DNS translates human-friendly domain names to computer-friendly IP addresses. Private DNS encrypts DNS queries made by your device to a DNS server. When used with a third-party DNS service that respects your privacy, private DNS can improve your online privacy. However, private DNS isn’t needed when using a VPN, and can actually make your VPN connection less secure.
In this article, we look at what private DNS is, how it can help protect your privacy, and how to enable it on your device, but also why you shouldn’t use it with VPN.
- What is DNS?
- Why DNS poses a privacy problem
- What is private DNS mode?
- Private DNS protocols
- Private DNS is not as private as a VPN
- Don’t use private DNS and a VPN together
- How to use private DNS
What is DNS?
The Domain Name System (DNS) maps human-friendly domain names to their corresponding computer-friendly numerical IP addresses.
For example, the Proton VPN website uses the domain name protonvpn.com, which corresponds to the IP address 185.159.159.140. When you type www.protonvpn.com into your browser’s URL bar, the domain name must be converted to its corresponding IP address for computers to understand it.
This conversion process is usually performed by special DNS servers run by your internet service provider (ISP).
Why DNS poses a privacy and censorship problem
Whoever resolves your DNS queries can see which websites you visit (but not what you do on them). Unless you use a VPN or actively change your DNS settings, it’ll be your ISP that resolves your DNS queries.
It’s important to understand that, by default, your ISP can monitor what you do online, even when it doesn’t resolve your DNS queries. However, this is the easiest (and therefore cheapest) way for them to log your browsing history.
Most ISPs that log their customers’ browsing history (which is most ISPs), therefore take the path of least resistance, and confine themselves to logging customers’ DNS records. In most jurisdictions, this minimal level of logging allows ISPs to meet any legal obligations they have to log users’ browsing histories.
Similarly, when governments wish to censor internet content on social, religious, political, or “moral” grounds, they ask domestic ISPs to enforce these blocks. And the easiest way to do this is to block DNS queries to specified websites and apps. Using an international third party DNS resolver can bypass these simple (yet effective) censorship blocks

Graffiti in Istanbul, encouraging people to use Google DNS servers to bypass a 2014 government censorship crackdown(yeni pencere)
What is private DNS mode?
Unlike most connections to websites, which are protected by HTTPS(yeni pencere), DNS queries are usually sent in unencrypted plaintext. This means anyone with access to the DNS queries (such as your ISP) can read them, even if they’re resolved by a third party.
If an ISP were to make extra effort to spy on its customers (as it might be required to do by a more restrictive government), it could simply monitor and log the DNS queries to third-party resolvers. Using more sophisticated technology, it could also implement censorship by filtering these queries.
Private DNS prevents this by encrypting your DNS queries as they travel between your device and a third-party DNS server. This ensures that your ISP (or anyone else monitoring your internet connection) can’t see your DNS queries.
Private DNS therefore represent a significant improvement in DNS privacy and security over traditional unencrypted DNS queries. However, it also has several limitations that we’ll discuss later.
Private DNS protocols
Private DNS is achieved using one of three security protocols: DNS-over-TLS (DoT), DNS-over-HTTPS (DoH), and DNSCrypt.
DNS-over-TLS
DoT encrypts DNS queries using the Transport Layer Security(yeni pencere) (TLS) protocol, ensuring the data can’t be easily intercepted or altered. DoT runs over port 853, making it easier for networks to block or monitor DoT traffic specifically, as it doesn’t blend in with other types of traffic.
This makes DoT the preferred choice on networks that wish to have some control over the traffic passing through them. DoT is also less complex to implement at the server level than DoH.
DNS-over-HTTPS
DoH uses HTTPS, the protocol that secures all sensitive information on the internet, to encrypt DNS queries. Like DoT, DoH uses TLS to encrypt the DNS queries, but DoH connections are run over port 443 so they’re mixed with regular HTTPS web traffic. This makes it difficult for observers to distinguish DNS traffic from other types of web traffic, making DoH more private and censorship-resistant than DoT.
Learn more about HTTPS(yeni pencere)
DNSCrypt
The oldest private DNS protocol, DNSCrypt, is very similar to DoH, but with some additional features that improve on DoH. However, DNSCrypt is not widely supported by operating systems and browsers, and therefore requires running third-party software(yeni pencere).
So which is best? All these private DNS protocols offer huge privacy and security improvements over not using private DNS at all, and have negligible impact on your browsing speeds. There are legitimate reasons for some networks to prefer DoT, but for most end-users, the greater privacy that DoH offers makes it the better option of the two.
In many ways, and despite being the oldest option, DNSCrypt is still the best option in terms of privacy. However, lack of support across the DNS ecosystem limits its appeal. For the rest of this article, we’re going to concentrate on DoT and DoH, as these protocols don’t require you to download additional software.
Private DNS is not as private as a VPN
Private DNS offers some privacy advantages, but these only work when ISPs (often at the behest of governments) pick low-hanging fruit and don’t put much real effort into censoring content or spying on you. Although it requires extra effort, an ISP can trace your connections to determine your browsing history, and can directly block traffic to specific IP addresses.
To prevent an ISP from being able to see what you do online (and therefore potentially censor it), you should use a VPN. This encrypts your connection between your device and the VPN server, so that your ISP can’t see the contents of your data. DNS queries are routed through the encrypted connection (also known as a VPN tunnel) to be resolved by your VPN provider, so your ISP can’t know which websites or other resources you visit on the internet.
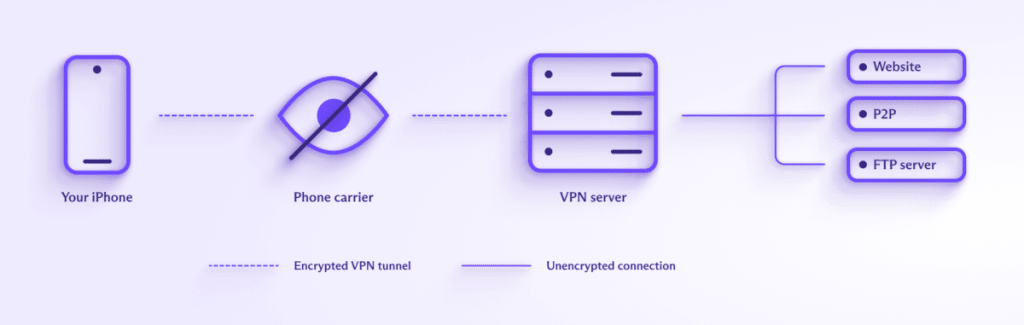
Similarly, websites you visit can’t see your real IP address. All they can see is the IP address of the VPN server.
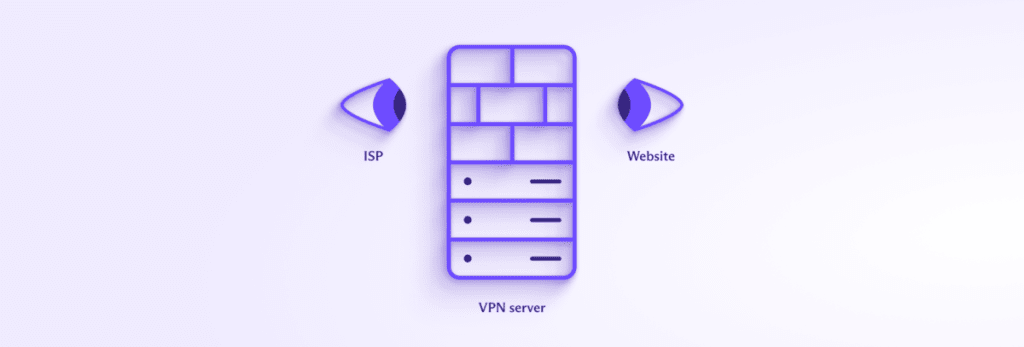
A VPN therefore provides much more privacy than a private DNS service.
Don’t use private DNS and a VPN together
All good VPN providers operate their own DNS servers. When using a VPN, DNS requests are routed through the VPN tunnel and resolved by the VPN service. As the VPN tunnel is encrypted, the DNS requests are encrypted without the need for a private DNS protocol.
Furthermore, configuring any third-party DNS service on your system makes it more likely DNS requests will be routed outside the VPN tunnel. Private DNS increases the chances of this happening, because encrypting the DNS queries makes it harder for the DNS protection measures used by the VPN software to ensure they’re properly routed through the VPN tunnel.
So not only is private DNS not needed when using a VPN, it can cause a DNS leak.
How to use private DNS
To use private DNS, you must first select a DNS resolver that supports either DoT or DoH (it’s also possible to self-host a DNS server, but this requires serious technical chops). Popular DNS services that support private DNS and which pay at least lip service to privacy, include:
- Cloudflare 1.1.1.1 — This large commercial DNS service only collects “anonymized DNS query data sent to the Cloudflare Resolver”. Cloudflare supports DoT and DoH.
- Quad9 — A not-for-profit DNS service which collects no personally identifiable information about its users. Importantly, the IP addresses of users are not stored when making a query. Quad9 supports DoH.
- OpenNIC — Billing itself as a decentralized, open, uncensored, and democratic DNS provider, OpenNIC is a collection of volunteer-run DNS servers located around the world. Unlike most DNS services, where a single DNS address (such as 1.1.1.1) will connect you to the network of DNS servers, with OpenNIC, you select an individual DNS server to connect to. Logging policies, and whether private DNS is supported (often in the form of the older DNSCrypt protocol), depends entirely on whoever runs the DNS server you choose.
Once you’ve chosen a DNS provider, you have two options. You can configure your operating system (OS) to route all DNS queries to your chosen provider, or you can configure just your browser to use a private DNS service.
All modern operating systems support DoT or DoH (or both), as do all modern browsers. By default, Firefox automatically connects to Cloudflare 1.1.1.1 servers using DoH.
Final thoughts on Private DNS
Private DNS is much more private, secure, and censorship-resistant than regular unencrypted DNS, and at least some DNS providers care a lot more about your privacy than your ISP does. So if you don’t use a VPN, you should configure your system or browser to use a trustworthy DNS service that supports private DNS.
However, a VPN provides much more privacy and is much more effective at defeating censorship than using private DNS. Just be aware that you shouldn’t (and don’t need to) use private DNS when using a VPN.







