AES is a fast, efficient, and secure encryption standard. Certified by the National Institute of Standards and Technology(nouvelle fenêtre) (NIST), AES is used by the United States government to secure classified data. This has led many companies to market AES (especially AES with a 256-bit key) as “military-grade encryption”, although such terminology is as inaccurate as it is meaningless.
What does AES stand for?
AES stands for Advanced Encryption Standard, and is a symmetric-key cipher. There are two fundamental kinds of cipher algorithms:
Asymmetric-key ciphers
These use public-key cryptography to allow the secure exchange of keys over a distance (such as over the internet). Data is encrypted using a public key, which is made widely available, but which can only be decrypted using the correct private key (which only the intended recipient should possess).
Asymmetric-key ciphers require a high level of computational power. This makes them relatively slow, and thus most useful for encrypting small amounts of data. RSA(nouvelle fenêtre), for example, is an asymmetric cipher used to encrypt just the keys during the TLS(nouvelle fenêtre) exchange that occurs when connecting to an HTTPS(nouvelle fenêtre) website.
Symmetric-key ciphers
The same key is used to both encrypt and decrypt the data. There may sometimes be a simple transformation between the two keys, but they are always derived from the same key.
Symmetric-key ciphers require much less processing power than asymmetric-key ciphers, and are therefore often cited as being around 1,000 times faster. This makes symmetric-key ciphers ideal for encrypting large volumes of data.
Where large amounts of data need to be transmitted over a distance (such as over the internet), the data itself is encrypted using a symmetric-key cipher, such as AES, while the key exchange is secured using an asymmetric-key cipher, such as RSA.
This is, in essence, what the OpenVPN protocol does to secure VPN connections.
Is AES secure?
In 2000, after a very thorough(nouvelle fenêtre) and open selection process, NIST announced that AES (formally known as Rijndael, after its creators Vincent Rijmen(nouvelle fenêtre) and Joan Daemen(nouvelle fenêtre)) would replace DES(nouvelle fenêtre) as its recommended(nouvelle fenêtre) “unclassified, publicly disclosed encryption algorithm capable of protecting sensitive government information well into the next century.”
Based on NIST’s recommendation, the US government uses AES to secure its classified information:
“The design and strength of all key lengths of the AES algorithm (i.e., 128, 192 and 256) are sufficient to protect classified information up to the SECRET level. TOP SECRET information will require use of either the 192 or 256 key lengths.”
Brute force attacks
The most basic form of attack possible on any encryption cipher is a brute force attack, which involves trying every possible key combination until the correct one is found.
As we discuss in Privacy Decrypted #3: Can encryption be broken?(nouvelle fenêtre), Fugaku(nouvelle fenêtre) is currently the most powerful (known) supercomputer in the world. If it dedicated its entire output to the task, it would take Fugaku 12 trillion years to exhaust all possible combinations for AES-128.
AES-256 is 340 billion-billion-billion-billion times harder to brute force than AES-128. To put this into perspective, the universe is 14 billion years old. It is therefore safe to say that even at its lower bit sizes, AES is highly resistant to brute force attacks from conventional computers.
It is often theorized that when quantum computing(nouvelle fenêtre) becomes available, modern encryption algorithms will be rendered all but useless. There is truth in this when it comes to asymmetric-key ciphers, but symmetric-key ciphers are relatively quantum resistant(nouvelle fenêtre), although quantum computers still reduce the security of AES by half. This means AES-256 remains secure(nouvelle fenêtre), but AES-128 less so.
Brute force attacks, however, are not the only way to compromise an encryption algorithm.
Key attacks
Over the years, a number of theoretical attacks on AES keys have been published by cryptographers, but all of these are either unworkable in practice, or are only effective on AES implementations that use a reduced number of rounds (see below).
The most successful attempt was a biclique attack(nouvelle fenêtre) published in 2011 that can reduce the time needed to brute force AES by a factor of four. However, it would still require billions of years to brute force AES on any current or foreseeable computer hardware.
No known key attack is practical against properly implemented AES-128 or higher.
Side channel attacks
A side-channel attack(nouvelle fenêtre) attempts to reduce the number of combinations required to make a successful brute force attack by looking for clues from the computer performing the encryption calculations. Clues can be gleaned by examining:
- Timing – how long a computer takes to perform an operation
- Electromagnetic leaks
- Audio cues
- Visual cues (picked up using a high-resolution camera).
Cache-timing attacks, in particular, have proven to be quite effective at successfully cracking AES. In the most notable example, researchers in 2016 were able to recover(nouvelle fenêtre) an AES-128 key using “only about 6 – 7 blocks of plaintext or ciphertext(nouvelle fenêtre) (theoretically even a single block would suffice)”.
However, there are a number of things that can be done to mitigate against the threat of side channel attacks:
- Properly implemented AES can prevent ways that data can be leaked.
- Hardware that integrates the AES instruction set(nouvelle fenêtre) further reduces the side channel attack surface of AES.
- Randomization techniques can be used to disrupt the relationship between data protected by AES and any leaked data that could be collected using a side-channel attack.
It is also worth noting that, in many cases, side channel attacks require the attacker to have close proximity or physical access to the device as it decrypts data (although remote attacks are possible if malicious software is installed on a device, particularly in the case of timing attacks).
The human factor
Security is only as strong as its weakest point. There is little point encrypting your data with AES-256 if you then secure it using the password “12345”. Social engineering attacks and keylogger viruses are also a threat to AES-encrypted data.
Use of a good password manager(nouvelle fenêtre), anti-virus software, and improved education about cybersecurity are the best forms of defense against these kinds of attacks. Note that this kind of attack is only a risk if you encrypt your own data with a password. It is not an issue with OpenVPN, where data is encrypted using RSA.
How AES works
AES is a block cipher(nouvelle fenêtre) that encrypts and decrypts data in blocks of 128 bits using 128-bit, 192-bit, or 256-bit keys. As noted earlier, the same key is used for encrypting and decrypting data. AES using a 128-bit key is often referred to as AES-128, etc.

Data is encrypted using multiple rounds, each of which consists of a series of mathematical operations.
The process starts with using Rijndael’s key schedule algorithm to derive a series of new round keys from the original secret key. This is known as key expansion.
Each round then consists of one or more (or a combination) of the following operations:
1. AddRoundKey — an XOR operation(nouvelle fenêtre) is performed to combine the data to be encrypted (the cipher text) with each round key.

2. SubBytes — a substitution table is used to further mix up the data (think, in principle, of the simple substitution ciphers you used as a child where you substituted each letter in a message for one a set number of later in the alphabet).
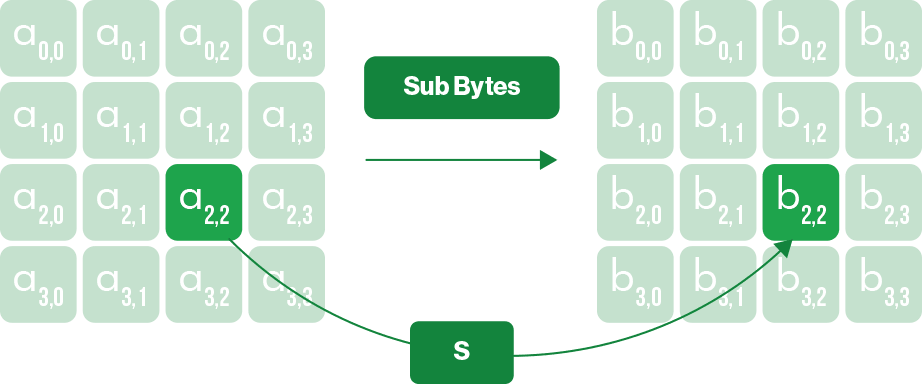
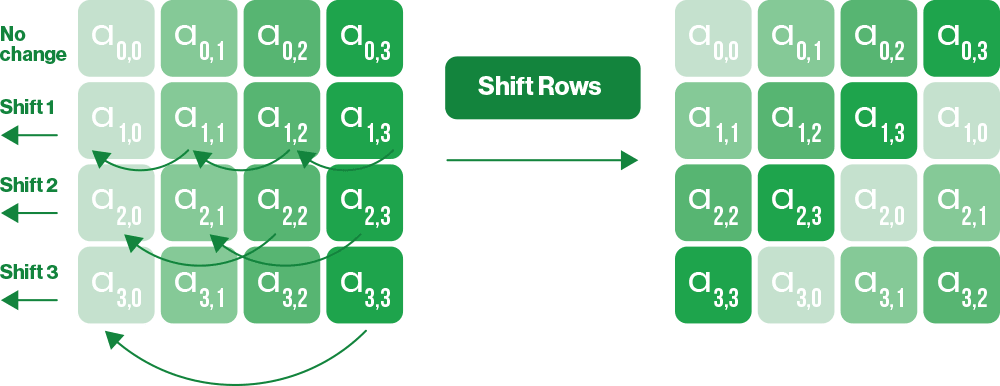
3. ShiftRows — each 128-bock of data consists of a 16-bit 4×4 block. This operation shifts each byte in a block row by a certain offset to the left.
4. MixColumns — an additional invertible linear transformation is performed on each column in the block.
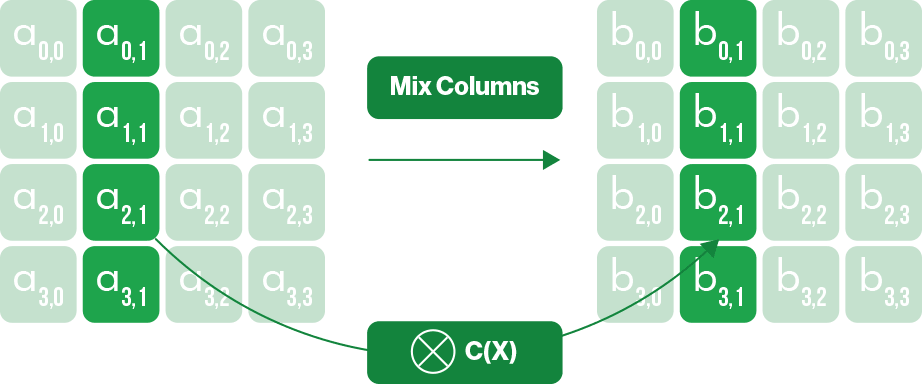
This series of transformations constitutes one round, which is then repeated on the data a set number of times. The number of rounds used depends on the key size:
- AES-128 — 10 rounds
- AES-192 — 12 rounds
- AES 256 — 14 rounds
To decrypt data, all the steps used to encrypt it are simply performed in reverse. This requires the original secret key so that you can reverse the process using each inverse round key.
Why AES-256?
As we have already discussed, it would take longer than the age of the universe to brute force AES-128 given current and foreseeable technology. Legendary cryptographer Bruce Schneier has even argued(nouvelle fenêtre) that AES-128 might be stronger than AES-256 thanks to it having a stronger key schedule(nouvelle fenêtre) (the algorithm that calculates all the round keys from the original secret key).
Yet AES-256 has become the de facto “gold standard” for symmetric-key encryption. Why? To an extent, optics plays a role. AES-256 simply sounds more impressive than AES-128 and “common sense” suggests it must be stronger.
But there is also a strong argument for increasing the key size to improve safety margins, so that encrypted data will remain secure even if some way is found to dramatically weaken the algorithm. This argument has become stronger as the need for post-quantum resistance becomes more pressing.
AES-CBC vs AES-GCM
Until fairly recently, AES was usually used in cipher block chaining (CBC) mode, where each block of plaintext is XORed with the previous ciphertext(nouvelle fenêtre) block before being encrypted. When used in CBC mode, a HMAC(nouvelle fenêtre) hashing algorithm such as HMAC-SHA256 is required to verify the data.
It is increasingly common, however, to see AES used in Galois/counter (GCM) mode, which uses the counter mode(nouvelle fenêtre) of encryption. The main advantage of this is that it uses the Galois field(nouvelle fenêtre) to verify data without the need for an outside algorithm. It is therefore more efficient than using a separate authentication algorithm that can have a high computational overhead.
Although AES-CBC with HMAC authentication is generally considered secure, CBC is potentially vulnerable to padding attacks(nouvelle fenêtre), such as POODLE(nouvelle fenêtre). GCM is not. Proton VPN uses AES-GCM in our OpenVPN encryption suite.
Final thoughts
There are modern secure alternative symmetric-key ciphers, such as Salsa20 and ChaCha20 (which is used by the WireGuard® protocol), but AES, and AES-256 in particular, has become the de facto standard for symmetric-key encryption.
This is fine, as AES is a strong and reliable cipher that is highly resistant to all known attacks. It’s also fast, although this is helped considerably by the AES-NI hardware acceleration(nouvelle fenêtre) built into many modern processors.
It should be noted that Salsa20 and ChaCha20 may both become more efficient in time, and may even come to benefit from hardware support, which may make these ciphers faster than AES in the future. Proton VPN now uses the WireGuard VPN protocol by default, which uses ChaCha20 as its symmetric-key encryption algorithm.



