VPNs are useful for many things, and when used properly, can protect you from being tracked in several ways:
- Websites can’t track you using your real IP address
- Your internet service provider (ISP) can’t track what you do on the internet
- Your government can’t track what you do on the internet via your ISP
- P2P peers can’t track you by your IP address
This means a VPN can prevent you from being tracked online in various ways, but it’s also important to understand the specific situations when a VPN can’t protect you so you can make informed decisions about your online privacy.
Learn about the VPN threat model(新しいウィンドウ)
- How a VPN works
- Can websites track you when using a VPN?
- Can your ISP track you when using a VPN?
- Can your government track you when using a VPN?
- Can P2P peers track you when using a VPN?
- Can your VPN provider track you when using a VPN?
- Can the police track you when using a VPN?
- Can your employer track you when using a VPN?
- Can Google track you when using a VPN?
- Can you be tracked when using public WiFi?
- Can someone tell if you’re using a VPN?
- Can you be tracked if the VPN disconnects?
- What is the best VPN to prevent tracking?
How a VPN works
A VPN connects your device to a VPN server run by a VPN service such as Proton VPN. The connection between your device and the VPN server is encrypted, so no one can access your data as it travels between the two computers.
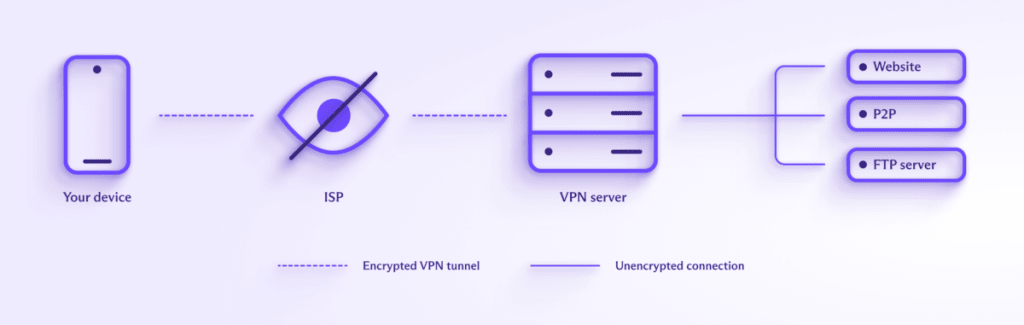
As we shall see, this deceptively simple setup has important consequences.
Learn more about how VPNs work
Can websites track you when using a VPN?
Not directly. Usually, when you visit a website, that website (or other internet resources, such as games or FTP servers) can see your device’s IP address. This uniquely identifies your internet connection and gives the website a good idea of where you’re geographically located (down to the city level).
Armed with your IP address, it‘s easy for cross-website platforms to track the websites you visit on the internet. Using a VPN prevents websites from seeing your real IP address. Instead, they see the IP address of the VPN server.
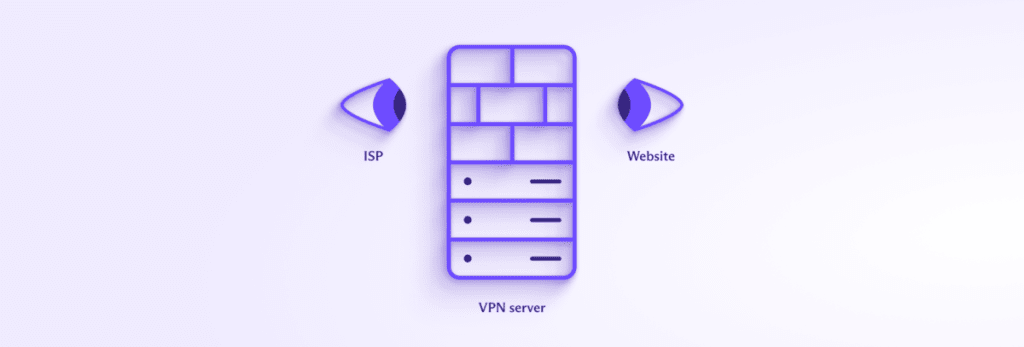
Using a VPN prevents the most simple and intrusive way for websites to track you. However, in response to technologies such as VPNs, websites have developed other ways to uniquely identify and track what you do online. These include:
Cookies
These are small text files that are stored on your browser when you visit a website. First-party cookies(新しいウィンドウ) are sent by the websites you actually visit and are used for legitimate purposes, like remembering that you’re logged in, your preferences, and other useful things.
However, many websites also load third-party cookies from advertising and analytics companies onto your browser that track what you do on the internet so that you can be targeted with privacy-invading ads.
Fingerprinting
Browser and device fingerprinting use minor differences between browsers or devices to uniquely identify and track you.
Learn more about browser and device fingerprinting(新しいウィンドウ)
Other sneaky ways websites track you include HTTP E-Tags(新しいウィンドウ), web (or DOM) storage(新しいウィンドウ), and browser history sniffing(新しいウィンドウ).
A VPN can’t prevent tracking using cookies, fingerprinting, and other similar techniques, but they’re not as invasive to your privacy as tracking you by your IP address and are much less reliable as a means of identifying you.
While these other methods can identify your browser or device as you visit different websites, your browser or device isn’t directly tied to your real identity in the same way that your IP address usually is.
Although a VPN can’t prevent cookies, the Proton VPN app has a DNS filtering feature called NetShield Ad-blocker. This can prevent tracking cookies and other malicious scripts from passing information back to whoever controls them, greatly reducing their ability to track you.
Learn more about NetShield Ad-blocker
Can your ISP track you when using a VPN?
No. Your data is encrypted, so your ISP can’t see its contents. This includes DNS requests, which are sent through the VPN tunnel and resolved by the VPN provider.
Your ISP can see the IP address of the VPN server you’re connected to, but it can’t see any connections made after that. So it can’t see which websites you visit or anything else you do on the internet.
Can your government track you when using a VPN?
Many governments collect large amounts of browsing data on their citizens and, as Edward Snowden’s 2013 revelations(新しいウィンドウ) showed, on citizens of other countries as well. The easiest way to do this is to require ISPs to log their customers’ online activity in a way that governments can access.
For example, almost all countries in the European Union have transposed the 2006 Data Retention Directive(新しいウィンドウ) (DDR) into local law. The DDR itself was declared invalid by the Court of Justice of the European Union in 2014 on human rights grounds, but no country has removed local implementation of the law from their statute books.
The UK’s Investigatory Powers Act 2016(新しいウィンドウ) (nicknamed the “Snoopers Charter”) can require ISPs to store customers’ browsing histories for 12 months, and the government has started trials(新しいウィンドウ) into making this a reality.
In the United States, there is no blanket data retention law requiring ISPs to keep logs, but the government can issue individual ISPs with national security letters(新しいウィンドウ) (NSLs) requiring their cooperation.
NSLs are almost always accompanied by gag orders(新しいウィンドウ), so it’s unclear how many ISPs in the US have been served with one. Following Snowden’s revelations about the scale and comprehensiveness of the NSA’s mass surveillance operations, it seems likely that most, if not all, ISPs have been targeted.
Using a VPN prevents your ISP from seeing what you do on the internet, making it an effective way to stop untargeted mass surveillance by governments.
However, a VPN won’t protect you against targeted attacks. For example, the NSA’s Computer Network Operations(新しいウィンドウ) unit (formerly Tailored Access Operations) uses a wide variety of “hands-on” surveillance techniques(新しいウィンドウ), such as breaking into targets’ houses to physically access devices or compromise their routers. They’ve even interrupted supply chains to infect software and hardware with spyware.
Using a VPN won’t protect you against targeted tracking of this kind.
Can P2P peers track you when using a VPN?
No. Usually, it’s very easy for BitTorrent users sharing the same files as you (your “peers”) to see your real IP address. The whole point of BitTorrent is to allow you to share files directly with other users without the need for an intermediary.

However, much like websites, when using a VPN, peers will see the IP address of the VPN server you’re connected to, not your real IP address.
Can your VPN provider track you when using a VPN?
Yes. Your VPN provider knows your real IP address, resolves your DNS queries, can see which websites you visit, and likely has your payment details. For these reasons, you must choose a VPN service you can trust.
Most VPN services claim to keep no logs of what you do online. For reputable VPN services, this means all records of your internet history are deleted and can’t be tracked. Many countries legally require VPN services to keep logs, so reputable no-logs VPN providers are based in countries without such legal requirements.
However, in most countries, VPN providers can be legally required to start keeping logs of individual users’ internet history when issued with a valid court order or similar legally-binding demand.
Proton VPN is based in Switzerland, where strong privacy laws not only mean there is no legal requirement for us to keep logs, but we also can’t be required to start logging. Additionally, our no-logs policy was recently confirmed by an external audit by the security firm Securitum.
Can the police track you when using a VPN?
Maybe. If police monitor a website, they’ll know the IP address you accessed it from. If you’re using a VPN, then they’ll see the IP address of the VPN server, which will let them find the VPN service you’re using.
A reputable no-logs VPN service will be unable to provide the police with your browsing history, but they can be legally required to start logging your internet activity in most jurisdictions. Also, most countries have formal arrangements that allow overseas police forces to request legal assistance outside of their direct jurisdiction.
Can your employer track you when using a VPN?
Probably. If you’re using a business VPN, your company can likely monitor every website you visit (or even which individual web pages you visit if the website doesn’t use HTTPS).
If you’re using a commercial VPN service (such as Proton VPN), your employer won’t be able to monitor your otherwise unencrypted internet traffic. A VPN will also allow you to bypass censorship blocks put into place on your work internet network (although you may face disciplinary measures if you’re caught evading these).
If your employer owns or controls the hardware you use, they may also have installed monitoring software to track everything you do online. A VPN can’t overcome a compromised device.
Can Google track you when using a VPN?
It depends. If you’re logged in to your Google account when using any Google service, Google will be able to monitor all aspects of your browsing (except for your current IP address). You can ask Google to delete your historic web activity and to stop recording new web activity(新しいウィンドウ), but this requires trusting Google(新しいウィンドウ).
If you’re using a VPN and not logged in to your Google account, Google will know significantly less about you. As with any other website, Google websites won’t be able to track you directly using your IP address, although it may use other methods. It’s probably a good idea to avoid using the Chrome browser(新しいウィンドウ) if you don’t want to be tracked by Google.
Learn which browsers respect your privacy(新しいウィンドウ)
Can you be tracked when using public WiFi?
No. A VPN prevents criminals who use WiFi sniffing, evil twin hotspots, and other hacking techniques from accessing your data when you use public WiFi. A VPN also prevents WiFi hotspot hosts from tracking what you do online, which is important since many are commercial businesses that monetize their ”free” WiFi by selling your browsing history.
Can someone tell if you’re using a VPN?
Websites and other online services you visit can see the IP address of the VPN server you’re connected to. If they want to, they can check that IP address against lists of known VPN and proxy servers(新しいウィンドウ) to see if you’re using a VPN.
Most websites have little reason to do this, but it’s routine practice for most streaming platforms.
Another way to detect if you’re using a VPN is simply to look at the port number your connection is using. By default, OpenVPN traffic uses UDP port 1194, while IPsec uses UDP port 500.
The best defense against this is to run VPN protocols over TCP port 443. This is the port used by HTTPS, so VPN traffic running over TCP port 443 is hard to tell apart from regular secure internet traffic. Proton VPN supports running both OpenVPN and WireGuard® over TCP port 443.
Governments with advanced censorship systems can also use a variety of deep packet inspection(新しいウィンドウ) (DPI) techniques on internet traffic to detect VPN traffic. Simply running VPN protocols over TCP port 443 isn’t enough to defeat sophisticated DPI systems, but some providers offer advanced obfuscation solutions that can defeat many DPI methods.
A good example is Proton VPN’s Stealth Protocol, which can defeat many advanced VPN detection techniques.
Can you be tracked if the VPN disconnects?
Unlikely. When you’re not connected to a VPN server, your internet traffic gets routed by your ISP in the usual way. However, most VPN services offer VPN apps that include a VPN kill switch.
This prevents your device from connecting to the internet outside the VPN, ensuring that if your VPN connection fails for any reason, your real IP address isn’t exposed, and your ISP won’t be able to track what you do on the internet.
Proton VPN offers a kill switch on all our apps plus a permanent kill switch on our Windows and Linux apps that ensures you never accidentally connect to the internet without the VPN enabled.
What is the best VPN to prevent tracking?
Proton VPN is based in Switzerland, which has some of the strongest data privacy laws in the world. We’re not subject to any legal requirements to log your internet activity, and we can’t be compelled to start logging either.
This is in sharp contrast to most jurisdictions where VPN companies are often based. Our no-logs policy has also been independently audited.
Proton VPN apps can block tracking (plus ads and other malicious scripts) using NetShield Ad-blocker, our DNS filtering feature. In addition to this, all our apps have a kill switch to protect you if the VPN connection drops.
Most of our apps support both the OpenVPN TCP and WireGuard TCP VPN protocols to conceal the fact that a VPN is being used, and our Stealth protocol can hide VPN use against even advanced DPI techniques.
Final thoughts
A VPN is a vital tool that prevents your internet activity from being tracked. It hides your real IP address from websites that you visit and prevents your ISP from knowing what you do online.
Just be aware that digital security is never simple. There are multiple attack vectors you should be aware of, and a VPN can’t protect you against them all.








