Deep packet inspection (DPI) is a method of examining data packets that pass through a network so that the traffic type can be identified. This information can then be used to block unwanted traffic.
The technique is commonly used in firewalls, intrusion detection systems, and other network security systems.
Unfortunately, the same analysis techniques used to protect private networks can also be used by governments and other organizations to monitor internet traffic and censor online dissent.
Using DPI, organizations can examine packets as they pass through a network to understand their purpose. This allows them to block or restrict access to certain websites, applications, and services.
Using a VPN prevents this kind of analysis, as the packets are encrypted. But the VPN protocol itself can often be identified by DPI. This allows repressive governments (and occasionally other organizations, such as offices and campuses) to effectively block access to VPN services, even when attempts are made to hide (obfuscate) the fact that a VPN is being used.
In this article, we look at how deep packet inspection works, with a focus on how repressive governments use it to impose censorship restrictions. We also look at how DPI affects virtual private networks (VPNs) such as Proton VPN, which are designed to overcome such restrictions.
- What is a data packet?
- How packet analysis works
- Simple packet analysis
- Deep packet inspection
- DPI and government censorship
- How VPNs works
- Simple VPN blocks
- Simple VPN anti-censorship tactics
- How DPI is used to detect VPNs
- VPN obfuscation
What is a data packet?
When data is sent over a network (such as the internet), it’s divided into small portions. These small portions are called data packets (or just packets).
The Internet Protocol(yeni pencere) uses data packets to help ensure information sent across the web reaches the correct destination. When all the packets making up a dataset (such as an image or the contents of an email) reach their destination, they’re reassembled.
The actual data contained in a packet is called its “payload”. Each packet also has a header that contains metadata explaining things like where it’s going and where it came from.

All data transmitted over the internet is sent in packets.
How packet analysis works
An organization performing any form of packet analysis must first obtain packets to analyze. This can be done in many ways, but port mirroring(yeni pencere), physical network taps(yeni pencere), and WiFi sniffing(yeni pencere) are common tactics. Once an organization has access to packets, it can analyze them in various ways.
Simple packet analysis
The easiest (and cheapest) way for an organization to implement blocks on network traffic is to examine the information contained in packet headers. This allows these organizations to block packets based on the ports they use or their destination IP address.
Deep packet inspection
The problem with simple packet analysis for organizations that wish to censor the internet is that it’s easy to bypass simply by changing the destination IP address or the port numbers used. This is because simple packet analysis doesn’t look at the data (the payload). Deep packet inspection analyzes the entire packet, including the payload.
How does deep packet inspection work?
DPI techniques include:
- Signature-based detection — Compares packets against a database of known malicious or unwanted traffic patterns
- Anomaly-based detection — Looks for patterns or behaviors that deviate from normal network traffic
- Protocol analysis — Examines the structure and format of packets to identify which protocol is in use
- Content inspection — Examines the actual data contained in the payload, such as the text of an email, to identify and block specific keywords or phrases
- Behavioral analysis — Examines the behavior of network traffic over time, such as the frequency of connections to a particular server or the amount of data transferred, to identify and block unusual activity patterns
DPI and government censorship
Repressive governments around the world want to limit their citizens’ access to independent information, their capacity to interact with the international community, and their ability to express viewpoints critical of the regime.
This is part of the reason that internet blackouts continue to become more common(yeni pencere). But these blackouts are incredibly costly for any country that regularly relies on the internet (so basically every country except for North Korea). The internet shutdowns from 2022 cost the global economy roughly $24 billion(yeni pencere).
The solution to this dilemma in places such as Russia, China, Iran, and Egypt is to make the internet available but block websites and apps they don’t want their citizens to access. On a basic level, this is quite simple to achieve. All governments have to do is instruct their domestic internet service providers (ISPs) to block connections to certain IP addresses.
The problem with this approach is that technologies such as virtual private networks (VPN) make it easy for more tech-savvy citizens to bypass these blocks, so governments deploy DPI to detect (and block) VPN use.
Read more about internet censorship
How VPNs works
A VPN creates an encrypted connection between your device and a VPN server run by a VPN service such as Proton VPN. The VPN app then routes all connections from your device through this “VPN tunnel”. This includes DNS queries, which your VPN provider resolves rather than your ISP (as usually happens).
Because the data sent through the VPN tunnel is securely encrypted, your ISP (and, by extension, your government) can’t see your data’s content or which websites you visit. All it can see is the IP address of the VPN server you connected to.
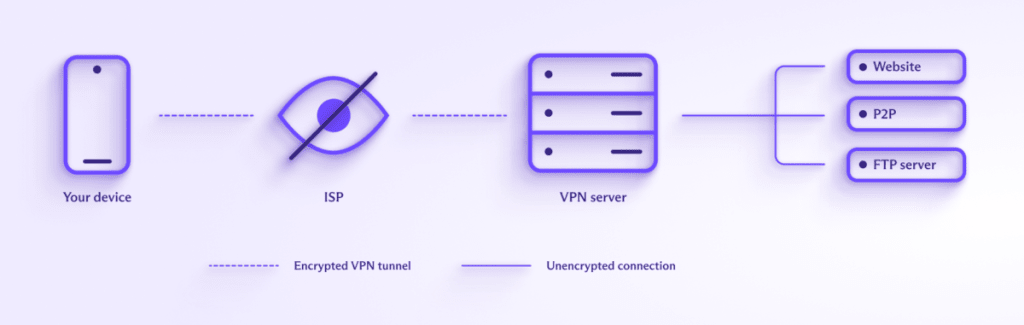
Learn more about how a VPN works
What an ISP can’t see, it can’t block, which is why VPNs are effective anti-censorship tools. Repressive governments, of course, know this, so their usual response is to try to block access to VPNs.
Simple VPN blocks
The simplest way to do this is to block access to VPN services’ websites. Such blocks are usually easy to evade — for example, by distributing VPN software such as Proton VPN’s Android APK file via an encrypted messenger or social media channels.
It’s also possible to perform simple packet analysis on packet headers using the following methods:
Destination IP address analysis
Authorities can examine the destination IP address of packets and match them against a list of known VPN server IP addresses. Armed with such a list, it’s easy for an ISP to block access to all of a VPN service’s servers.
With the resources available to most governments, it’s not difficult for them to compile these lists themselves. But they don’t really need to because many commercial services do good business by compiling and selling such lists.
Port analysis
DPI can examine the destination port number of packets and match them against a list of known VPN port numbers
For example, by default, OpenVPN uses UDP port 1194, while WireGuard® uses UDP port 51820.
SSL/TLS certificate analysis
By examining packets’ SSL/TLS certificates(yeni pencere), authorities can match them against a list of known VPN SSL/TLS certificates and detect if people are using a VPN.
Simple VPN anti-censorship tactics
Simple packet analysis is a common censorship tactic because it’s easy and cheap. It’s also fairly easy for a VPN service to bypass using the following methods:
VPN over TCP
HTTPS(yeni pencere) is the encryption standard that secures the web, making possible much of what we take for granted being able to do on the internet. This includes securing all online financial transactions, such as online purchases and managing your bank account online.
HTTPS uses TCP port 443, so VPN services often also run their VPN protocols over TCP port 443. This makes it difficult to simply block this port without effectively shutting down the entire internet.
OpenVPN has built-in support for TCP, making it a popular choice among VPN services using this tactic. WireGuard is usually run over UDP, but Proton VPN has also developed a way to run WireGuard over TCP.
Learn more about the difference between UDP and TCP
VPN over TCP can effectively evade simple protocol analysis, but more advanced DPI techniques can easily spot the difference between HTTPS and VPN packets.
Changing port numbers
Although VPN protocols default to using expected ports, most can be run over almost any port (except for ports reserved for specific functions). So a simple (but often effective) anti-censorship technique is to run VPN protocols over non-standard ports.
Proton VPN’s Smart Protocol feature detects when a connection is blocked and automatically switches between VPN protocols and port numbers to find combinations that aren’t blocked.
Alternative routing
An unusual anti-censorship tactic used by Proton VPN is alternative routing(yeni pencere). If access to any Proton service is blocked (including to the Proton VPN website), we try to route the connection through third-party server networks that are unlikely to be blocked (such as AWS).
VPN bridges
Destination IP address analysis is a challenging attack vector to overcome, but some VPN services mitigate the issue with VPN bridges. These allow them to evade censorship by providing alternative entry points to the VPN network that are not publicly listed or blocked by censors.
VPN services can achieve this by using a technique called “bridge relaying” or “bridge mode.” This is when a VPN provider runs a few “bridge relays” that it doesn’t publicly list and only provides to people who need to defeat censorship. These bridge relays act as a secret entry point to the VPN network and can be used to bypass blocks on VPN traffic.
Another way VPNs use bridges is by allowing people to connect to the VPN network through a “bridge VPN”, which is when a VPN connection is established between your device and a VPN server that censors haven’t blocked. You can then use this bridge VPN to connect to the main VPN network and access blocked content.
How DPI is used to detect VPNs
Online censors and internet users have been locked in an arms race since the web’s earliest days. ISPs started to block ports, so people started using non-standard ports. Repressive governments responded by using DPI to determine what traffic was doing on open ports, which encouraged people to use VPNs to defeat the DPI. In turn, governments developed more sophisticated DPI techniques, and so on.
DPI is hard to bypass because it examines the entire packet to identify VPN traffic in a variety of ways. These include:
Protocol analysis
This examines the structure and format of packets to identify which protocol is in use and detect if the packets are using a VPN protocol like OpenVPN, PPTP, L2TP, or IKEv2.
Packet size analysis
Unusual packet sizes may indicate the use of a VPN.
Behavioral analysis
DPI can examine network traffic behavior over time to identify patterns that may indicate the use of a VPN. For example, if there is an unusual spike in traffic to a specific server or a sudden change in the location of IP addresses, it might indicate that a VPN is being used.
VPN obfuscation
As the next step in the arms race for an uncensored internet, some VPN services have developed custom VPN protocols resistant to DPI techniques. For example, we developed the Stealth protocol for Proton VPN.
This new protocol combines various open-source technologies, most notably using obfuscated TLS tunneling over TCP to look like HTTPS in a more censorship-resistant way than simply running VPN over TCP port 443.
Stealth has helped millions of people overcome VPN blocks in places such as Iran and Russia, but we can’t guarantee its effectiveness against advanced DPI techniques.
Final thoughts
Deep packet inspection can be sophisticated and poses an ongoing challenge to our work of bringing the open internet to everyone. But we founded Proton VPN to face challenges exactly like this, and our engineers are always developing new anti-censorship tools and features.
We’re locked in an arms race with some of the globe’s most repressive governments, and the stakes could not be higher. Repressive governments rely on keeping tight control over the information their citizens can access, who they can talk to, and what they can say to their fellow citizens and the rest of the world.
But we believe everyone has the right to access independent reporting, associate with whomever we please, and criticize injustices and abuses of power. We’re fighting to ensure everyone has access to these fundamental human rights.
Proton VPN was founded to help fight for a world without censorship, which is why we offer a 100% free VPN service. With Proton VPN, anyone can access the free and open internet. We’re proud that activists, journalists, and ordinary people around the world turn to Proton VPN in times of turmoil.
If you live in a repressive country, our service is here to help. If you don’t, you can support our mission to make the uncensored internet available for everyone by signing up for a Proton VPN Plus plan.








