Privacy advocates often refer to an “encrypted tunnel” or “VPN tunnel” that protects your data when you use a VPN. But what exactly is a VPN tunnel?
The term “tunnel” is a metaphor. Apart from the fiber optic cables tying the internet together, your data isn’t really traveling through a tunnel. But VPNs do protect your data as it travels across the internet.
This article explains in simple terms what “VPN tunnel” means and how it works. It also provides an overview of different VPN protocol types used to create VPN tunnels and includes a diagram to help you understand what happens when you use a VPN.
What is a VPN tunnel?
A VPN tunnel refers to the encrypted connection between your internet-connected device and a VPN server. This prevents hackers and governments from inspecting the data you send and receive over the internet.
VPNs can work on any device that connects to the internet and can run a VPN app, including your smartphone, computer, and some smart TVs. All you have to do is download a VPN app to your device and follow the instructions to connect to a VPN server.
When you connect to the VPN server, an encrypted connection is negotiated between your device and the VPN server. This encrypted connection is often referred to as a VPN tunnel.
How does a VPN tunnel work?
Here’s a VPN tunnel diagram to help explain:
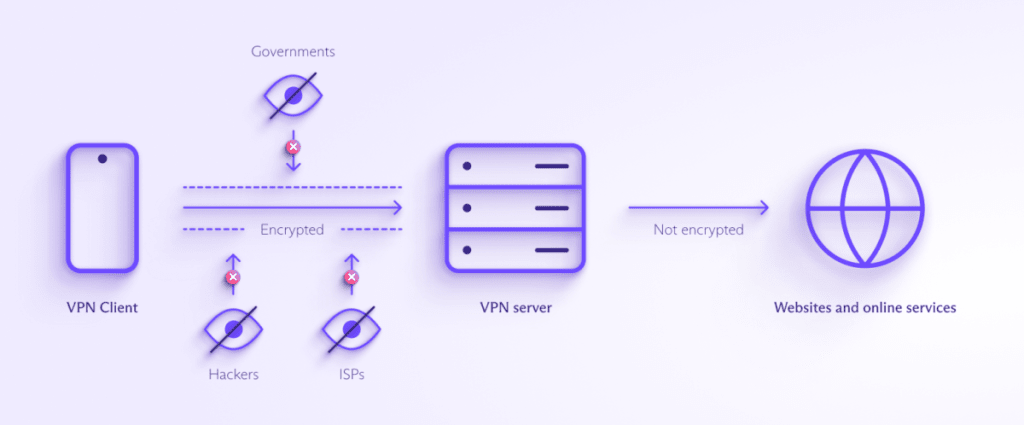
A VPN server is a computer operated by your VPN provider. When you establish a VPN tunnel, your internet connection is encrypted between your device and the server.
There isn’t an actual tunnel: Rather, the data that makes up the websites you visit, the emails you send, and the photos and videos you share is broken up into smaller pieces called packets. The packets are encrypted using an algorithm that converts the information from readable text to unreadable ciphertext(новое окно). Only the VPN app and VPN server can decrypt those packets using a secret key.
Read a more technical explanation of what a VPN is
Data exchanged between the VPN server and the final destination, such as a website you’re visiting, is not encrypted by the VPN. These days, it’s usually encrypted using standard web encryption (TLS(новое окно)), but this isn’t always the case. Now, your internet traffic appears to originate from the VPN server, even if the server is in another country.
This means your true location is masked. Websites can’t trace the data beyond the VPN server back to you. This ability to make it appear as though you’re accessing the internet from another country makes VPNs very effective at bypassing web censorship.
It’s also important to note that you should only use VPNs that you trust. When you connect to any VPN, the VPN provider can see the same kind of data that your ISP could when not using a VPN. It handles your internet connection to whatever website you visit, which is why it’s critical that you only use trustworthy VPNs that have an independently verified no-logs policy.
Read about the independent audit of Proton VPN’s no-logs policy
Benefits of using a VPN tunnel
Many people connect to a VPN every time they use the internet because it offers so many privacy and security benefits.
Privacy
Because your internet traffic is encrypted before it leaves your device, your online activity is inaccessible to anyone monitoring the internet. Technically, anyone can monitor internet traffic. Those who regularly do include:
- Websites and trackers — Companies love to monitor who you are and what you do online so they can profit from your data. A VPN tunnel prevents them from seeing your true location, the type of device you’re using, and what websites you visit. (Note: Websites can perform other types of tracking, so you should also be sure to use a private browser(новое окно) and be careful about the info you actively submit to any website.)
- Governments — In the last 20 years, mass surveillance has been deployed against entire populations in many countries. This includes the inspection of data packets as they travel across the internet. Using a VPN prevents governments from engaging in many types of invasive spy techniques.
- Internet service providers — Your ISP or your cell phone carrier can see all your web activity. They can use this data for their own purposes or turn it over to the government in response to a subpoena. But your ISP can’t monitor data you encrypt with a VPN.
- WiFi administrators — Whenever you connect to the WiFi at an airport, cafe, or even an Airbnb, you are exposing your online activity to the owner of that WiFi network. Some public WiFi operators then sell your data to advertisers and analytics companies. When you establish a VPN tunnel before browsing the web, all the WiFi operator can see is that you’re connected to the VPN server.
Security
Often where there’s privacy, there’s also security. VPN tunnels reduce the amount of your data that’s visible to others — and that includes hackers.
Most websites are now equipped with HTTPS, which encrypts all data sent and received between your device and the website’s servers. But not every website(новое окно) does. This leaves your traffic vulnerable to interception, including any passwords or other sensitive data you enter.
A larger concern is that the data collected from you by any of the above trackers will suffer a data leak that exposes your information. A VPN will not defend against all (or even most) leaks, but it is one more layer of protection in an information space designed to extract your data.
Anti-censorship
Perhaps the most functional benefit of a VPN tunnel is its ability to transport you anywhere in the world — virtually at least.
If you are in a location where the government or internet service provider is blocking websites, you can use a VPN to bypass that censorship. Many authoritarian governments censor news sites and encrypted communications platforms as a means of imposing control over the population. A VPN is a critical tool for preserving freedom.
VPN tunnels can also help you access accounts that have geo-restrictions while you’re traveling. For example, many streaming sites are not accessible in certain countries. If you’re traveling abroad, you can connect to a VPN server back home to log in to your account.
Proton VPN users can access many popular streaming sites by connecting to a Plus server in that country.
Other benefits of VPN tunnels
There are other benefits of a VPN that are very important in certain use cases:
- Prevent peers from seeing your real IP address when using P2P file sharing (BitTorrent).
- Access your workplace network remotely. (Consumer VPNs typically don’t offer this feature but rather it’s another benefit of VPN technology generally.)
- Avoid bandwidth throttling — ISPs sometimes slow-lane network(новое окно) web traffic belonging to rival services. With a VPN, what they can’t see, they can’t block.
VPN tunnel types
VPN tunnels are just encrypted connections between your device and the VPN server. But different tunneling protocols can be used to create this VPN connection. The protocols are basically a set of instructions the computers must follow to establish the encrypted connection, maintain it, and transmit your internet traffic inside it.
VPN protocols have different strengths and weaknesses. Some are faster or slower, more stable or less stable, or more resistant to attacks.
Read a more in-depth explanation of which VPN protocol is the best
Here’s a quick overview:
- Point-to-Point Tunneling Protocol (PPTP) — An older VPN protocol with several known vulnerabilities. You shouldn’t use a VPN service that runs on PPTP.
- L2TP/IPSec — Layer two tunneling protocol (L2TP) and Internet Protocol security (IPSec) are two protocols that often work together to negotiate the server connection and manage the encryption, respectively. This is a more secure system than PPTP, but it may have vulnerabilities and generally isn’t as fast or stable as newer protocols.
- IKEv2/IPSec — Internet key exchange version two (IKEv2) is fast, stable, and secure when used with IPSec. There are no known security vulnerabilities. The main drawback is that it’s easier for government censors to block than some newer protocols.
- OpenVPN — OpenVPN is a safe choice: fast, stable, secure, and difficult to block.
- WireGuard® — WireGuard is the newest VPN protocol we use and recommend. It incorporates several cutting-edge technologies, including elliptic curve cryptography(новое окно). And it’s the fastest VPN tunneling protocol available. We’ve gone a step further and configured it to run on ports used by normally encrypted internet traffic, making it more difficult to block.
- Stealth — Stealth is a VPN protocol developed by Proton VPN based on WireGuard and released in 2022. Stealth has a number of anti-censorship improvements over WireGuard, including an extra layer of TLS encryption.
What VPN tunnels does Proton use?
Proton VPN is one of the highest-rated VPN providers because we offer fast, stable, and secure VPN tunnels for our community. We originally developed Proton VPN to provide additional security to the many journalists and activists using our encrypted email service, Proton Mail(новое окно). Today, millions of people around the world depend on Proton VPN to stay safe from surveillance and bypass censorship.
Because so many people rely on our service for their safety, we only use the most secure VPN tunneling protocols.
Depending on your operating system, Proton VPN gives you access to the following VPN protocols:
- Windows: OpenVPN, WireGuard®
- macOS: OpenVPN, IKEv2, WireGuard, and Stealth
- Android: OpenVPN, WireGuard, and Stealth
- iOS/iPadOS: OpenVPN, IKEv2, WireGuard, and Stealth
- Linux: OpenVPN
FAQ
You can set up a VPN tunnel for free by creating a free Proton Account and downloading the Proton VPN app for your device.
A VPN tunnel is a connection between your device and a VPN server that encrypts all your internet traffic as it travels between them. This prevents third parties from seeing your online activity, hides your location from others on the internet, and helps bypass censorship.
Three of the most common VPN tunneling protocols include OpenVPN, IKEv2, and WireGuard. All of these protocols are secure and used by many VPN providers.
A VPN tunnel is just a metaphor for the encryption a VPN uses to conceal your data as it travels between your device and the VPN server. Most internet traffic is visible to others on the network, so third parties, like your internet service provider or government agencies, can see what websites you visit and where you are located. A VPN sets up an encrypted connection that functions like a tunnel, preventing third parties from seeing your data as it travels through it.








