Perfect forward secrecy (PFS) is a cryptographic feature of internet communication protocols that ensures even if a session is compromised, past and future sessions remain secure. It achieves this by using a new and unique private encryption key for each session.
PFS is sometimes known simply as forward secrecy by those uncomfortable with the idea that any cryptographic feature might be “perfect”. It can also be more descriptively referred to as using ephemeral encryption keys.
- Public-key cryptography
- The problem
- How perfect forward secrecy solves this problem
- Perfect forward secrecy explained
- The current state of perfect forward secrecy
- Proton VPN uses PFS
Public-key cryptography
For two computers to securely communicate with each other, they must exchange encryption keys. This creates the problem of how to securely communicate the encryption keys, but this was solved in the 1970s with the development of public-key cryptography (also known as asymmetric cryptography).
With public-key cryptography, the encryption software program generates two keys — a public key and a private key. Together, these are known as a key pair. Data is encrypted with the public key, and can only be decrypted using its matching private key.
This solves the problem of how to send data securely over the internet: You make your public key widely available to anyone who wants it. They encrypt data they wish to send to you with your public key, and only you can decrypt it with your matching private key.
In practice, asymmetric cryptography is very slow compared to more conventional symmetric key cryptography (where the same key is used to encrypt and decrypt the data), and so is mainly used to transfer encryption keys (which are small). The data itself is encrypted using symmetric encryption.
Asymmetric cryptography is at the heart of the TLS key exchange used to secure your connection to HTTPS websites. Without it, you wouldn’t be able to perform online banking, securely pay for stuff on the internet, or enter personal information into an online form.
Learn more about HTTPS(nuova finestra)
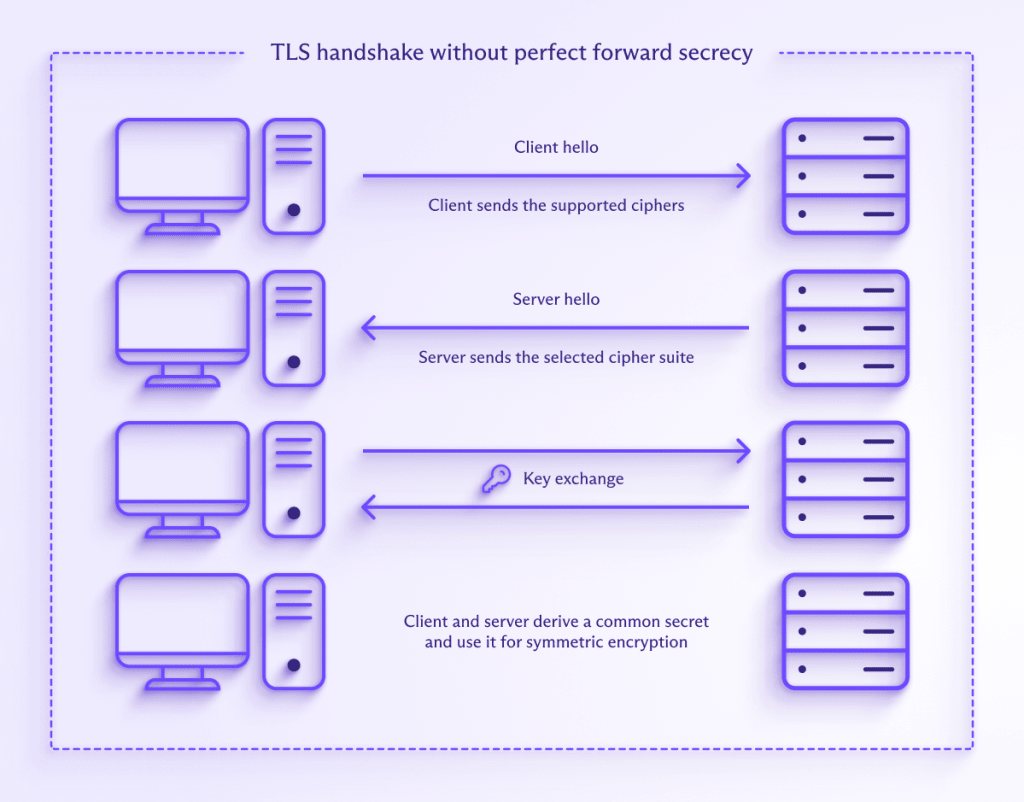
Asymmetric cryptography is also used to establish a secure VPN connection between your device and a VPN server. Like HTTPS, the OpenVPN VPN protocol uses TLS for this. As its name suggests, the Internet Key Exchange (IKE) part of the IPsec/IKEv2 encryption suite handles this for IKEv2 connections.
The problem
This is all great, but there’s a problem. If the same key pair is reused many times and the long-term encryption key (such as the private key of a server) becomes compromised in some way, then an adversary will be able to decrypt all communications that were encrypted using that key pair. All VPN sessions, for example.
This private encryption key therefore becomes a “master key” that can be used to unlock all communications with a server or company.
How perfect forward secrecy solves this problem
The solution is (at least in principle) quite simple — don’t reuse the same key pair for each session. When developers use perfect forward secrecy, the program generates a new and unique key pair for each session. In fact, it’s even possible to regenerate keys within a session (for example, after a specified period of time). When PFS is used, there is no “master key”.
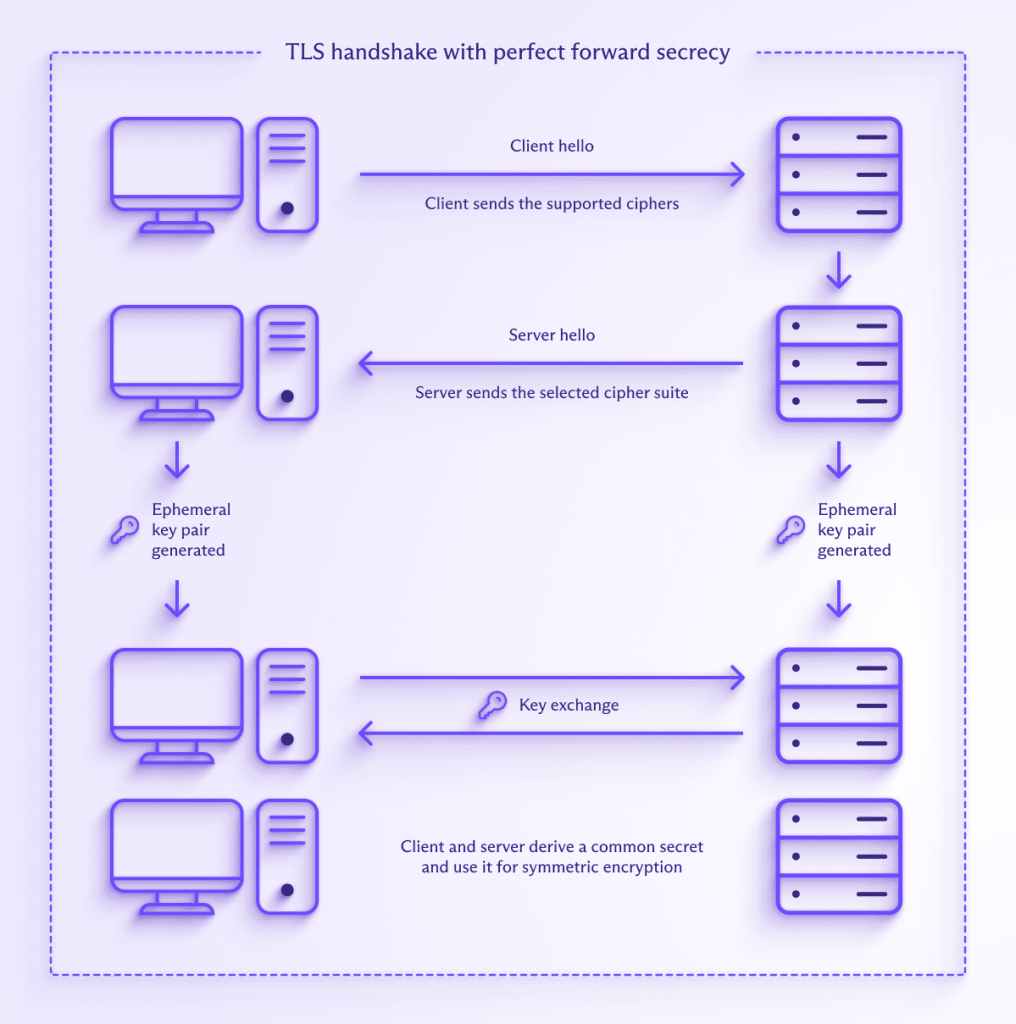
This means that even if a session is compromised in some way, only that session is compromised. Past and future sessions remain secure. Each and every session must be individually compromised, which is a highly arduous and impractical task against modern encryption schemes.
Perfect forward secrecy explained
Although the idea behind PFS is simple, the math required to achieve it is highly complex(nuova finestra). All modern key agreement protocols capable of PFS use a version of Ephemeral Diffie–Hellman(nuova finestra) (DHE) or ephemeral Elliptic Curve Diffie-Hellman(nuova finestra) (ECDH) to generate new keys for each session.
The Diffie-Hellman key exchange is not without controversy. Its re-use of a limited set of prime numbers makes it vulnerable to being cracked(nuova finestra) by a powerful adversary (for example, the NSA(nuova finestra)). This means that a static (non-ephemeral) Diffie-Hellman key exchange isn’t very secure, but it’s fine when ephemeral keys are used (DHE).
ECDH is a newer form of cryptography that uses the properties of a particular type of algebraic curve to encrypt a connection, instead of a large prime number. The different math used allows ECDH to be more secure at any given key length, which makes it much more practical to implement securley.
The current state of perfect forward secrecy
Until 10 years ago, there was a pervading complacency across the technology industry about the need to secure TLS and other internet connections with PFS.
However, the release of documents by Edwards Snowden in 2013 exposed the breathtaking scale, scope, and sophistication of the NSA and GCHQ’s mass surveillance programs(nuova finestra). One of the most shocking revelations was that the NSA adopted a “collect it all” policy(nuova finestra) — storing vast amounts of encrypted communication data that it could not currently access, but which it hoped to be able to mass-decrypt and access at some future point in time.
This was followed just a year later by the discovery of the Heartbleed bug(nuova finestra), which could be used to compromise almost all HTTPS connections in the world. Although now fixed, doing so was hugely expensive and multiple major data breaches occurred before any fix was implemented.
In both cases, the use of perfect forward secrecy would have severely mitigated the amount of damage done. Companies across the globe have since scrambled to implement forward secrecy on their servers to secure the privacy and security of their users.
Final thoughts
Perfect forward secrecy is an essential component of any secure communications over the internet. Thankfully, its use is now routine.
Proton VPN uses perfect forward secrecy to secure all connections to our VPN servers. For example, the cipher suite used by our apps for OpenVPN includes a DHE key exchange, while WireGuard® (and Stealth) uses ECDH with the Curve25519(nuova finestra) elliptic curve(nuova finestra).
To try out a VPN service that uses only the strongest VPN protocols(nuova finestra), with strong encryption(nuova finestra) settings, and perfect forward secrecy, you can download Proton VPN for free.







