Freenet is a decentralized, encrypted, open-source dark web designed to let you communicate with others, upload and download content, and access online information anonymously.
Learn more about the different dark webs(yeni pencere)
- What’s in a name?
- What is Hyphanet?
- Opennet and darknet
- Is Hyphanet safe?
- How to install Hyphanet
- How to use Hyphanet
- Final thoughts
What’s in a name?
The original Freenet project dates back to 1999, but recently (March 2023) changed its name to Hyphanet. This is because Ian Clarke(yeni pencere), creator of the original Freenet, has started to develop “a successor to Freenet” with “different design priorities”.
This new dark web platform was code-named Locutus, but in mid-2023, the board of Freenet Project, Inc., a non-profit organization that has managed Freenet since 1999, decided to rename the Locutus project to Freenet 2023.
In response, the Freenet community changed the name of the original Freenet to Hyphanet (a reference to underground mycorrhizal fungal networks(yeni pencere)).
At the time of writing this article, Freenet 2023 remains firmly at the development stage. An alpha version is available for developers to experiment with, but it isn’t available for general use. This article will therefore focus on Hyphanet.
What is Hyphanet?
Freenet started as a student project by Ian Clarke. This resulted in the widely acclaimed 2001 paper, Freenet: A Distributed Anonymous Information Storage and Retrieval System(yeni pencere), which became one of the most frequently cited computer science articles in 2002.
Unlike other dark web technologies such as Tor and I2P, it’s a pure dark web in that it provides no access to the regular internet. Strictly speaking, it’s a fully distributed, peer-to-peer, anonymous publishing network that offers secure data storage.
When you join the Hyphanet network, you agree to share a percentage of your local disk space. This space (referred to as a datastore) is securely encrypted, and other Hyphanet members download parts of files from it (similar to BitTorrent).
However, on top of this basic file-hosting framework, volunteers have developed applications that allow for websites, message boards, and more. A limitation of this system is that websites can’t be dynamic (so they’re always simple static HTML pages).
An advantage is that web pages (and other data) can be available long after the original host has disappeared. However, if no one accesses data for a long time, it can disappear (this works much like BitTorrent, where files that aren’t actively seeded become de-indexed over time).
Opennet and darknet
Since 2007, Freenet has offered two “modes” — opennet and darknet. These terms can be somewhat confusing because Freenet’s definitions don’t align with how the public generally understands these terms.
If you use Hyphanet in opennnet mode, you connect to random peers. As such, openenet mode is similar to Tor Onion Services in many ways. If you use it in darknet mode, you only connect to trusted friends who you’ve previously exchanged public keys and node references with.
It’s these darknets that make Freenet uniquely secure, as it completely blocks outside access to data shared within a darknet group.
Is Hyphanet safe?
When setting up Hyphanet, you must configure an encrypted datastore on your local disk. This datastore stores fragments of files that other Hyphanet users have uploaded, and you have little or no control over what’s stored there. This prevents Hyphanet users from censoring content by deleting files in their datastore.
The encryption Hyphanet uses makes it “hard, but not impossible” to determine which files are stored in your local datastore and serves primarily to provide plausible deniability(yeni pencere) about the nature of the material stored on your local disk.
Hyphanet was designed to protect the anonymity of those who “insert” (upload) content into the network and “request” (download) it. As with Tor and I2P, you always connect to data stored on Hyphanet indirectly, with your connection first routed through several other nodes in the Hyphanet network.
Hyphanet bundles packets together and routes them through a varying number of nodes to confuse timing attacks.
Can Hyphanet be compromised?
There are a number(yeni pencere) of reports(yeni pencere) of law enforcement agencies successfully tracking down Freenet/Hyphanet users, but none of these contain any technical details and have been disputed(yeni pencere).
A 2017 paper titled Statistical Detection of Downloaders in Freenet(yeni pencere) claims to have developed “a passive technique for detecting Freenet downloaders”. But again, this claim is disputed(yeni pencere).
How to install Hyphanet
Hyphanet is available as a Windows .exe, Debian .deb, and Gentoo package. You can also install it on macOS or any Linux system as a .jar file (which requires installing Java).
The installation wizard does a good job of guiding you through the setup and then launches the Hyphanet portal in a tab on your default browser. However, you’re strongly advised to run Hyphanet with your browser in Private or Incognito mode(yeni pencere), so it’s a good idea to copy the local Hyphanet URL, restart your browser in Private or Incognito mode, and then paste the URL.
The Hyphanet installer also offers to install desktop and menu icons on your system to make accessing Hyphanet easy.
How to use Hyphanet
Unlike with I2P, Hyphanet doesn’t require you to manually configure your browser’s proxy(yeni pencere) settings. And unlike either I2P or Tor, its main screen provides a host of useful links to get you started, including an index of Hyphanet websites, a search engine, extensive documentation, developer blogs, plus various email, messaging, and chat tools.
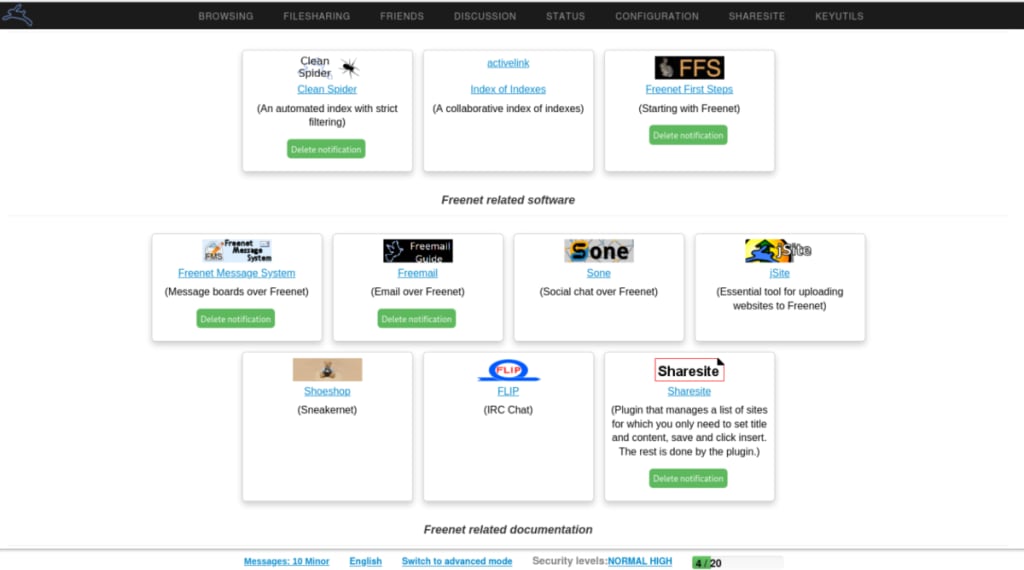
As noted, all web pages are static HTML, which prevents trackers and other privacy-invasive scripts from being embedded. These take from a few seconds to around a minute to download (in this reviewer’s experience), which is much faster than I2P pages (again, in this reviewer’s experience).
Many of the utilities available on Hyphanet require the Web of Trust plugin. This attempts to reduce spam and address the fact that anyone can insert content into the Hyphanet network by providing you a cryptographically provable identity with a score value that other community members can assign positive or negative ratings to.
Final thoughts
With no access to the regular internet, a big problem with Hyphanet in opennet mode is that most content is either pointless (“Hi there!”) or illicit in some way. However, its indexes, such as The Filtered Index featured on Hyphanet’s front page, do provide links to potentially more interesting (and savory) content.
When compared with other dark webs, Hyphanet will always be a niche alternative to Tor Onion Services. However, it is faster than I2P, and a much greater proportion of its links actually work.
Of course, what really sets Hyphanet apart from other dark webs is the ability to create closed darknets with like-minded people that are almost impossible to detect.
Because of their closed nature, it’s impossible to know how many people actually use these darknets or to provide any other kind of objective assessment about them. But that’s rather the point.







