vigilant.


