The internet was founded on the idea that it would be a free and open space for expression. Unfortunately, internet censorship is becoming more common worldwide. But while technology provides the tools for Internet censorship, it also offers ways to fight back. We explain what internet censorship is, how it works, and how to defeat it.
What is internet censorship?
Where does censorship happen?
What is censored?
Internet censorship examples from 2021
Internet censorship around the world
What countries have no internet censorship?
How does internet censorship work?
The best way to defeat censorship online
What is internet censorship?
Simply put, internet censorship is the control or suppression of what content can be published, communicated, or accessed on the internet.
Where does censorship happen?
Censorship can be applied at any of several points when you are browsing the internet. Anytime you try to access a website, your internet traffic will be handled by your:
- Device (e.g., your smartphone, your work laptop, etc.)
- Local network (e.g., your home WiFi, your work WiFi, etc.)
- Internet service provider (ISP)
- Search engine of choice
This is not a complete list of all the places censorship can be applied, but it represents the most common examples enforced by governments.
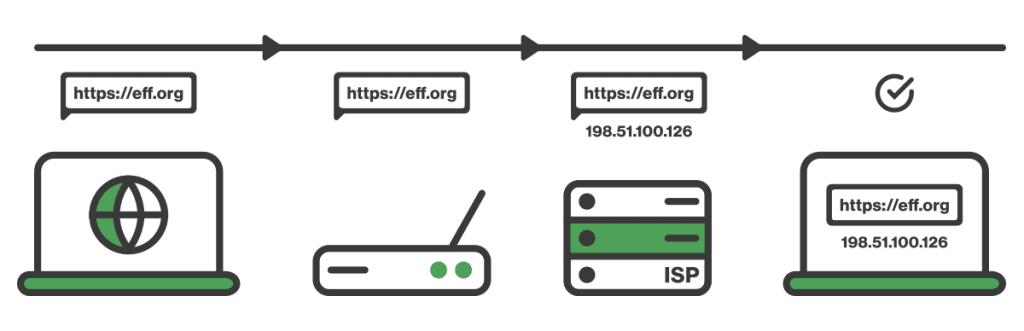
Censors can place blocks on content at any one of these steps.
- Blocks on your device: Software can be installed on a device that enforces blocks locally on your device. This can include parental controls, network security software, or malware.
- Blocks on your local network: The person running your local network can implement blocks as well. You typically see these types of blocks on university or workplace WiFi networks.
- Blocks at the ISP and national level: An ISP connects your device to the rest of the internet, meaning it has broad power to block specific websites or the entire internet. A government can force ISPs to carry out censorship for it, effectively blocking the censored content for everyone in that country.
- Blocks implemented by search engines: Since many people rely on search engines to find the content they are looking for, governments can also require these search engines to block certain queries or only return government-approved results.
What is censored?
This depends entirely on who is applying the censorship. You might apply child controls on your child’s phone to block pornography, your work WiFi might block torrenting services, and your national ISP might block access to foreign websites that are suspected of propaganda.
Other common targets for censorship include news organizations, social media platforms, like Twitter and Facebook, or messaging services, like WhatsApp or Telegram, as they provide quick, efficient ways to spread information and organize.
This post focuses on the government censorship of the internet at the national/ISP level because it is the most impactful in terms of the number of people affected.
Internet censorship examples from 2021
Censorship takes many different forms and can be implemented briefly or turned into a durable, lasting condition of the internet. Examples of the different types and levels of censorship from 2021 include:
- China’s Great Firewall(yeni pencere), which was established in the mid-2000s, blocks access to thousands of western websites. It has steadily been increasing its censorship, blocking all language versions of Wikipedia(yeni pencere) since 2019. The Chinese government also exercises tight control of its national internet to swiftly delete posts that are critical of Xi Jinping or the Chinese Communist Party.
- In January, in the run-up to national elections (a pretext many regimes use to censor the internet), the Ugandan government ordered the national internet provider to shut down internet access entirely throughout the country. Ugandans were without internet(yeni pencere) for a little over five days.
- During mass protests in July, the Cuban government blocked access to several social media platforms(yeni pencere), including Facebook, Instagram, WhatsApp, and Telegram, for two days.
The last example is the most representative of most internet censorship. Building an entirely separate national internet is expensive and difficult to maintain, and shutting down a country’s internet entirely, even for a short time, can lead to massive economic losses. Comparatively speaking, it is easier to block news articles that are critical of the government and prevent people from organizing on social media technically and politically. Fortunately, these types of blocks can be defeated.
Internet censorship around the world
According to Freedom House’s 2021 assessment of Freedom on the Net(yeni pencere) (FOTN), internet freedom has declined for the 11th straight year.
This decline has been largely driven by governments’ abuse of problematic regulations that allow them to remove critical or unflattering content. This is expected from authoritarian countries like China, Iran, and Myanmar (which occupy the bottom three rankings in the FOTN report), but this type of online censorship is also becoming more common in democracies like India and Indonesia.
What countries have no internet censorship?
According to the 2021 FOTN report, the four countries with the highest freedom scores are:
- Iceland
- Estonia
- Canada
- Costa Rica
While this doesn’t mean that these countries have no censorship, they all have strong records of protecting freedom of speech and expression on the internet and generally try to make the internet as accessible as possible.
How does internet censorship work?
Internet censorship is usually implemented through one of the following methods. We briefly explain how they work and how you can bypass them.
Domain Name System (DNS) filtering and redirection
Your DNS queries are resolved by DNS servers operated by your ISP by default. This means your ISP can refuse to resolve requests for domains hosting censored content on their DNS servers, making the site non-accessible to browsers and causing them to return an incorrect IP address.

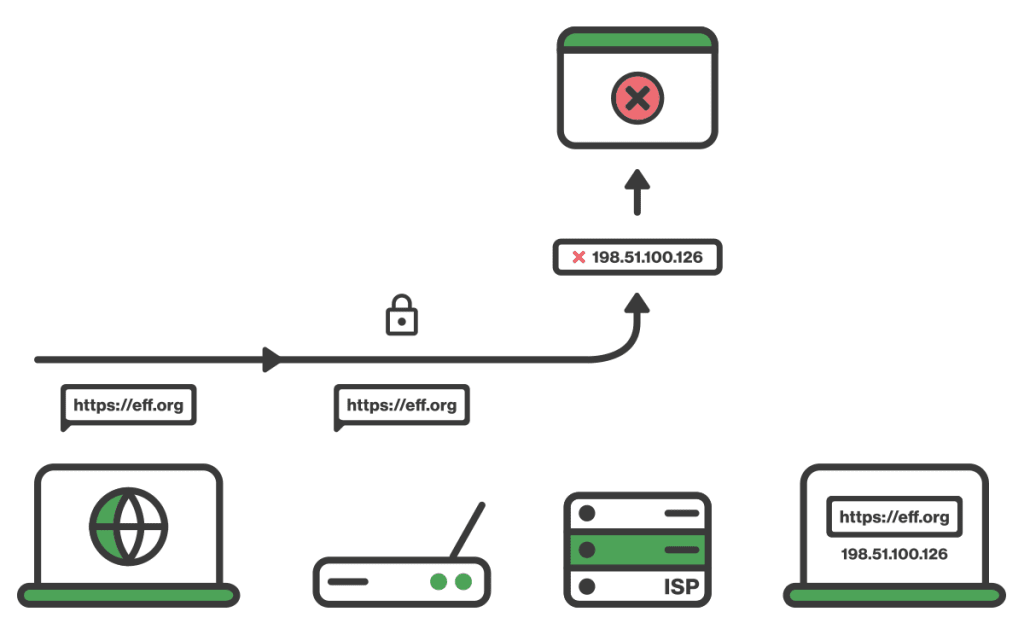
Internet Protocol (IP) address blocking
IP address blocking is a fairly simple way of censoring specific websites or platforms. First, the censor creates a list of the IP addresses or TCP/IP port numbers of all the websites to be blocked. Then, as browsers request to reach a website, the ISP will check each request against the list. If there is a match, the ISP will drop the connection.
Any websites on the same shared hosting server will share the same IP address and also be blocked as collateral damage. IP address blocking is the most common way to geo-block copyrighted content, like music or movies.
By blocking certain TCP/IP ports, censors can even block applications by their type of traffic. This is a common way to block VPNs.
Search engine blocks
Search engines have immense power to shape web traffic, which is why governments often threaten to block their service unless they agree to filter out objectionable content. Since this type of censorship relies on the cooperation of the search engine operator, it can only be enacted by national governments. Government censors will define what content is objectionable and must be removed from search results. Safe Search on Google is an example of a search filter, though its purpose is to block inappropriate material from children.
Deep packet inspection (DPI)
DPI is an advanced form of censorship used by certain states with strict internet controls. It works by inspecting the metadata of packets sent between servers to determine what type of traffic is being transferred. Authorities can then log, re-route, or block that traffic based on what they find. This is one of the few methods effective at blocking encrypted traffic. Sophisticated firewalls using DPI (such as the Great Firewall of China) can even detect and block VPN or Tor traffic.
The best way to defeat online censorship
Proton VPN is the best way to defeat the most popular types of online censorship.
A VPN creates an encrypted tunnel between your device and the VPN server. Your internet traffic, including your DNS queries, is then routed through the VPN server and not traceable back to you. This prevents your ISP from seeing which websites you are trying to access and prevents it from applying any blocks. You can then connect to a server in another country (like the countries with high FOTN scores) where that content or service is not blocked.

This will let you defeat:
- DNS filtering
- IP address blocking
- URL filtering
- Search engine blocks
Proton VPN is a better option than other VPNs because:
- We have developed advanced features that allow Proton VPN to bypass attempts to block or censor VPN services themselves.
- We provide a free VPN(yeni pencere) with no logs, no ads, no data limits, and no speed limits.
- We are based in Switzerland and subject to strong Swiss data privacy laws.
- We are a transparent, trustworthy VPN service run by the creators of Proton Mail(yeni pencere), the world’s largest encrypted email service.
Learn why Proton VPN is the best option to defeat censorship
Other solutions to censorship
If you know you are facing DNS filtering, you can simply switch who handles your DNS queries. Quad9 is a popular DNS provider that can help you bypass blocks. While you will need to reconfigure your operating system to use a new DNS provider, Quad9(yeni pencere) offers a thorough setup guide.
To defeat advanced censorship, you can turn to the open-source software Tor. The Tor browser(yeni pencere) encrypts your internet connection and routes it through different Tor servers (called nodes) on the Tor anonymity network. The website will only see the IP address of the last Tor server pinged and not the IP address of your device(yeni pencere). Tor can be slow and cumbersome to work with, but it remains an excellent option for anyone trying to access censored sites or anonymize their web activity.

If even Tor fails because your ISP is blocking access to known Tor nodes, you can use a Tor bridge with a pluggable transport. A Tor bridge is a Tor node that is not listed in the main Tor directory. Since bridges are unknown, an ISP cannot block their IP addresses. However, if a government used DPI, it would be able to find the Tor bridge. To prevent this, you can add a pluggable transport to your connection. A pluggable transport transforms your Tor traffic into something more innocent or random looking, like regular HTTPS traffic.
Learn how to use Tor bridges and pluggable transports (yeni pencere)
Tools like Proton VPN and Tor play an important role in keeping the internet free and open and help you stay one step ahead of those that would deny you access to information. As the poet Yevgeny Yevtushenko said, “When truth is replaced by silence, the silence is a lie.” We hope you use these tools to fight through the silence and find the truth.







