IP allowlisting is a security mechanism that restricts access to networks, systems, or applications based on approved IP addresses. Only IP addresses on the allowlist are permitted to connect, while all others are denied access. This method is typically employed by IT administrators to enhance an organization’s network security by allowing only trusted IP addresses to interact with the organization’s resources.
While this has long been known as IP whitelisting, we prefer the term allowlisting, as it’s more descriptive and culturally neutral. As we’ll discuss later in this article, Proton VPN for Businesses customers can secure company their company’s IT resources by allowlisting (whitelisting) the IP addresses of dedicated VPN servers that can be accessed by authorized personnel only.
In this article, we’ll look at:
- What is an IP address?
- How does IP allowlisting work
- Advantages of IP allowlisting
- Disadvantages of IP allowlisting
- Proton VPN dedicated IPs
What is an IP address?
An Internet Protocol (IP) address is a computer-friendly numerical label that uniquely identifies every device that connects to the internet (so if you connect to the internet using a WiFi connection, your IP address will be that of the modem/router you’re connecting to over WiFi, rather than your device itself).
IP addresses work much like postal addresses, allowing data packets to reach their correct destination.
With regard to IP allowlisting (IP whitelisting), the first of these functions is most relevant — uniquely identifying an internet connection. IP addresses are usually assigned by your internet service provider (ISP).
How does IP alowlisting work?
IP allowlisting (IP whitelisting) is the practice of only allowing specific IP addresses to connect to a company IT resource, such as a gateway server that controls access to an office local area network (LAN), or an online software as a service (SaaS) platform. All other connections are refused.
It’s the mirror of blocklisting (also known as blacklisting), which allows connections from any IP address that hasn’t been specifically blocked. Examples of how IP allowlisting is used to improve businesses security include:
- Remote access: Limiting VPN or remote desktop access to specific IP addresses ensures that only known and trusted devices can connect to your company resources.
- Web applications: Restricting access to administrative interfaces or APIs to a set of known IP addresses helps to prevent unauthorized access.
- Database servers: Ensuring that only application servers within a specified IP range can connect to the database server reduces the risk of data breaches.
- Email servers: Allowing email relaying only from specific IP addresses helps to prevent unauthorized use and reduce spam.
Advantages of IP allowlisting
Businesses use IP allowlisting (IP whitelisting) to improve network and cloud security by restricting access to company resources to only staff members connecting from authorized IP addresses. IP allowlisting offers the following advantages:
Access control
By explicitly defining which IP addresses can connect to a network, server, or application, administrators have precise control over who can access specific resources. This helps ensure that only trusted users or systems have access.
Reduced attack surface
Limiting access to a known set of IP addresses minimizes the number of potential attack vectors. This makes it harder for malicious actors to exploit vulnerabilities, as they first need to bypass the allowlist.
Easy to implement
IP allowlisting is straightforward to implement and configure. Most firewalls, routers, and web servers support IP allowlisting through access control lists(ventana nueva) (ACLs) or similar mechanisms.
Improved monitoring and auditing
With IP allowlisting (IP whitelisting), it becomes easier to monitor and log access attempts. Any access attempt from a non-allowlisted IP can be flagged and investigated, providing valuable data for security audits and incident response.
Compliance
Many industries are subject to regulatory requirements that mandate strict access controls. IP allowlisting can help organizations comply with such regulations by ensuring that only authorized users can access sensitive data or systems.
Protection against DDoS attacks
IP allowlisting can mitigate the risk of distributed denial-of-service(ventana nueva) (DDoS) attacks by allowing only legitimate traffic from allowlisted IPs. This helps to maintain the availability and performance of critical services.
Improved network performance
By restricting access to a limited set of IP addresses, network traffic can be more efficiently managed and filtered, potentially improving overall network performance.
Cost-effective
Compared to other security measures, IP allowlisting (IP whitelisting) is a cost-effective way to add an additional layer of security. It doesn’t require expensive hardware or software and can be managed with existing network infrastructure.
Scalability
IP allowlisting can be easily scaled to accommodate growing networks. New IP addresses can be added to the whitelist as needed, ensuring that legitimate users continue to have access while maintaining security.
Disadvantages of IP allowlisting
Although it offers some clear security advantages, traditional IP allowlisting (IP whitelisting) measures do have some potential drawbacks. However, as we’ll discuss below, many of these disadvantages can be overcome using Proton VPN for Business dedicated IP addresses.
Maintenance overhead
Maintaining an up-to-date allowlist can be time-consuming and labor-intensive. As users’ IP addresses change (especially if they use dynamic IP addresses), the whitelist must be regularly updated to reflect these changes.
Limited flexibility
IP allowlisting (IP whitelisting) can be restrictive for users who need to access resources from multiple locations, such as remote workers, mobile users, or employees who travel frequently. Each new location may require an update to the whitelist.
Scalability
The ability to add IP addresses to the allowlist as needed can be an advantage, but as the number of users or IP addresses that need to be allowlisted grows, managing the allowlist can become cumbersome. This is especially challenging in large organizations with many users and devices.
Difficulty with dynamic IP addresses
Many people, especially those using residential ISPs, have dynamic IP addresses that can change. This necessitates constant updates to the allowlist, which can be impractical and error-prone.
Configuration errors
Manually managing an allowlist increases the risk of configuration errors. Mistakenly excluding a legitimate IP address can prevent your team from accessing necessary resources, while mistakenly including an unauthorized IP address can create security vulnerabilities.
Limited protection
IP allowlisting (allowlisting) only controls access based on IP addresses. It does not protect against threats that originate from allowlisted IPs, such as compromised devices or insider threats. Additional security measures are necessary to address these risks.
Usability challenges
For end-users, IP allowlisting can create usability challenges. Legitimate users might be blocked if their IP address changes or if they attempt to access resources from a non-allowlisted location. This can lead to frustration and hinder productivity.
Travel
Users who need to access resources while traveling internationally may face access issues due to IP address changes. Updating the allowlist to include new international IP addresses can be slow and difficult.
Added network complexity
Implementing IP allowlisting can add complexity to network configuration and management. Network administrators must carefully plan and implement allowlisting rules, which can complicate troubleshooting and network design.
False sense of security
Relying solely on IP allowlisting (IP whitelisting) might give a false sense of security. While it does provide an additional layer of defense, it should be part of a broader, multi-layered security strategy that includes firewalls, encryption, authentication, and other security measures.
Proton VPN dedicated IPs
A robust solution to many of the above disadvantages is to rent dedicated servers with fixed IP addresses from Proton VPN. These are VPN servers that only your authorized staff have access to. You then allowlist only the IP addresses of these servers, allowing your staff to have secure segmented access to your businesses office LANs, and SaaS, CaaS, PaaS, and IaaS(ventana nueva) resources.
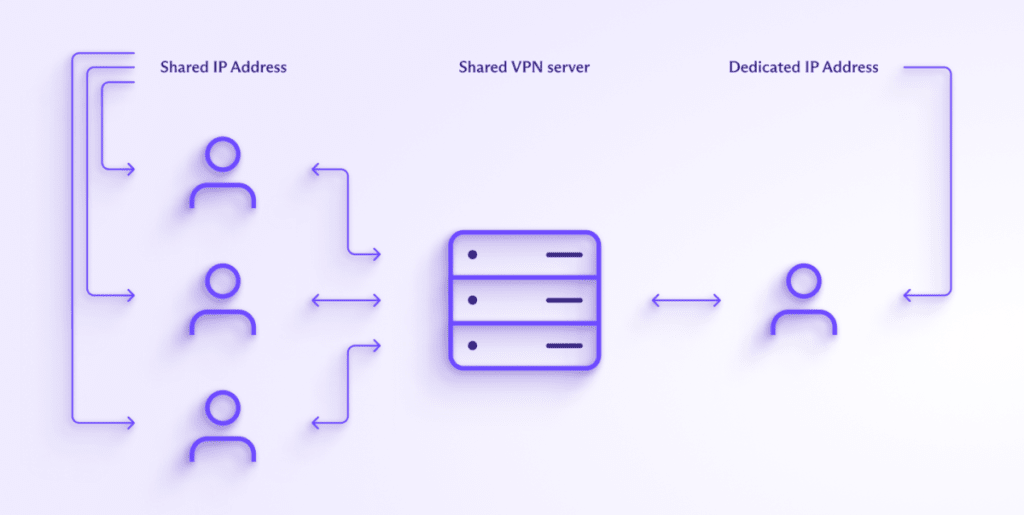
Learn more about dedicated servers and IP addresses
Doing this addresses many (if not all) drawbacks associated with more traditional IP allowlisting approaches.
Easy maintenance and configuration
All your company needs to do is allowlist the IP addresses of any dedicated servers you have leased from us. This also allows for segmented access to your different IT resources, as you can allowlist dedicated IPs for some resources, but not others.
For example, you might manage a company that leases three dedicated server addresses from Proton VPN. All staff members can use server #1 to access commonly used company IT resources such as your CRM and collaboration platforms. Only some staff members can use server #2, which provides need-to-know access to specific company resources, and only senior staff members can access server #3, allowing them to see staff management tools and other sensitive resources.
Note that access to dedicated Proton VPN servers is secure anyway, with full support for two-factor authentication (2FA) via a mobile authenticator app or security key. But allowlisting IPs in this way provides an additional layer of security.
Proton VPN for Business also supports single sign on (SSO), making it easy for your staff to securely connect to the company IT resources they need.
Security you can trust
Proton VPN is trusted by millions of businesses, journalists, activists, and ordinary people around the world to keep them private and secure on the internet. It’s what we do. We use only the strongest VPN protocols with their best encryption algorithms to ensure the connection between your staff members’ devices and our VPN servers can’t be compromised, and continually monitor our bare metal servers with full disk encryption for potential issues.
Your staff can use 2FA to securely access your dedicated gateways, and our NetShield Ad-blocker feature can help keep your devices free from becoming compromised by malware.
Access from anywhere
Because you need only allowlist the IPs of your dedicated VPN servers, it doesn’t matter if your staff work remotely or are traveling. As long as they are authorized to sign in to your dedicated servers, they’ll be able to access the resources they need from anywhere in the world, and no matter if their own IP address changes.
Learn how to use IP allowlisting to secure your IT resources
Final thoughts:
IP allowlisting (IP whitelisting) can be a valuable security tool, but it’s important to be aware of the limitations of traditional IP allowlisting methods, and to implement it only as part of a comprehensive security strategy that addresses a range of potential threats and challenges.
However, IP allowlisting Proton VPN for Business dedicated servers provides an additional layer of security for your company’s physical and online resources, offering a flexible and modern security solution without the downsides of more traditional IP allowlisting.







