Proton offers browser extensions for Proton VPN and Proton Pass(nouvelle fenêtre). Browser extensions are useful (and can be fun(nouvelle fenêtre)). And with more than 250,000 extensions available(nouvelle fenêtre) on the Chrome web store alone, they’re very popular.
But are they safe?
The answer is not always. That is why Google blocks approximately 1,800 malicious extensions uploaded(nouvelle fenêtre) to Chrome each month. In this article, you’ll learn why – and how you can know whether an extension can be trusted.
- What are browser extensions?
- Are browser extensions safe?
- How to use browser extensions safely
- How to uninstall browser extensions
- Recommended safe browser extensions
- So can browser extensions be trusted?
What are browser extensions?
Browser extensions are small software programs that you can add to your web browser to extend its functionality. Extensions allow you to customize your browsing experience by adding new features or modifying the behavior of websites. They can perform a wide range of tasks, such as blocking ads, managing passwords(nouvelle fenêtre), translating text, or enhancing privacy by encrypting data(nouvelle fenêtre) or preventing tracking.
For example, the Proton VPN browser extension(nouvelle fenêtre) encrypts your browser traffic with the VPN, without affecting speeds or the IP address of the other apps on your system. The Proton Pass browser extension(nouvelle fenêtre) autofills passwords, manages secure notes, and generates unique email aliases.
Are browser extensions safe?
Depending on the permissions they request (which we’ll discuss below), a browser extension can potentially access everything you do in the browser and relay it to a third party. This includes your:
- Browsing history (including pages visited, searches made, and even interactions on certain sites)
- Personal information (including usernames and passwords, email addresses, phone numbers, post address, and more)
- Payment and bank details
- Cookies and session data stored on your browser
- Download and upload activity (including sensitive documents, photos, or other personal data)
- Clipboard data that you’ve copied into or pasted from your browser
- Geolocation information
- Other apps or accounts that you’ve integrated with your browser
Malicious browser extensions can therefore do a huge amount of damage. As with mobile apps, browser developers have developed a permissions system, where extensions should only ask for the permissions they need. In theory, this limits the amount of damage a malicious extension can do. However:
- Many extensions genuinely require access to many permissions to function correctly (this notably includes VPN extensions and password extensions)
- Malicious apps often ask for permissions they wouldn’t need if they were trustworthy. But even if you can tell what permissions an extension needs, how many people actually check these before hitting the install button?
A recent study found that 51% of all installed browser extensions(nouvelle fenêtre) have the potential to cause extensive damage (note that most of these will be legitimate extensions that simply have the permissions necessary to do harm).
How to use browser extensions safely
1. Only download extensions from trusted developers
A big problem with extensions is that there is very little vetting of them. Basically, anyone can upload an extension to the Google Chrome Store, Firefox Browser Add-ons, and similar places.
One of the eye-opening facts exposed in the above study was that some 43,000 extensions on the Chrome web Store have anonymous authors.
It should go without saying that you should only download extensions from developers you trust.
2. Use open source extensions
Open source extensions can be independently audited by anyone qualified to ensure that they’re doing what they’re supposed to be doing, and nothing else. This is in sharp contrast to closed-source proprietary extensions, where you just have to trust the developer.
Most open source extensions haven’t been audited in this way, but the fact that they are an open book ready to be audited at any time is a strong indication that they can be trusted (although never a guarantee) .
3. Download only from reputable sources
As we’ve already discussed, many malicious extensions slip through the net. However, reputable browser extension repositories, such the the Chrome web Store and Firefox Browser Add-ons, do at least try to vet the software they host, and to remove extensions considered malicious.
4. Monitor changes in ownership or terms of service
A change in ownership or terms of service can mean that an extension that was trustworthy becomes a liability. A high-profile example(nouvelle fenêtre) of this happening involved the Stylish extension, once a popular and trusted tool for customizing website appearances.
Stylish was sold to a new company in 2017, and soon after the acquisition, the new owners modified the extension to secretly collect users’ complete browsing histories without proper user consent. This included every website visited and search queries, all of which is highly sensitive data. The extension was eventually removed from the Chrome and Firefox web stores after privacy experts and users raised concerns.
It’s therefore important to monitor any significant updates or changes in the privacy policies of extensions you use.
5. Monitor permissions
Browser extension permissions is the system specifically designed to make using browser extensions safer. But as we discussed above, in practice, it’s of limited use.
That said, you should keep an eye on permissions, as these can be a big red flag. After all, your ad-blocker extension shouldn’t be asking permission to access your camera and microphone.
6. Delete unused extensions
Browser extensions you’ve previously installed but don’t use eat up memory and present potential and unnecessary security risks. So just delete them.
How to uninstall browser extensions
After reading this article, you may wish to audit your browser extensions and uninstall any that are suspicious (or simply unused). Here’s a quick guide for how to do this on the most popular browsers(nouvelle fenêtre).
Firefox (desktop)
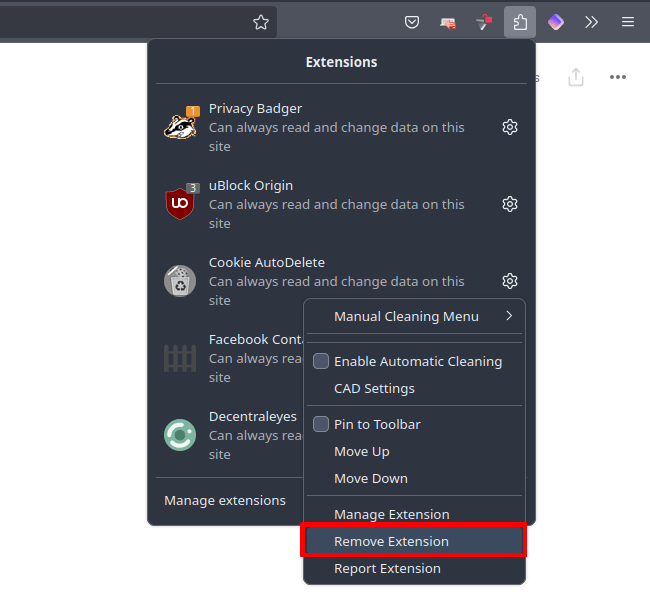
Open Firefox and select the Extensions menu bar icon (looks like a jigsaw piece). Click the ⚙ icon next to the extension you wish to uninstall → Remove Extension.
Firefox (Android)
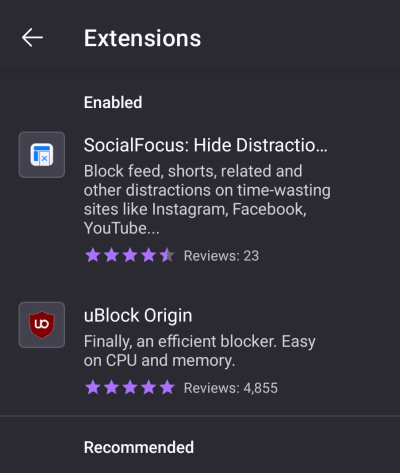
1. Open the Firefox app and go to ⋮ → Extensions → Extensions Manager and select the extension you wish to uninstall.
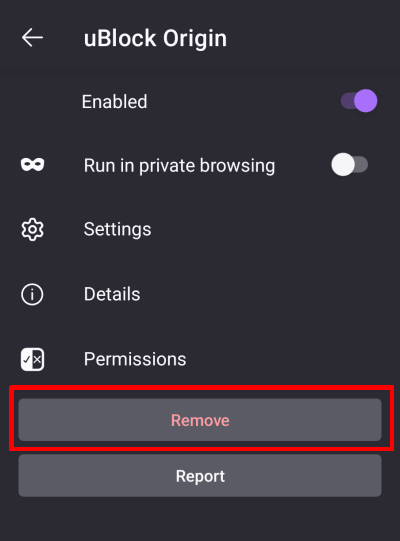
2. Select Remove.
Chrome (desktop)
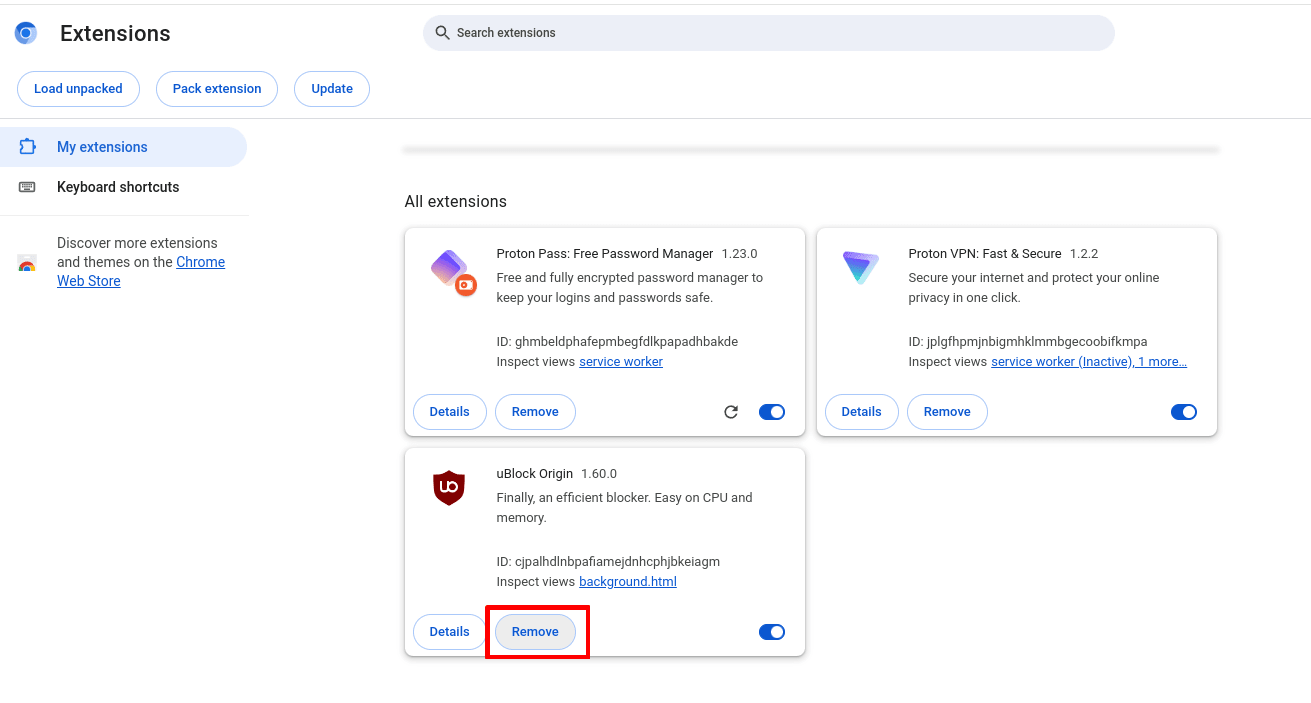
On Chrome and Chromium, go to ⋮ → Extensions → Manage extensions → the extension you wish to uninstall → Remove.
Brave (desktop)
Open Brave and go to ☰ → Extensions → the extension you wish to uninstall → Remove.
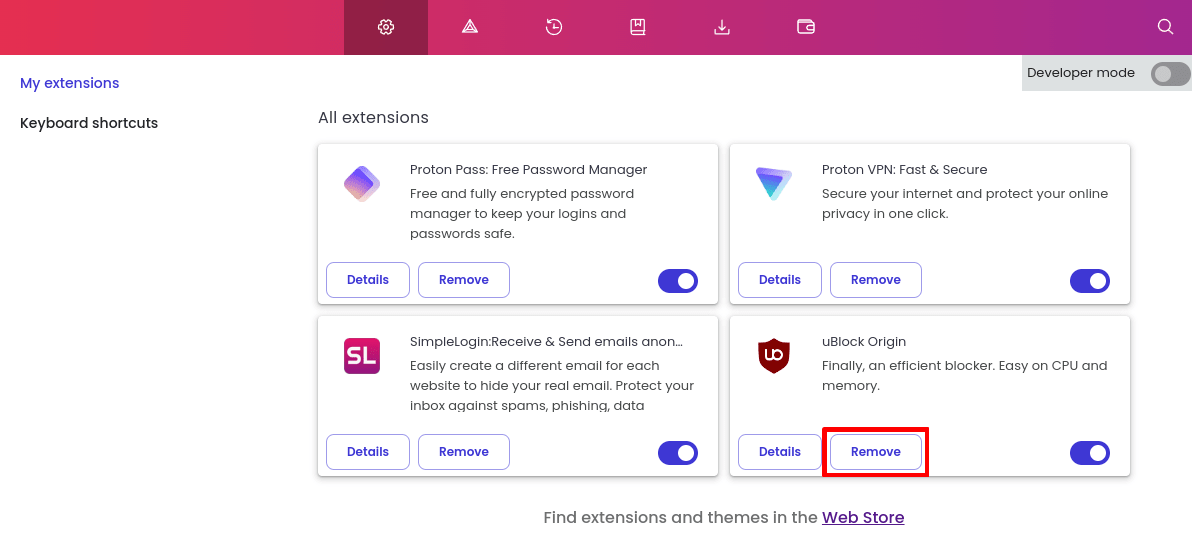
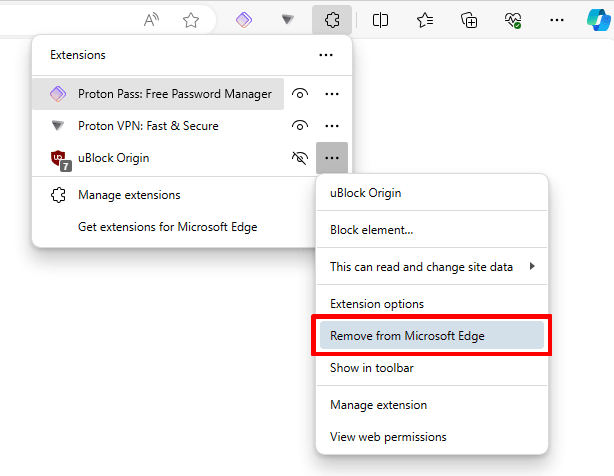
Edge for Windows
Open Edge and select the Extensions menu bar icon (looks like a jigsaw piece). Click the ⚙ icon next to the extension you wish to uninstall → ⋮ → Remove from Microsoft Edge.
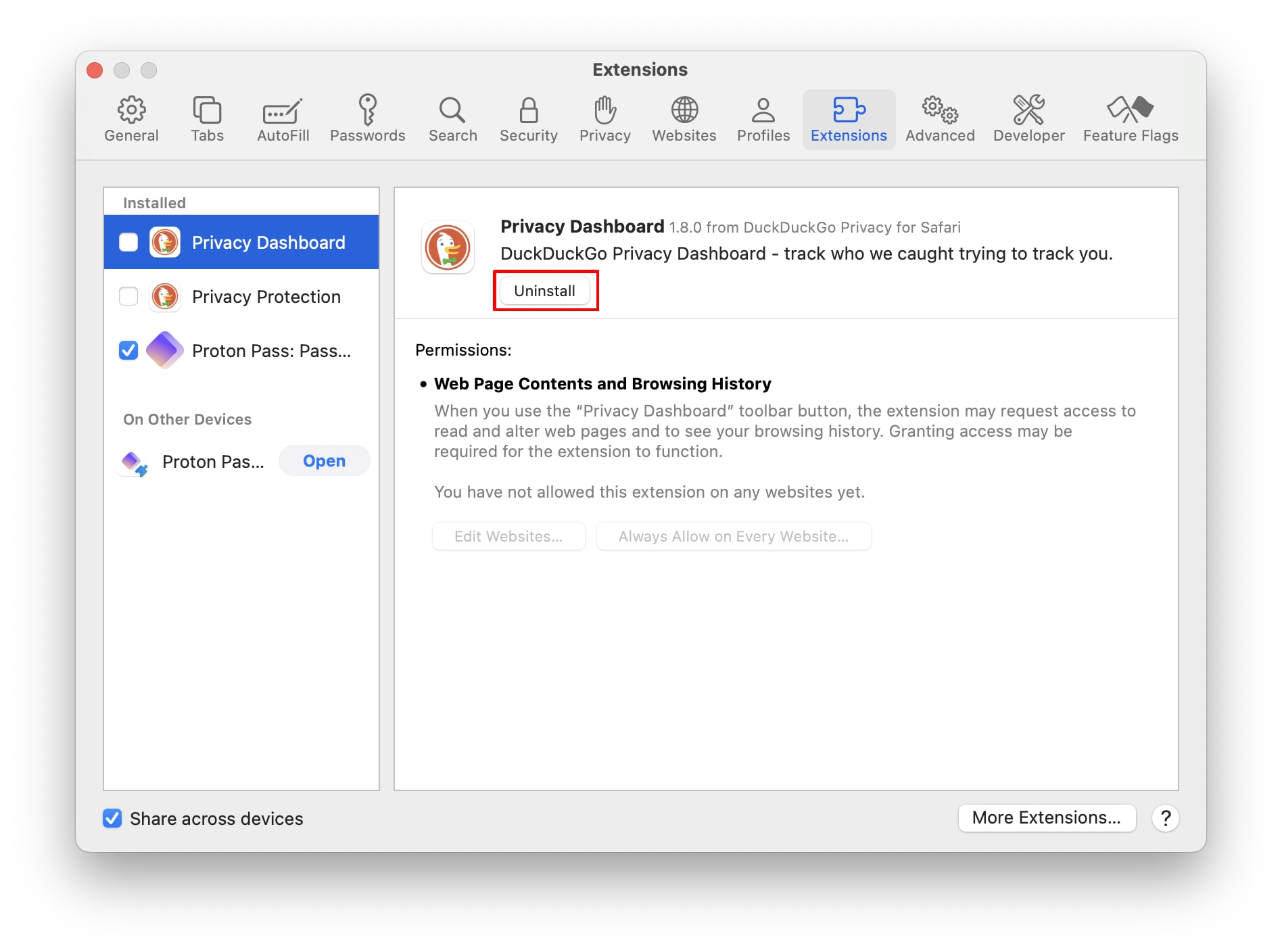
Safari for macOS
Open Safari and go to the macOS menu bar → Safari → Settings… → Extensions tab → the extension you wish to remove → Uninstall.
Recommended safe browser extensions
The following browser extensions are open source and developed by individuals or organizations widely regarded as being trustworthy. However, other than our own software, Proton VPN has no inside knowledge about these extensions, has not audited them in any way, and takes no responsibility if you choose to install them.
As a company with a mission to make privacy the default for everyone, we’ll focus on extensions that make your online browsing safer and more secure.
Proton VPN
Proton VPN is a Swiss-based no-logs VPN service trusted by millions of journalists, activists, and ordinary people around the world. With our browser extension for all major browsers, you can protect your browser traffic with the VPN, without affecting speeds or the IP address of the other apps on your system.
For example, you can browse privately without affecting ping rates for online games. Or you can stream from another country in one browser while shopping for the best local deals in a different browser. It’s also ideal for browsing privately on low end devices and on devices where you don’t have the admin rights to install a full VPN app.
Unlike most open source browser extensions, the Proton VPN browser extension has been fully audited(nouvelle fenêtre) by third-party security professions. Our no-logs infrastructure has also been audited.
Proton Pass(nouvelle fenêtre)
Proton Pass is designed to securely store your passwords, notes, and other sensitive data, while protecting your privacy with end-to-end encryption. This ensures that only you can access your information, and not even Proton can see your data.
The browser extension (for all major browsers) can save and autofill your passwords, create secure passwords(nouvelle fenêtre) or passphrases, and generate 2FA authentication codes. Its built-in hide-my-email feature can create disposable email aliases, allowing you to maintain your privacy and avoid spam when signing up for new online services.
As with all Proton products, the Proton Pass browser extension is open source(nouvelle fenêtre) and has been independently audited(nouvelle fenêtre).
Privacy Badger (nouvelle fenêtre)
Created by the Electronic Frontier Foundation(nouvelle fenêtre) (EFF), Privacy Badger focuses on protecting your privacy by automatically blocking invisible trackers that follow you around the web. Unlike traditional ad blockers (including Proton VPN’s Netsheild ad-blocker feature), Privacy Badger learns over time which domains are tracking your behavior and blocks them accordingly.
Privacy Badger doesn’t rely on predefined filter lists. Instead, it observes third-party tracking behaviors as you browse. When it detects the same trackers on multiple sites, it automatically blocks them. It also blocks third-party tracking cookies, but allows ads that don’t track you.
Privacy Badger and Proton VPN’s Netshield ad-blocker feature complement each other, and can be used together.
Cookie AutoDelete(nouvelle fenêtre)
The problem with cookie-blocking software (including browser extensions) is that cookies are often used by websites for legitimate purposes, such as keeping you logged in. In some cases, blocking cookies can even “break” websites that you want to visit.
The Cookie AutoDelete extension helps balance privacy and usability by allowing a website to place cookies on your browser when you’re visiting the website, but then automatically deletes them after you close a tab or window.
Decentraleyes(nouvelle fenêtre)
Websites often rely on third-party content delivery networks(nouvelle fenêtre) (CDNs) to host essential resources, but these CDNs can track you across different sites. Decentraleyes hosts popular web libraries used by CDNs locally, so when a web site requests a resource from a CDN, it intercepts the resource and loads it locally.
This helps maintain your privacy by blocking this kind of tracking, while still ensuring the websites you visit function properly. It can also help web pages to load faster.
So can browser extensions be trusted?
Yes. So long as their developer can be trusted.
The bottom line is that (as with most other software you run on your system) malicious browser extensions can cause a huge amount of damage, and the safeguards put into place by browser developers are of very limited use in preventing this.
However, if you download browser extensions from trusted stores that are verified to belong to trusted developers (open source can help determine which developers are trustworthy), there is little to worry about.







